Trojan:Win32/Patched refers to a detection for modified versions of legitimate programs. Often such modifications are made to add malicious functionality to a program.
Trojan:Win32/Patched Overview
Trojan:Win32/Patched is a Microsoft Defender detection used to detect programs that have been modified by hackers to perform malicious actions. Unlike traditional Trojans that disguise themselves as useful software, this threat involves injecting malicious code into actual legitimate programs. This code is getting executed along with a totally functional app.
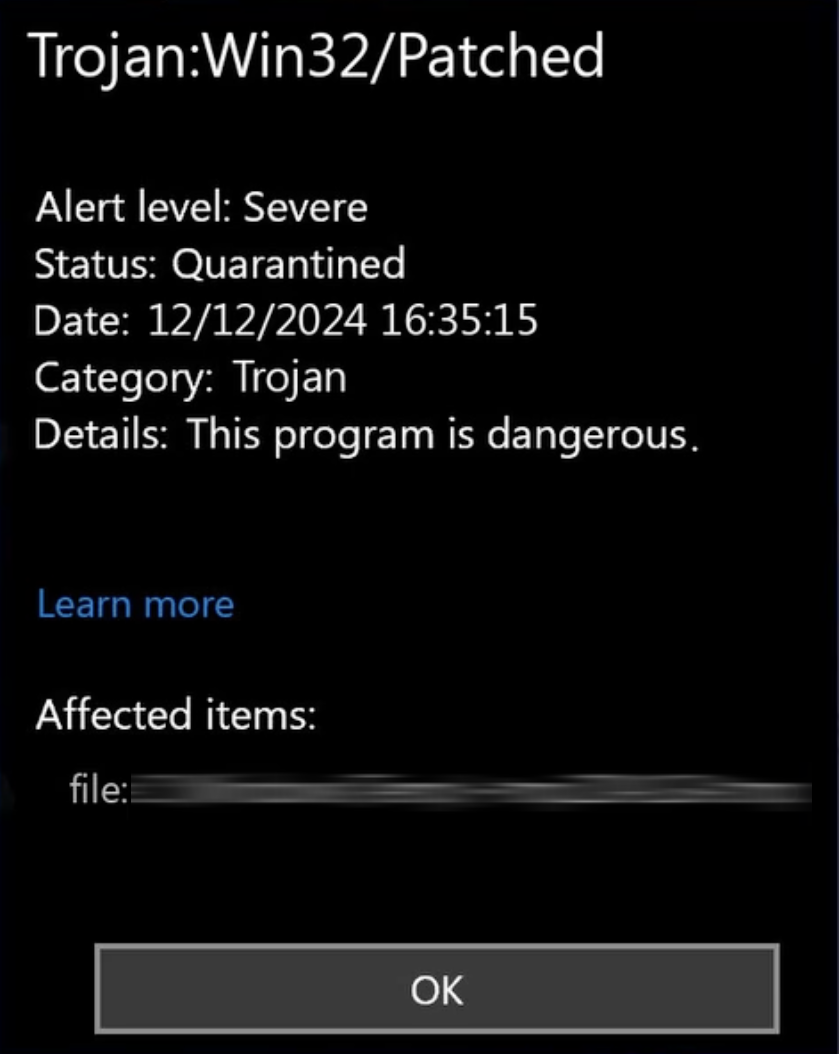
The threat of Trojan:Win32/Patched lies in its ability to inject malicious code into executable files like EXE or DLL. These modifications may be minimal, but enough for the program to start performing actions not originally intended by the developer. Typically, the main purpose of the modification is to steal data. Malicious code can be used to obtain sensitive information such as passwords, cryptographic keys or financial data.
Crypto wallets are the most frequent targets of such modifications, as they contain valuable data, as well as browsers, where it is possible to steal stored passwords or interfere with the user’s browsing process. We also cover browser-related threats in a separate post. Password managers are also of interest, as their compromise gives attackers full access to credentials.
Such software is often distributed through software downloaded from dodgy sources, like P2P networks and sites with cracked software. Installing such programs typically involves ignoring or disabling anti-malware notifications. Aside from this, malware may hide in strange scripts you are asked to run for “human verification”.
Is It a False Positive?
Sometimes the Trojan:Win32/Patched detection may be a false positive, but in most cases, it is accurate. Antimalware solutions, including Windows Defender, may mistakenly flag modified files as threats, even when they lack malicious code.

This often happens in the case of pirated software where the checksum of the file does not match the original one. Defender interprets this as a modification and, therefore, a potential threat.
False positives, however, are not exclusive to pirated software. They can also occur during program updates if the certificates for these updates have not yet been included in antimalware databases. In such situations, the updated file may be mistakenly labeled as malicious, although it is actually legitimate. This happens because antimalware tools often rely on signatures and checksums, treating any inconsistencies as potential threats.
If you encounter a Trojan:Win32/Patched detection and are in doubt whether it is a false positive or a real detection, you can download a third-party anti-malware solution such as GridinSoft Anti-Malware and run a scan with it. Having results from at least two sources provides a more comprehensive assessment.
How to Stay Safe?
To minimize the risks associated with Trojan:Win32/Patched, following basic cyber hygiene practices is sufficient. First, always download application installers from official websites. Second, avoid clicking on “Sponsored” links in search results when looking up popular queries. These links often lead to modified programs or, in some cases, malware disguised as legitimate software.
Third, never download cracked software. Not only is this illegal, but it also carries a high risk of downloading malware instead of the intended program. Lastly, ensure you use reliable anti-malware software. This serves as a crucial line of defense if a threat manages to reach your device.