Veeam has released security updates to address a critical flaw, CVE-2024-42448, with a CVSS score of 9.9. This flaw impacts the Service Provider Console (VSPC) and could pave the way for remote code execution on susceptible instances.
Veeam’s Critical RCE Vulnerability Patch Discovered
Veeam has issued a security patch to address two critical flaws in its Service Provider Console (VSPC) software. The most critical of these, tracked as CVE-2024-42448, could allow for remote code execution on compromised systems. The vulnerability was assigned a CVSS v3.1 score of 9.9 out of 10, marking it as critical.
The issue arises when a VSPC management agent, authorized to interact with the server, is exploited to execute malicious code remotely on the VSPC server machine. The problem was identified during Veeam’s internal security testing.
The second vulnerability, CVE-2024-42449, appears to be less critical, with a CVSS score of 7.1. This flaw may allow attackers to extract NTLM hashes linked to the service account of the VSPC server. These hashes could then be exploited for further attacks, such as pass-the-hash, granting hackers access to the server and all the data stored on it and on the related systems.
The former vulnerability arises from improper handling of requests originating from an authorized management agent. In particular scenarios, an attacker may transmit specifically crafted commands that the server executes without adequate validation – a rather common case for RCE vulnerabilities.
Once authorized, the management agent (in fact, an instance taken over by adversaries) acquires trusted communication privileges with the server. This trusted connection is then exploited to inject malicious input, resulting in code execution. The underlying issue likely pertains to insufficient input validation or an absence of isolation in the execution process.
This attack allows malicious actors to run arbitrary commands or code on a targeted system without direct physical access. In this case, the attacker must have an authorized VSPC management agent to exploit the flaw, which could occur through credential compromise or insider threats.
Thing is – it is possible to chain these vulnerabilities to reach the needed conditions. If an attacker acquires NTLM hash through the second flaw, they can perform pass-the-hash attacks, thereby accessing the management agent. And at this point, the first flaw becomes available for exploitation, leading to anything from malware injection to data exfiltration.
Affected Versions
These vulnerabilities affect VSPC version 8.1.0.21377 and all previous versions of builds 7 and 8. Unsupported versions are also considered at risk, even though they were not tested explicitly. The research shows over 140 thousand instances of Service Provider Console available to the Web over the last year.
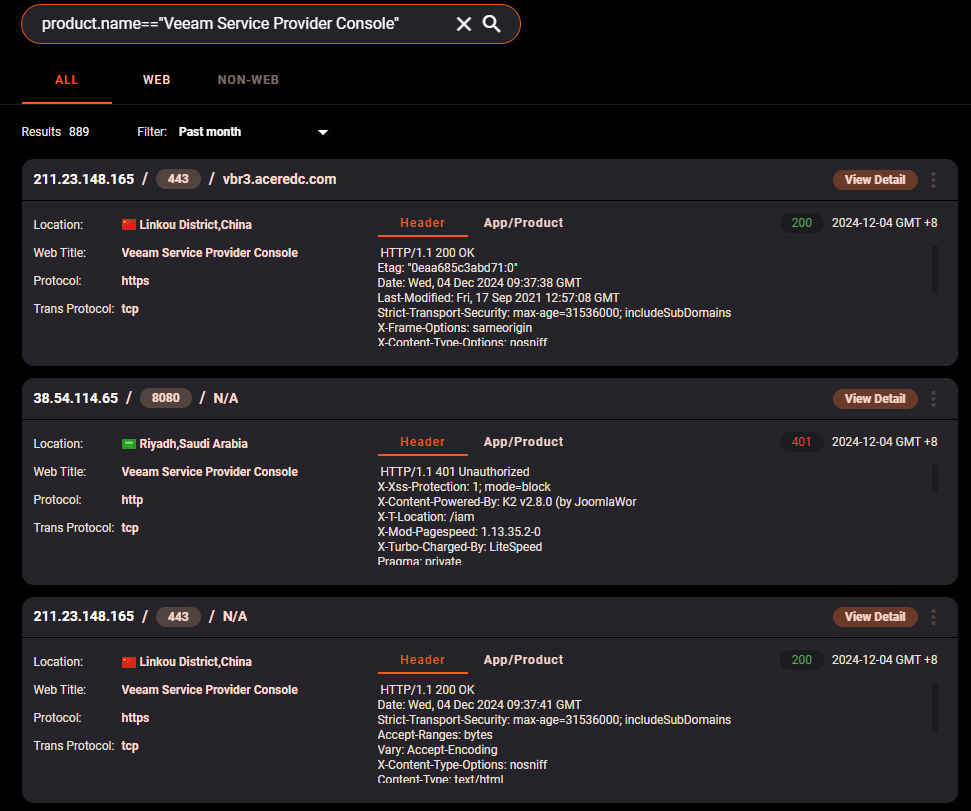
Even more of them are closed within corporate networks, which does not make the situation any better considering the character of vulnerabilities. To mitigate these threats, Veeam urges users to upgrade to version 8.1.0.21999 immediately, as no alternative mitigations are available. Given the history of Veeam vulnerabilities being exploited to deploy ransomware, users should act promptly to secure their systems by applying the patch.