Amid the chaos of Twitter’s transition to the new name – X, scammers have devised yet another deception scheme. They offer Twitter Blue users to transfer their subscriptions to X, but the victim gives the attackers access to their Twitter account instead of moving.
Twitter Blue to X Phishing Emails
As Twitter’s global rebranding is not going as well as planned, scammers are taking advantage of it. For example, a Twitter user named @fluffypony recently received an email designed for Twitter Blue users. As a reminder, Twitter Blue is a checkmark that previously indicated that an account was verified. However, after the purchase of Twitter by the great strategist Elon Musk, it could be obtained by anyone for $8 a month. The email informs the user, “Twitter Blue seamlessly transforms into Stay Blue with X, your existing subscription is nearing its expiration and requires migration,” and prompts them to click the blue box labeled “Transition”. In addition, the email says that if the user fails to complete the migration, he risks losing his verified checkbox. As a result, he will have to reapply for it and re-subscribe. It’s worth noting that this phishing campaign is not targeted, and similar emails were received by Twitter users who are not tick owners.
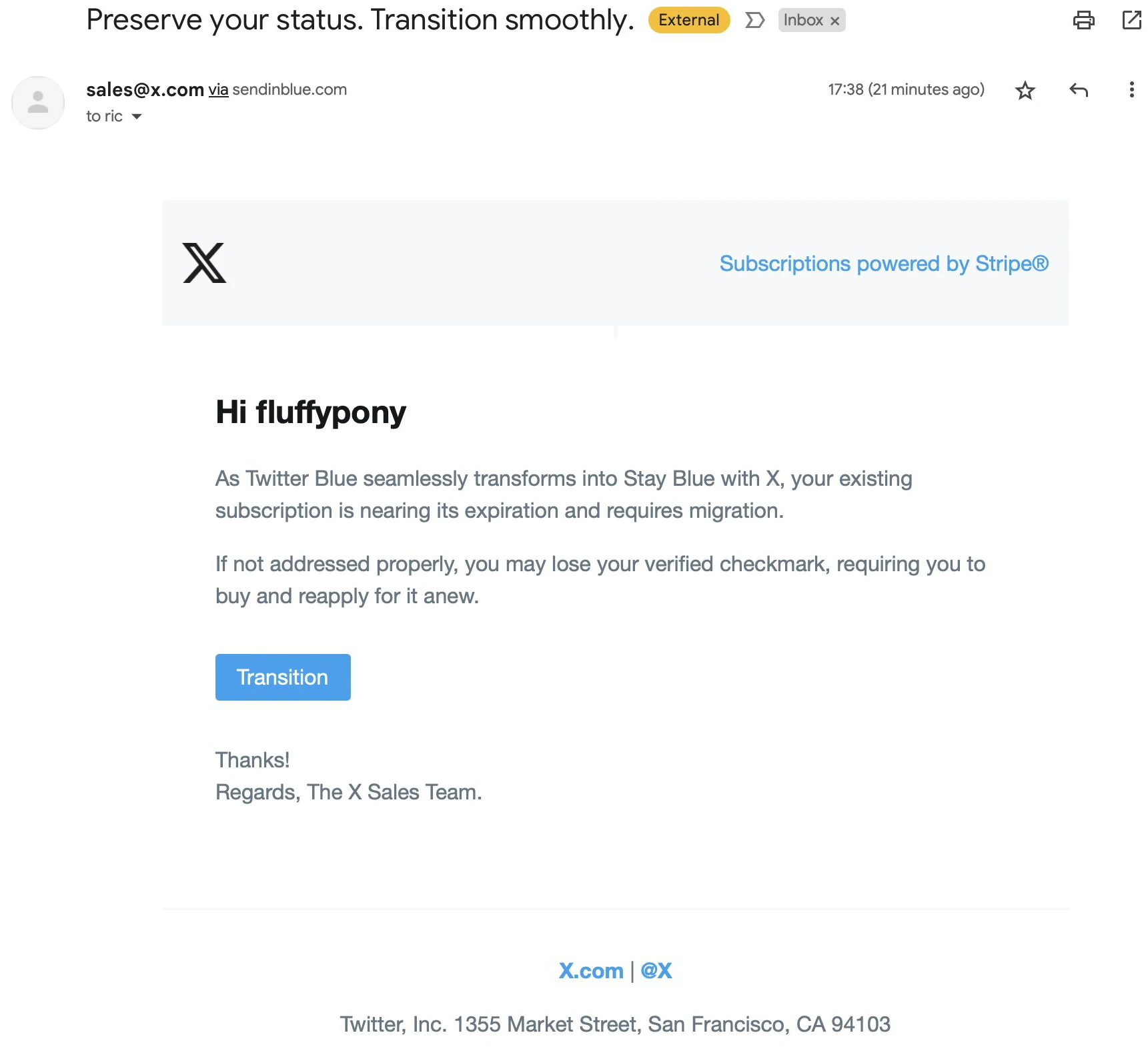
Email details
Although the email is definitely phony, the attackers have gone to great lengths to make the scheme as effective as possible. First, the email comes from x.com and passes the Security Policy Framework (SPF), even though it comes from the Sendinblue (now known as Brevo) mailing list platform. This customer relationship management (CRM) company includes a mailing list platform that bypasses many spam filters, including those in Gmail. As mentioned above, the email contains a “Transition” link that, when clicked, opens a legitimate API authorization screen that asks you to log in and an app that looks like the official Twitter app. However, as @fluffypony writes, the post-authorization URL is null/complete, so it is not a valid Twitter application. In other words, authorizing the app will give attackers control over the victim’s Twitter account. Attackers will be able to access and update the profile and account settings and subscribe and unsubscribe to accounts. Cybercriminals can view, publish, and delete tweets from the account.
Mitigation
Suppose you are a victim of this phishing campaign. In that case, you can block the attackers from accessing your Twitter account by following the steps:
- Go to Twitter Settings
- Open Security and accounts access, then go to Apps and Sessions
- Here, find the Connected Apps menu
- There, revoke app authorization. This will terminate the authorization attempt from the phishing email.
Safety recommendations
Although, even if you are not affected by this phishing attack, you can check your authorized applications. Twitter is aware of this issue and is working to fix it. Anyway, the primary responsibility lies with the end user. We recommend that you take the following tips into consideration, which will help you avoid such scams in the future:
- Be careful with the emails you receive. Statistically, phishing is the most effective method of spreading malware. Only open it if you expect to receive an email from a specific company or organization.
- Carefully check the address of the site to which you are redirected. Please hover the mouse over the link or button, and the full address where the link leads will appear in the lower left corner. Do not follow the link if the site address differs from the correct one. (This method may not work if attackers use a URL Shortener).
- Never enter your personal information, such as logins and passwords, on sites you don’t know or doubt their legitimacy. Today, scammers have learned how to spoof legitimate sites. The presence of an SSL certificate on a phishing site is no surprise to anyone. Therefore, it is essential to be vigilant before entering any information on the site.
- Be careful with attachments and links. Legitimate organizations never ask via email to download and run a file. Instead, they ask you to download the file from the official website. Only open files or click on links if you are sure the sender is trustworthy.
- Use two-factor authentication for your online accounts. 2FA adds an extra layer of security by asking you to enter a code from your cell phone when you log in.
- Use antivirus software and keep it up to date. Sometimes a person can make a mistake and inadvertently download malware onto a device. In this case, an anti-malware solution will neutralize the threat before it deploys the payload.


