Recent research uncovers a new spreading campaign of AsyncRAT, that targets users who download electronic books. The reviewed campaign targets ones who seek for a specific book, originally available as a paid workbook on different platforms. Tricked into clicking on the downloaded file, people in fact trigger malware installation.
AsyncRAT Spreads in Fake eBook Files
The latest spreading campaign of AsyncRAT was described by Gridinsoft analysts. Fraudulent actors publish what originally looks like a downloading link for an archive that contains the desired book. As I’ve mentioned, the specific book that this website offers is not free, so it adds even more to the temptation of a user. After hitting the download button, they see a genuinely looking file, and click it, hoping to open the book.
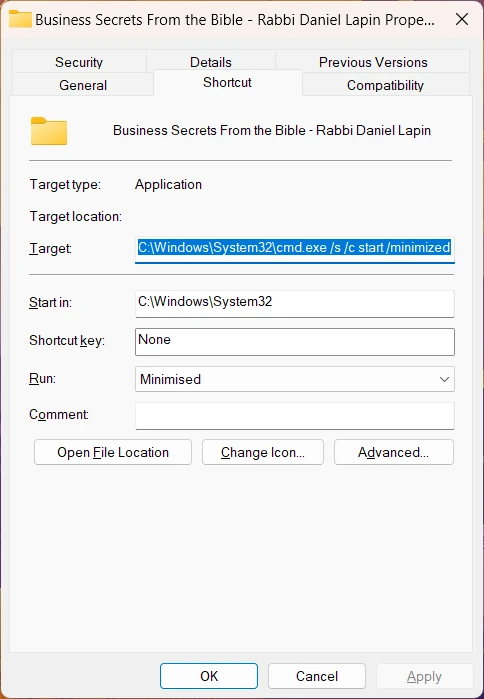
But despite the expectation, nothing will ever happen. This file is only made to look like one of an ebook, and is in fact a disguised compressed file that triggers the chain of malicious events. Shall the user click on it, the file executes its script, launching a multi-stage malware loader. All the resources needed for the attack (except the final payload) are stored in this exact fake ebook file.
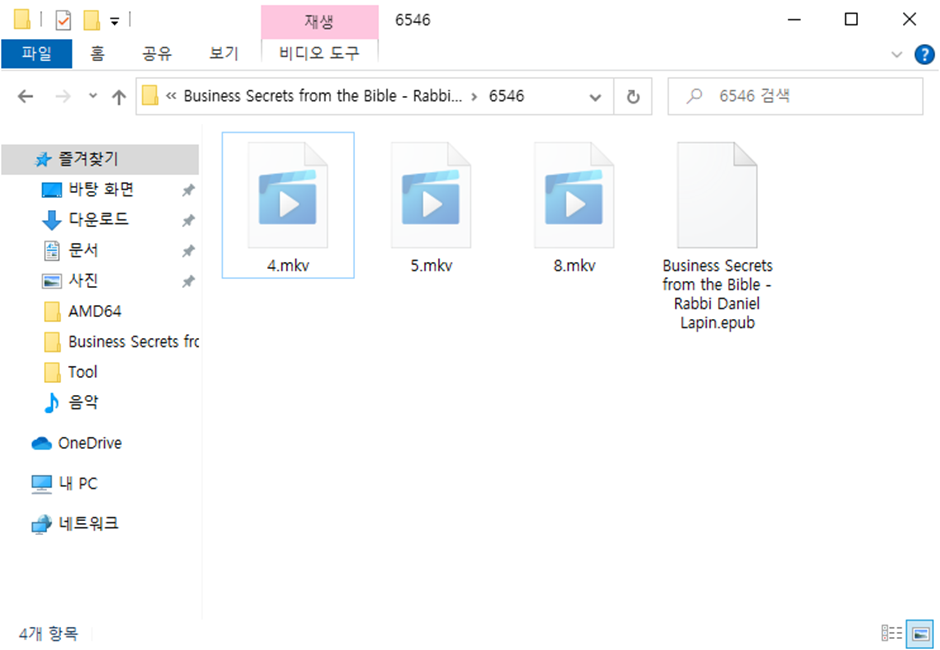
The first thing that is launched is a PowerShell script that initially checks the system for antivirus software. Then, it starts playing with the files in the archive, which only look as video files. In fact, they only have extensions of ones, being a VBS script under the bonnet. This first batch file collects system information and runs another VBS file that eventually downloads AsyncRAT from the command server. The other script creates another task in the Scheduler, and executes the final payload.
What is AsyncRAT?
AsyncRAT is an open-source remote access tool, that originally appeared on public in 2019. For obvious reasons, it is often weaponized by malicious actors. Even in its original design, it is a powerful toolkit for remote access and administration, with the application of encrypted connections during the session. AsyncRAT is capable of logging keystrokes, sending remote commands, controlling the attacked system and deploying malware.
As the source code is freely available, it is nearly impossible to trace a specific cybercrime gang that uses it in their attacks. In fact, AsyncRAT appears in both attacks on individuals and high-profile cyberattacks led by state sponsored actors. Open-source nature also adds to the flexibility of the payload. Functionality, detection evasion, capabilities for other malware delivery – they can alter pretty much anything. This is what makes not only AsyncRAT, but any open-source malware exceptionally dangerous.
How to protect against malware?
To stop the obfuscated malware spreading campaign like the one I’ve described above, I recommend using GridinSoft Anti-Malware. Its multi-component detection system will stop the attack even before the malicious file gets to the system, thanks to its superior online protection module.