Google has disclosed that two Android zero-day security vulnerabilities have been detected in its Pixel smartphones. The patch is already available, as Google claimed fixing the flaws in the recent Pixel Update Bulletin. Even worse news is that the flaw is already under exploitation in targeted attacks.
Two Android Zero-Day Flaws Exploited in Targeted Attacks
In a recent announcement, Google released a statement regarding detecting two zero-day security vulnerabilities in its Pixel smartphones. The first vulnerability, CVE-2024-29745 (CVSS 7.2), is an information disclosure flaw in the bootloader component that could compromise data confidentiality. The other one, CVE-2024-29748, is a privilege escalation flaw in the firmware component that can allow unauthorized access and control over the device.
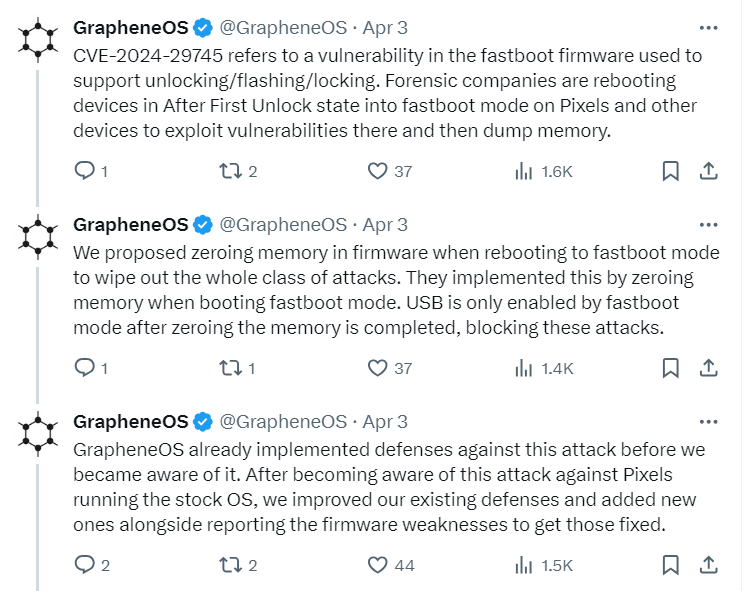
According to Google’s advisory, these vulnerabilities were fixed on April 2, 2024. The original discovery though happened back in early January 2024, by GrapheneOS developers. The good news is that they are subject to limited, targeted exploitation, which means the risk of widespread exploitation is relatively low. Nonetheless, Google urges all Pixel smartphone users to update their devices to the latest software version as soon as possible.
Android Zero-Day Vulnerabilities Exploited in the Wild
Although Google has not provided specifics on the attacks, GrapheneOS developers have indicated active exploitation of this flaw. In addition, CISA has updated its Known Exploited Vulnerabilities Catalog with these vulnerabilities currently being exploited. CVE-2024-29745 is linked to a vulnerability in the fastboot firmware, which supports various device states such as unlocking, flashing, and locking. Threat actors can exploit this flaw to access the devices’ memory without privileges or user interaction.
On the other hand, CVE-2024-29748 presents a different risk. This flaw allows to circumvent the factory reset done by the apps that use device admin API for this. As the result, attackers were able to stop the device from finishing the factory reset, although they need a physical interaction with one. Although Google has addressed a part of the issue, GrapheneOS has pointed out that the reset can still be stopped by cutting power to the device. As a result, GrapheneOS is working on a more comprehensive solution. This includes a stronger duress PIN/password feature and a secure “panic wipe” action that can be executed without requiring a reboot.
Safety Recommendations
As the digital landscape evolves, so does the sophistication of cyber threats. To mitigate these risks, users should manually verify if their devices have the latest software version. Staying informed about security updates and best practices is crucial in safeguarding digital assets against emerging threats. Google’s disclosure serves as a reminder of the ongoing battle for cybersecurity and the need for continuous improvement in defense mechanisms to protect personal information.




