Win64/Reflo.HNS!MTB is a detection of a malware sample that aims at stealing confidential information. It usually spreads through game mods and works as quietly as possible. That virus may belong to any malware family, as it is a behavioral detection of a specific action that it does in the system.
Win64/Reflo.HNS!MTB Overview
Trojan:Win64/Reflo.HNS!MTB is a heuristic detection used by Microsoft Defender to detect a specific type of malware. This malware is a type of spyware and can actively collect sensitive information, such as user credentials, from the victim’s system. Heuristic detection is used when malware has certain characteristics and behavioral patterns that match known threats, but it may not have a matching signature in the antivirus database.
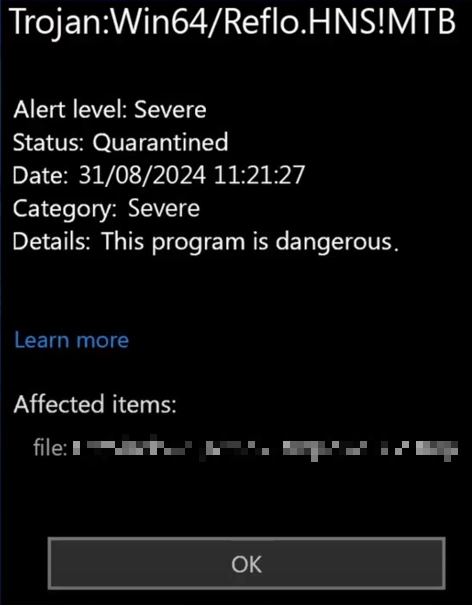
After the execution, Reflo Trojan will start its malicious activity immediately, with the primary goal of stealing confidential information. This can end up with your social media accounts to start sending spam messages, and banking accounts being drained. This type of malware is designed to operate stealthily, so its presence is usually difficult to detect. In most cases, the victim only discovers it when significant damage has already been done, such as aforementioned unauthorized access to online accounts.
As with most similar threats, Trojan:Win64/Reflo.HNS!MTB is often spread via pirated software. Repackers, modders, and websites that distribute pirated games, cracked programs, or mods may add it as a hidden addition to their repacks. It can also spread through email attachments, malicious links, or accidental downloads on compromised websites. However, the main source of this threat is questionable game mods.
Technical Analysis
Now let’s see how this malware behaves on a compromised system. As mentioned earlier, this virus is mainly distributed via game mods. This suggests that any detections might be false positives by default. Although the user won’t notice anything visually, clicking “allow” triggers certain processes in the system.
The process begins with the following command:
"C:\Windows\system32\cmd.exe" /c "cd ^"C:\Users\
C:\Windows\system32\cmd.exe /K "C:\Users\
python Setup.py
Next, the malware checks for the presence of a sandbox or virtual environment and fingerprints the system. To do this, it checks the following registry keys:
HKEY_CURRENT_USER\Software\Policies\Microsoft\Windows\System
HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Command Processor\AutoRun
HKEY_LOCAL_MACHINE\Software\Microsoft\COM3
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\ComputerName\ActiveComputerName
This is a standard procedure for malware that prevents the threat from running in a virtual environment. In addition, Trojan:Win64/Reflo.HNS!MTB uses some tricks to prevent dynamic analysis.
Payload
The following commands are used by the Reflo Trojan to drop and unpack the payload:
"C:\Windows\SysWOW64\unarchiver.exe" "C:\Users\user\Desktop\RedTiger-Tools-main.zip"
7620 - C:\Windows\SysWOW64\7za.exe "C:\Windows\System32\7za.exe" x -pinfected -y -o"C:\Users\user\AppData\Local\Temp\cjov35ys.mq0" "C:\Users\user\Desktop\Appname.zip"
7660 - C:\Windows\System32\conhost.exe C:\Windows\system32\conhost.exe 0xffffffff -ForceV1
The malware drops many files into the Windows temporary directory C:\Users\user\AppData\Local\Temp\, including many “.py” files that are necessary for the malware to work.
Credential Access
The next step is to collect confidential information. This is done by creating a DirectInput object that enables the malware to read keystrokes. In this way, attackers can intercept usernames and passwords that the victim enters on their device. Once the user authorizes the execution of this threat, it can run in the background for an extended period. The malware is extremely stealthy, and the name of the executable can be random. Therefore, the user is unlikely to realize why they can no longer log into their account.
Besides keylogging, the hijacker also collects confidential data already stored on the system. Among other things, the malware can collect cookies, saved passwords, and credit card information from autocomplete forms in popular browsers. Even though the latest versions of browsers encrypt this information in encrypted form, it does not protect it completely. The malware can also collect cookies, saved passwords, and credit card information from autocomplete forms in popular browsers. Typically, the query looks like this:
SELECT action_url, username_value, password_value FROM logins
Almost always, infostealer malware like Reflo.HNS!MTB targets the most popular web browsers. Chrome, Chromium, Opera, Firefox and some of the popular alternatives to the mainstream applications are among the target list. Still, using the no-name browser won’t always secure you: malware masters can easily adjust the list of applications their virus will extract credentials from.
C2 Connection
The malware communicates with multiple addresses on the internet, but certain addresses are of particular interest. Specifically, it attempts to connect to .onion addresses, which are associated with the Darknet. Our instance is trying to connect to:
3bp7szl6ehbrnitmbyxzvcm3ieu7ba2kys64oecf4g2b65mcgbafzgqd.onion
55niksbd22qqaedkw36qw4cpofmbxdtbwonxam7ov2ga62zqbhgty3yd.onion
7mejofwihleuugda5kfnr7tupvfbaqntjqnfxc4hwmozlcmj2cey3hqd.onion
ajlu6mrc7lwulwakojrgvvtarotvkvxqosb4psxljgobjhureve4kdqd.onion
These are just a few of the addresses, but in addition to darknet sites, the malware tries to connect to URLs related to Discord, Telegram, Mastodon or similar social networks. That tactic allows frauds to mask the final command servers, as the corresponding user profiles will contain nothing but the link to the “main” C2.
How To Remove Trojan:Win64/Reflo.HNS!MTB?
To remove Trojan:Win64/Reflo.HNS!MTB, it’s essential to use an advanced anti-malware solution. I recommend GridinSoft Anti-Malware, as it can offer permanent protection against most threats in addition to cleaning. The first step is to scan your system and remove all detected threats. To do this, follow the instructions below:

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.

After removing the threats, be sure to change your account passwords and terminate any suspicious sessions. This step is crucial to prevent attackers from regaining access to compromised accounts.