WithSecure (formerly F-Secure Business) researchers claim that the content of encrypted messages sent through Microsoft Office 365 can be partially or completely disclosed due to the use of a weak block cipher.
Although the experts received a bug bounty for their discovery, no fix for this problem is expected, and Microsoft has stated that they do not consider it a vulnerability.
Let me remind you that we also wrote that the list of worst passwords is still topes “123456”, and also that Encryption algorithms for 2G networks have been intentionally weakened.
The WithSecure report explains that organizations use message encryption in Office 365 to send and receive email (both external and internal) to keep content private. However, this feature encrypts data using Electronic Code Book (ECB) mode, which allows the message to be read under certain conditions.
The main problem with ECB is that when using the same key, repeating plaintext data areas end up producing the same encryption result, which creates a certain pattern.
This problem first manifested itself back in 2013, when tens of millions of passwords leaked from Adobe, and researchers discovered that the company used the 3DES symmetric block cipher in Electronic Code Book (ECB) mode to encrypt data, and this allowed converting all passwords to plain text format. In 2020, a similar vulnerability (CVE-2020-11500) was found in the video conferencing app Zoom.
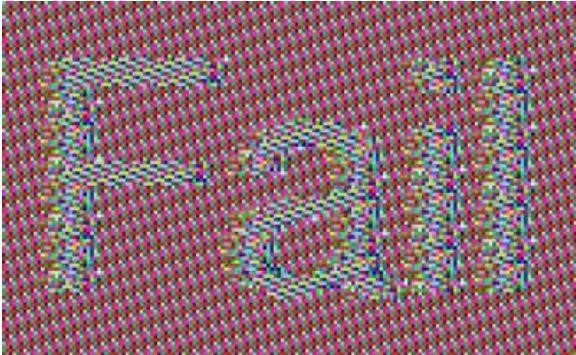
As WithSecure now explains, “thanks to” the use of ECB, the content of encrypted Office 365 messages cannot be decrypted directly, but structural information about these messages can be obtained. That is, an attacker who manages to assemble several encrypted messages can detect patterns that can cause parts of the messages to gradually become readable without using the encryption key.
Thus, a large database of messages allows concluding about the entire content of the letter or only parts of it, looking at the relative position of repeated sections. To demonstrate the potential for such an attack, experts showed the contents of an image that was extracted from an encrypted Office 365 message.
Analysts emphasize that the attack can be carried out offline and use any previously sent, received or intercepted encrypted messages, and there is no way for organizations to prevent the analysis of already sent messages.
But the most interesting thing is that WithSecure analysts notified Microsoft about this issue back in January 2022 and received a $5,000 bug bounty from the company. However, no patches were released after that.
The specialists repeatedly “reminded” the developers about the vulnerability and tried to find out at what stage the problem was solved, but in the end, Microsoft informed WithSecure that this problem was not considered a vulnerability at all and, therefore, there would be no fixes for it, and there would be no CVE identifier.
Now that WithSecure experts have made the issue public, Microsoft has explained to the media that the company is still using ECB because of its support for legacy applications. At the same time, the company is working on adding an alternative encryption protocol to future versions of the product.
After that, WithSecure specialists reported that if no fixes are expected, then the only way to protect is to refuse to use Microsoft Office 365 message encryption at all.