Chinese retailer Temu allegedly suffered a huge data breach. Hackers have put a leaked database for sale on the Darknet, which contains 87 million records with customer information. The company, however, completely denies being hacked or experiencing a data leak. This suggests the possibility that the data was just scraped from other sources.
Temu Hacked, Hackers Sell Leaked Data
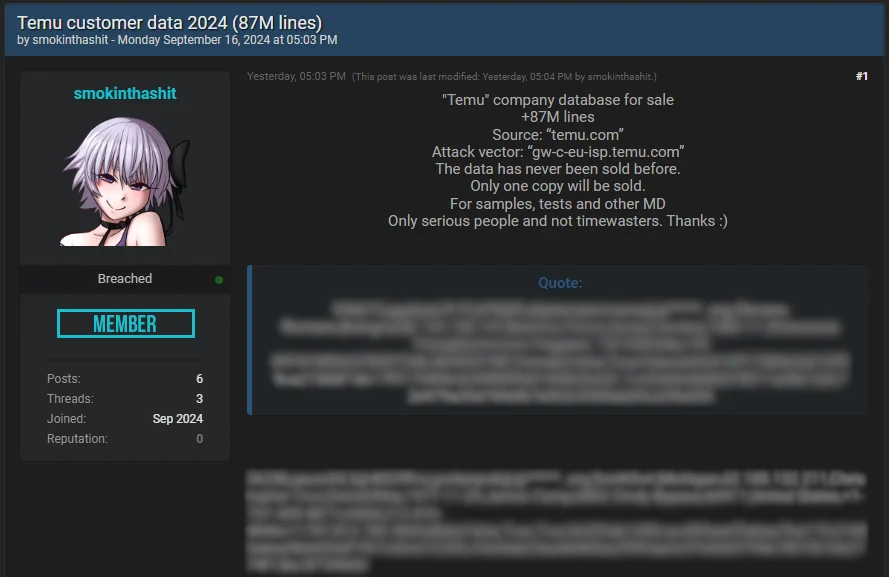
On Monday, September 16, a hacker with the nickname smokinthashit published a post on the hacker forum BreachForums that contains Temu’s user database. The attacker claims that the database contains 87 million records. The database reportedly contains usernames, identifiers, IP addresses, full names, birth dates, phone numbers, shipping addresses, and hashed passwords. As proof, the attacker published samples of the stolen data.
Temu is a Chinese shopping platform that operates pretty much around the world. It offers a variety of goods at relatively low prices. Despite numerous jokes about the quality of goods from Temu, the price-quality ratio allows the service to enjoy great popularity among buyers. It is not surprising that such a statement by cybercriminals caused such a fuss among users of the service.
Temu’s response
Security researchers contacted Temu representatives and asked them to comment on the situation. However, the company categorically denied any data leak. Temu said they examined the samples published by the attackers and found no matches with their databases. The platform representatives also clarified that they take user data privacy seriously and have the app’s MASA certification. They also have independent security validations, a HackerOne bug bounty program, and comply with the PCI DSS payment security standard.
For their part, the attackers went on to claim that they had indeed hacked Temu. They also claimed they still had access to the company’s internal dashboards and knew of the vulnerabilities in the code. However, they provided no evidence to support this claim. In any case, as a security measure, service users are recommended to enable two-factor authentication and change their passwords. In addition, against the backdrop of the incident, astrologers announced an increase in phishing attempts related to Temu and online shopping.
May Users be in Danger?
Although such statements from hackers are not usually made without any proof, there is no reason to believe them now. According to the responses from Temu’s representatives and attackers, it appears to be a database compiled through web scraping from various sources rather than a fresh breach. However, If the data breach is confirmed, it would suggest that sensitive information like actual shipping addresses, bank card details, and purchase history has been leaked online. Still, taking preventive measures like changing your password and enabling 2FA is always a good idea.