PUABundler:Win32/MediaGet is a Russian potentially unwanted program designed for accessing pirated content. Like most similar software, it installs some unnecessary programs onto the system during installation and also turns the device into a proxy server in exchange for an ad-free experience.
MediaGet Virus Overview
PUABundler:Win32/MediaGet is a detection of potentially unwanted software associated with the program MediaGet, a BitTorrent client with Russian origin. The program was originally positioned as a torrent client, it now functions more like a player for pirated content.
The main problem is that MediaGet installs a range of unwanted programs, which an inexperienced user may struggle to cancel. This is accomplished through the use of tricks, which I’ll talk about later.
Although the program has its own official website, in most cases the user receives it as “recommended software”, bundled with other free programs. Alternatively, they may be recommended to use it on websites that, once again, spread unlicensed software of different kind. Once again: the program is not inherently malicious, it is the additional software it installs that may have undesirable and sometimes malicious properties.
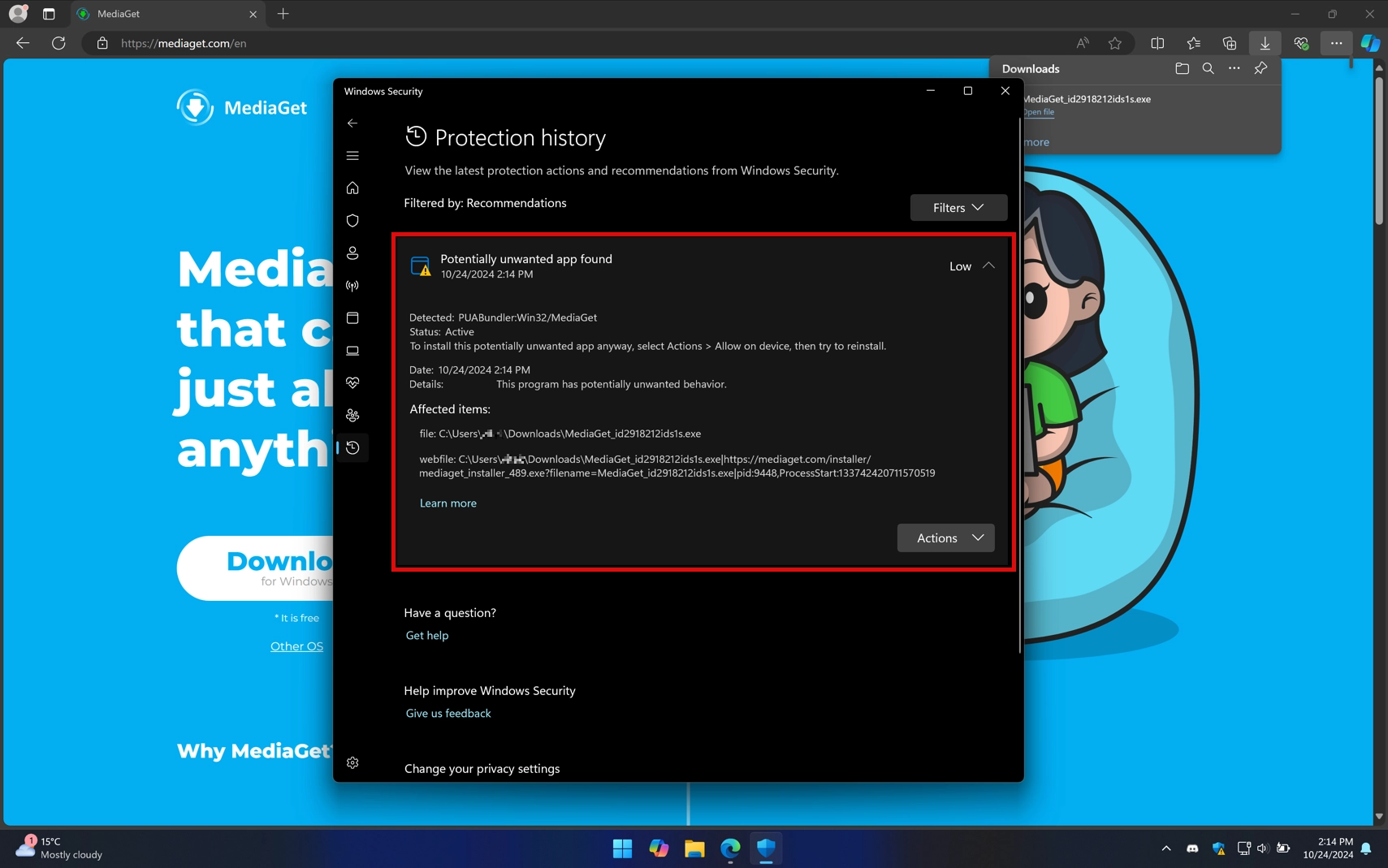
Even if the user uninstalls MediaGet, the additional software is not removed along with it, and some items are not displayed in the list of installed applications, which makes it very difficult to remove them. Because of these factors, the program has received the status of potentially unwanted software and even a separate classifier PUABundler:Win32/MediaGet.
How dangerous is it?
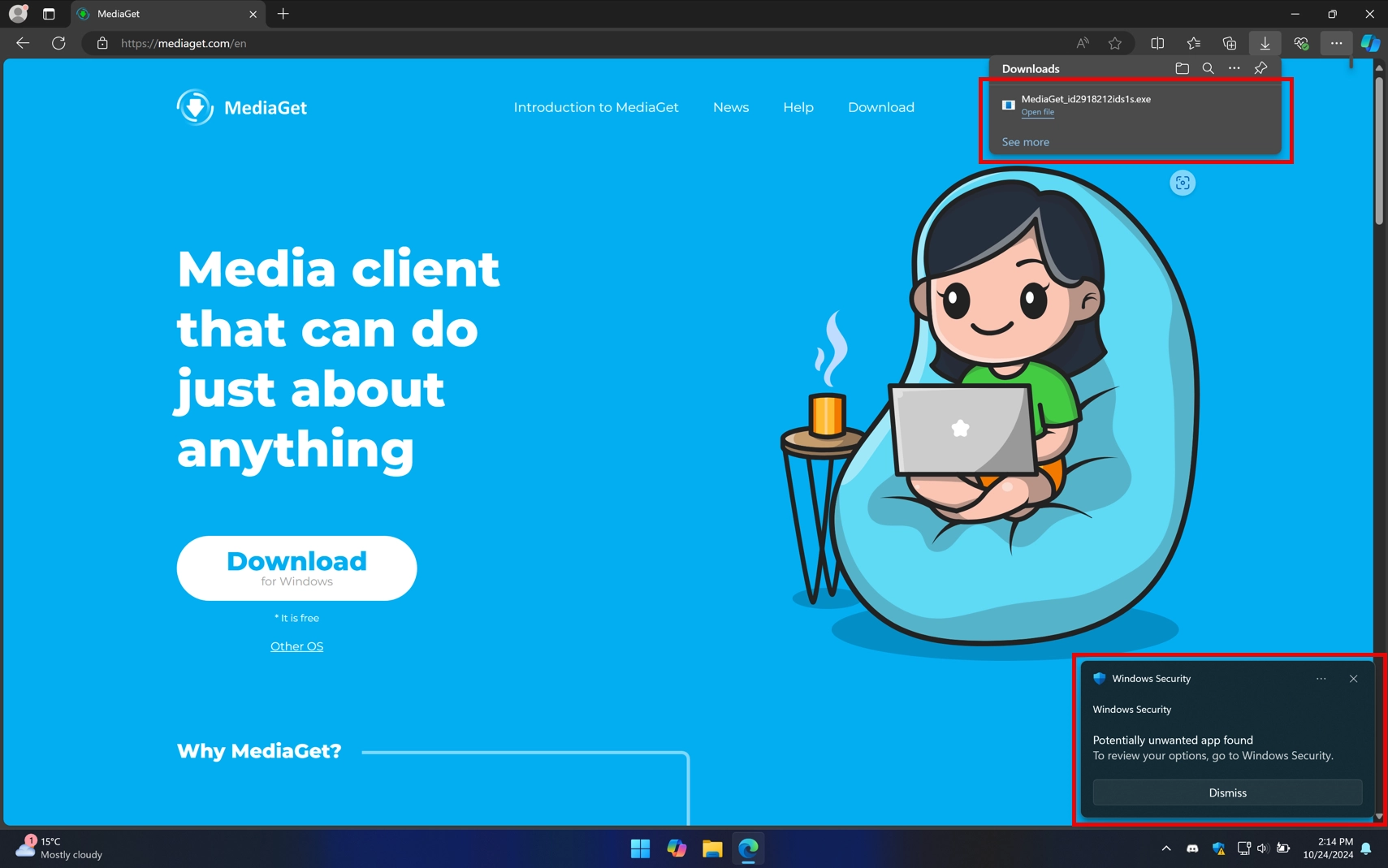
To avoid making unconfirmed claims, I decided to get my own experience with PUABundler:Win32/MediaGet behaves, although on a virtual machine instead of a live system. The first thing that catches your eye is that Microsoft Defender immediately flags the downloaded file from the official website. The random character string in the file name appears to be a failed attempt to prevent detection back at the download stage.
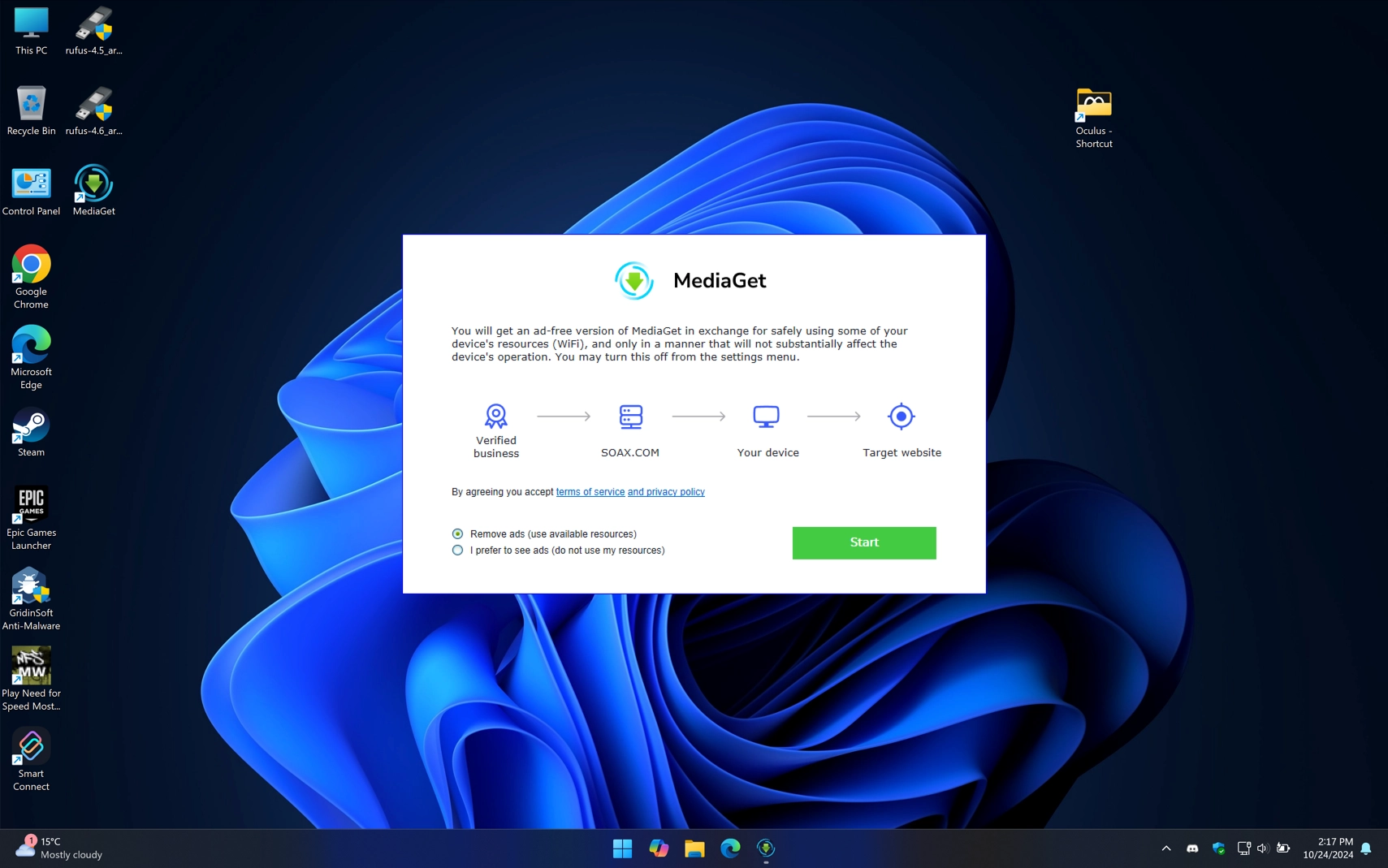
I selected “Allow” in the Defender menu and started installing the program. The first red flag was the program’s offer to provide the device’s resources in exchange for an ad-free experience. I agree, I’m not sorry to share the resources of my gaming PC for the sake of a scientific experiment. We’ll return to this point later; for now, let’s continue with the installation.
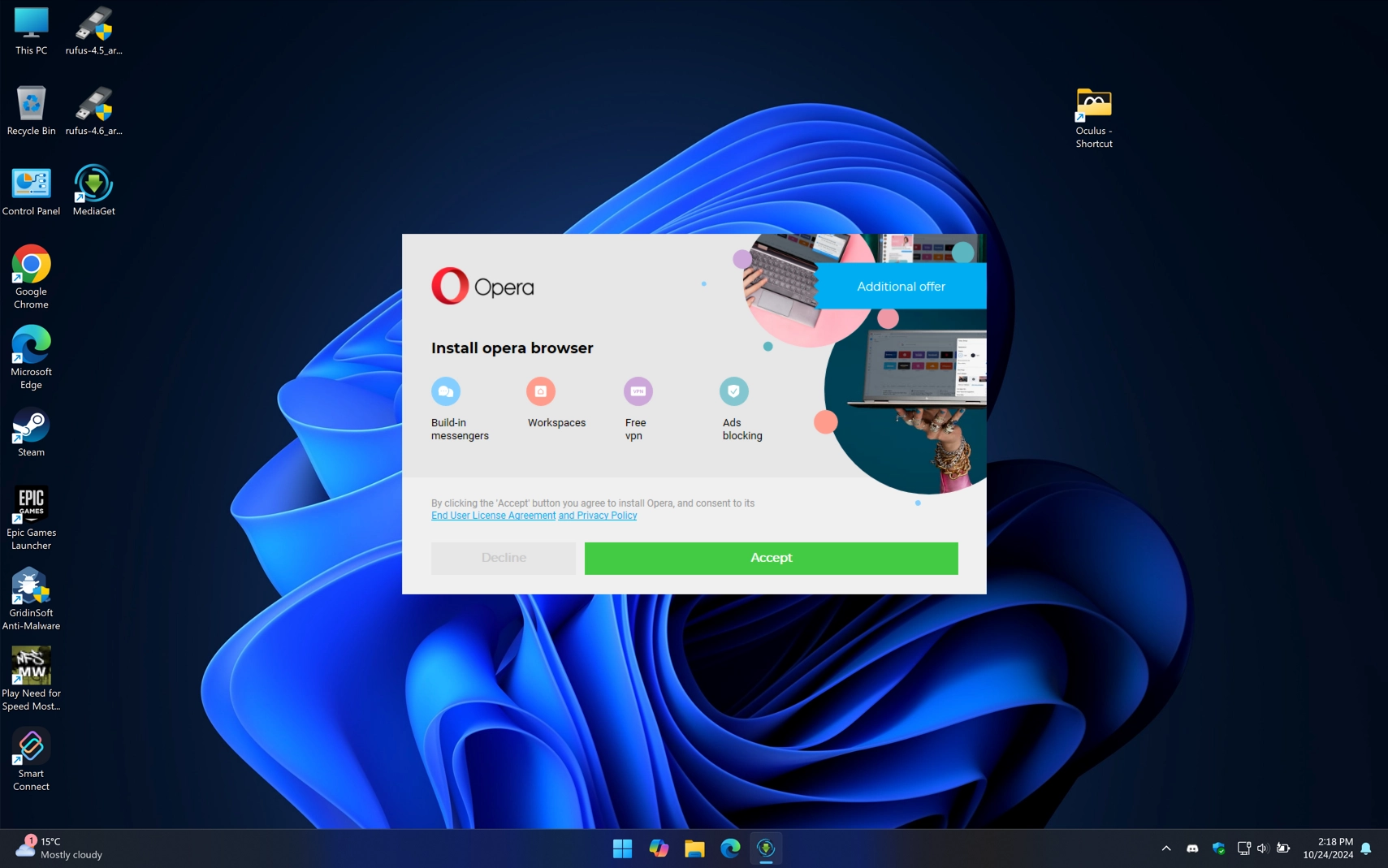
Next, the installer offers to install the web browser Opera. The problem is that there is a big green “Accept” button and a small gray “Decline” button. At first glance it may seem that the Decline button is inactive, but if you click on it the next installation screen appears with the next item of “recommended software”.
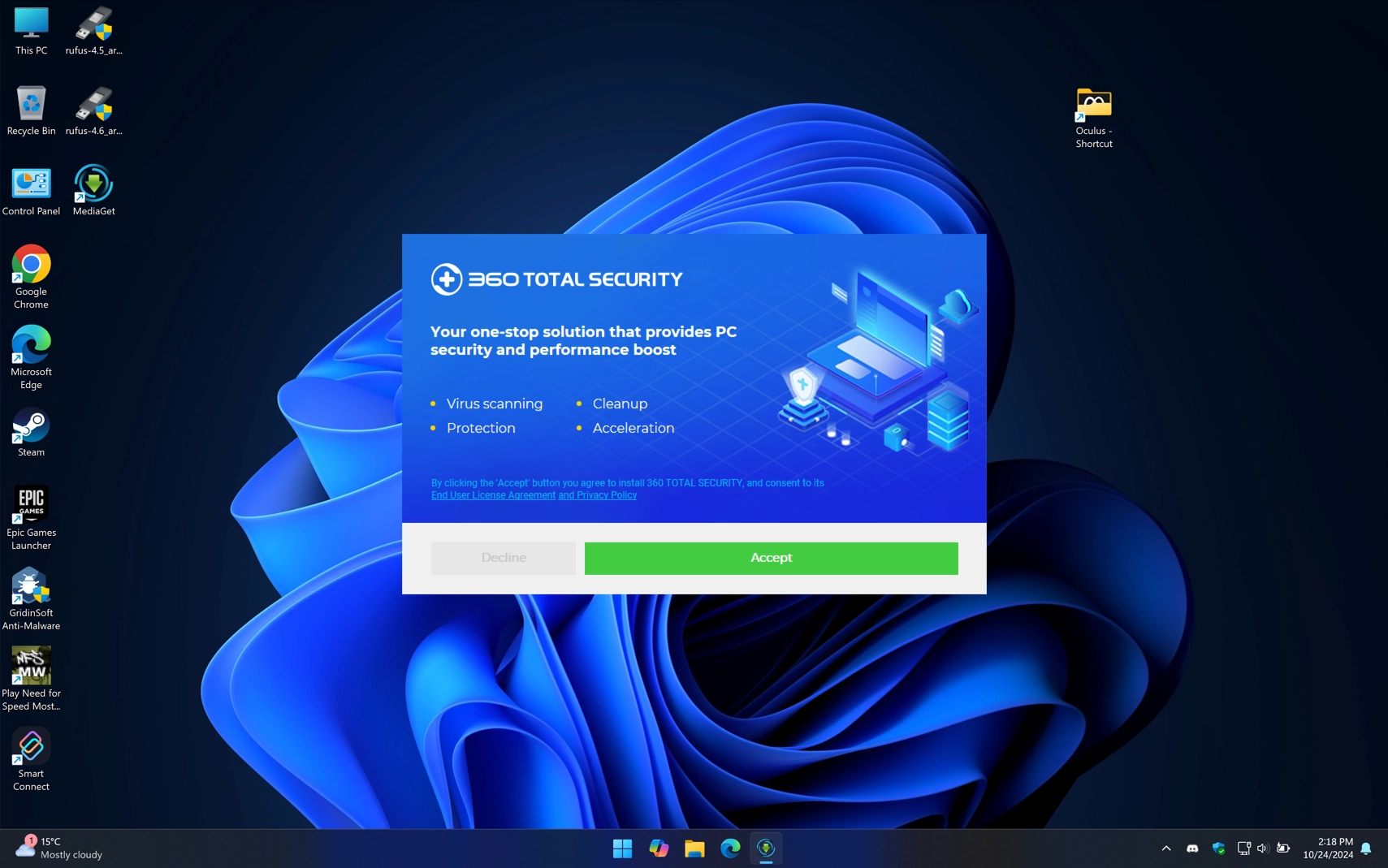
This time, we see 360 Total Security installing – a Chinese antivirus notorious for being hard to remove from the system. Remember at the beginning I talked about the tricks that we would come to later? I was referring to this exact trick with the “inactive” Decline button, which an inexperienced user might not notice and click Accept.
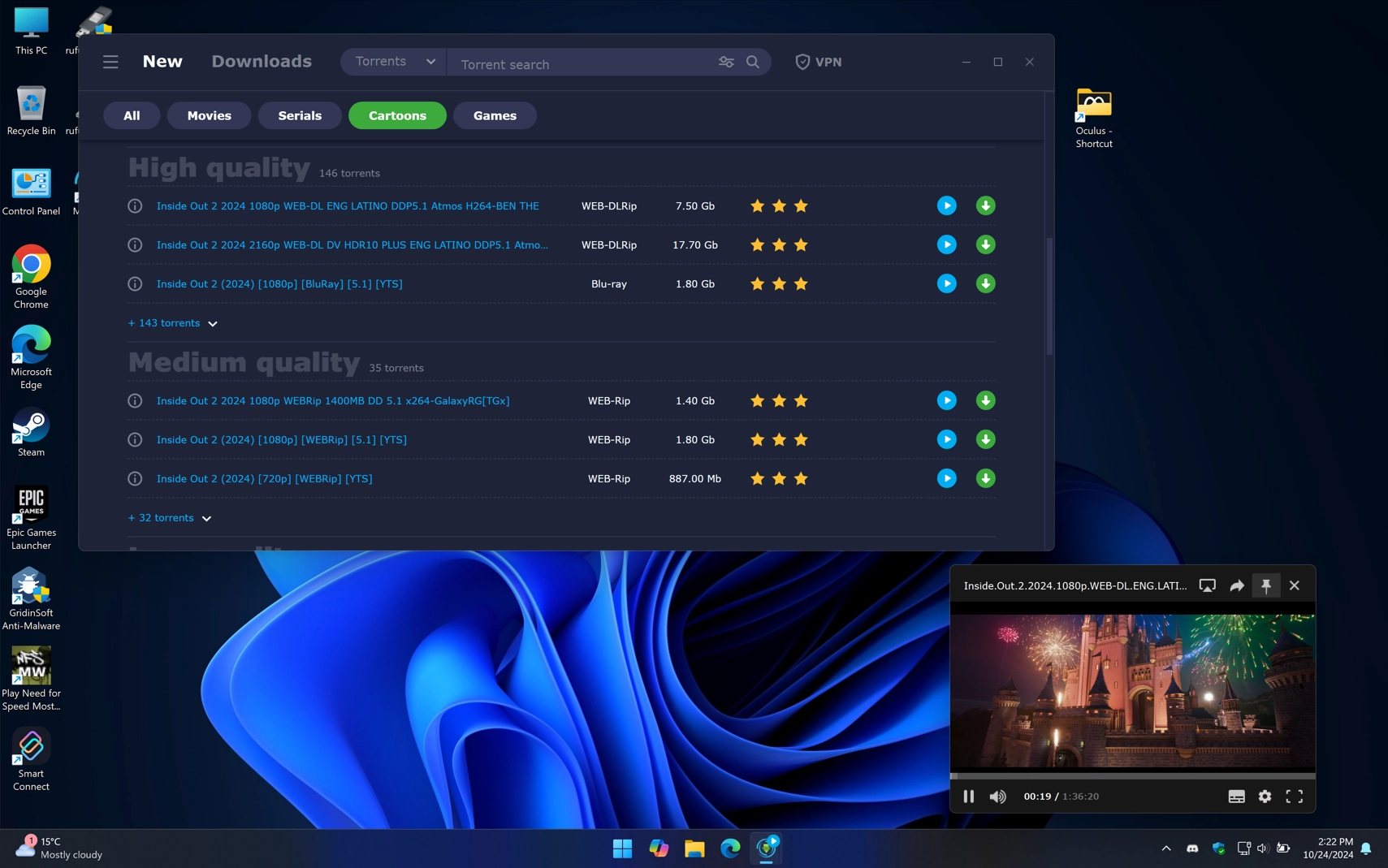
After launching we can see an average client for watching pirated movies/cartoons/serials etc. Although the authors of the program do not mention the program’s origin anywhere on its official website, the presence of buttons of Russian services like VK (Vkontakte) and OK (Odnoklassniki) indicates the program’s Russian origin and target audience.
In addition, this is not the first incident related to this program. It was previously reported that the program does have Russian roots. This is also due to the fact that most legitimate services in Russia are either blocked or non-functional.
Additional Payload
As for the additional programs MediaGet installs along the way, the Opera browser and 360 Total Security antivirus were fairly typical over several consecutive runs. But I would like to take a closer look at the payload that PUABundler:Win32/MediaGet installs to allocate PC resources to third parties. This is the file highsocks.exe, which is added to autorun after installation and runs with the system.
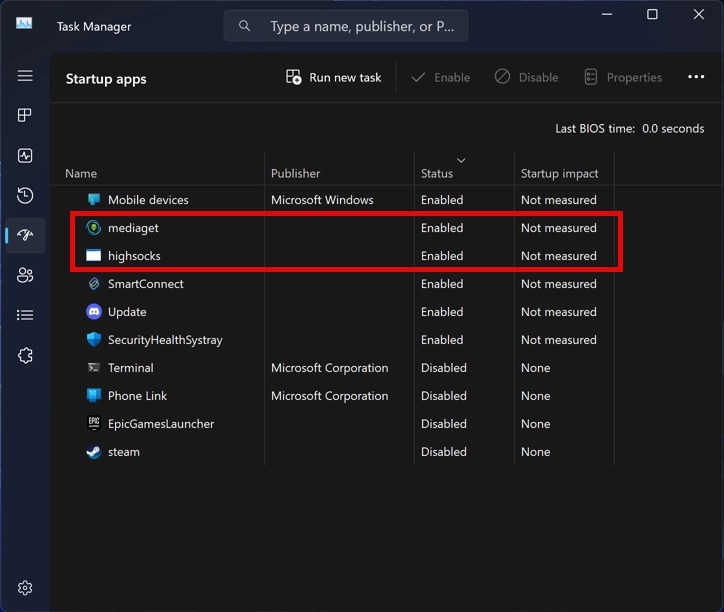
Remarkably, after uninstalling MediaGet, this file remains in the system and still works. Moreover, it is not in the list of installed applications, making it difficult for the user to detect and remove.
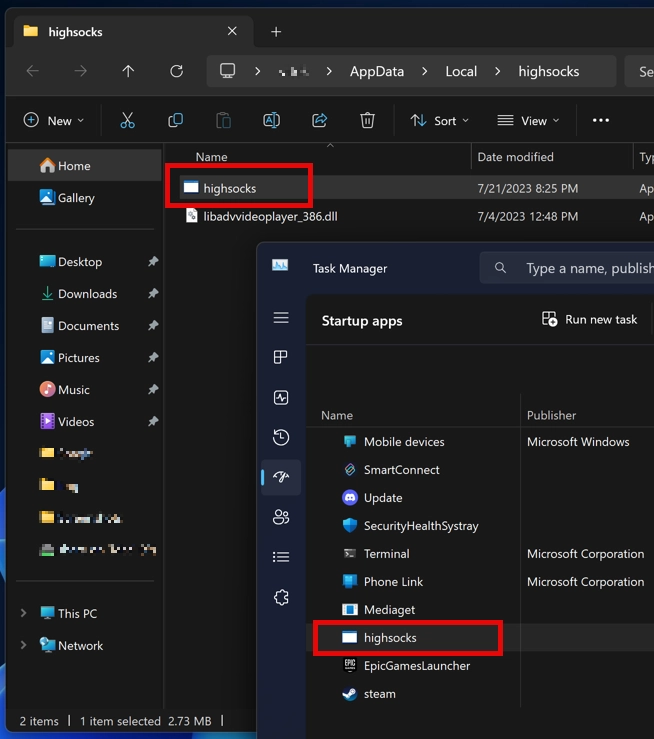
I decided to have a closer look at this file in more detail. Apparently, this program makes the victim’s device a proxy server. Alongside with that, highsocks.exe injects itself into the legitimate system process WMIADAP.EXE and also terminates the svchost.exe process with the parameter WerSvcGroup. The program also executes the shell command:
C:\Windows\System32\wuapihost.exe -Embedding
This could indicate an attempt to mask its activity. The program is primarily running in memory rather than on disk, which suggests that this is an attempt to avoid detection by antivirus tools. But well, all the technical details aside, I can confidently say that this program is proxyware.
Collecting System Information
In addition to the above activities, highsocks also collects certain system information, including language and region settings:
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\MUI\UILanguages\en-US
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Nls\CustomLocale
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\MUI\Settings\LanguageConfiguration
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\MUI\UILanguages
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\MUI\UILanguages\PendingDelete
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\NLS\Language
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\SafeBoot\Option
Although this information might have legitimate uses, when combined with other red flags, it appears more like unwanted activity. This information can also be used to prevent execution in certain “friendly” territories, which is standard practice for malware.
How To Remove PUABundler:Win32/MediaGet
Although PUABundler:Win32/MediaGet is not malware in the truest sense of the word, its monetization and installation methods are not fully clear and secure. As for removing the program and its traces, this can be difficult without specialized tools. I recommend using GridinSoft Anti-Malware, as it is an advanced anti-malware solution that will help you clean your system of unwanted software in two clicks. Just follow the instructions below:

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.