Trojan:Win32/Vigorf.A Virus Removal Guide
Your antivirus just flagged Trojan:Win32/Vigorf.A and you're wondering what's going on. Your…
Program:Win32/Uwamson.A!ml
Win32/Uwamson.A!ml is a specific name of a Microsoft Defender detection. This designation…
Microsoft Account Unusual Sign-in Activity
Email notification of a suspicious login attempt to your account is a…
Pornographic Virus Alert From Microsoft
Microsoft shows you the banner which states that your PC is infected…
Microsoft Email Scam
Hackers are constantly finding new ways to infect your computer with malware…
Microsoft SharePoint Vulnerability Exploited, Update Now
In late March 2024, the U.S. Cybersecurity and Infrastructure Security Agency (CISA)…
Microsoft is Hacked, Again by Midnight Blizzard
Microsoft acknowledges being hacked for the second time this year, by the…
Windows SmartScreen Vulnerability Exploited to Spread Phemedrone Stealer
The malicious campaign exploits the CVE-2023-36025 vulnerability in Microsoft Windows Defender SmartScreen…
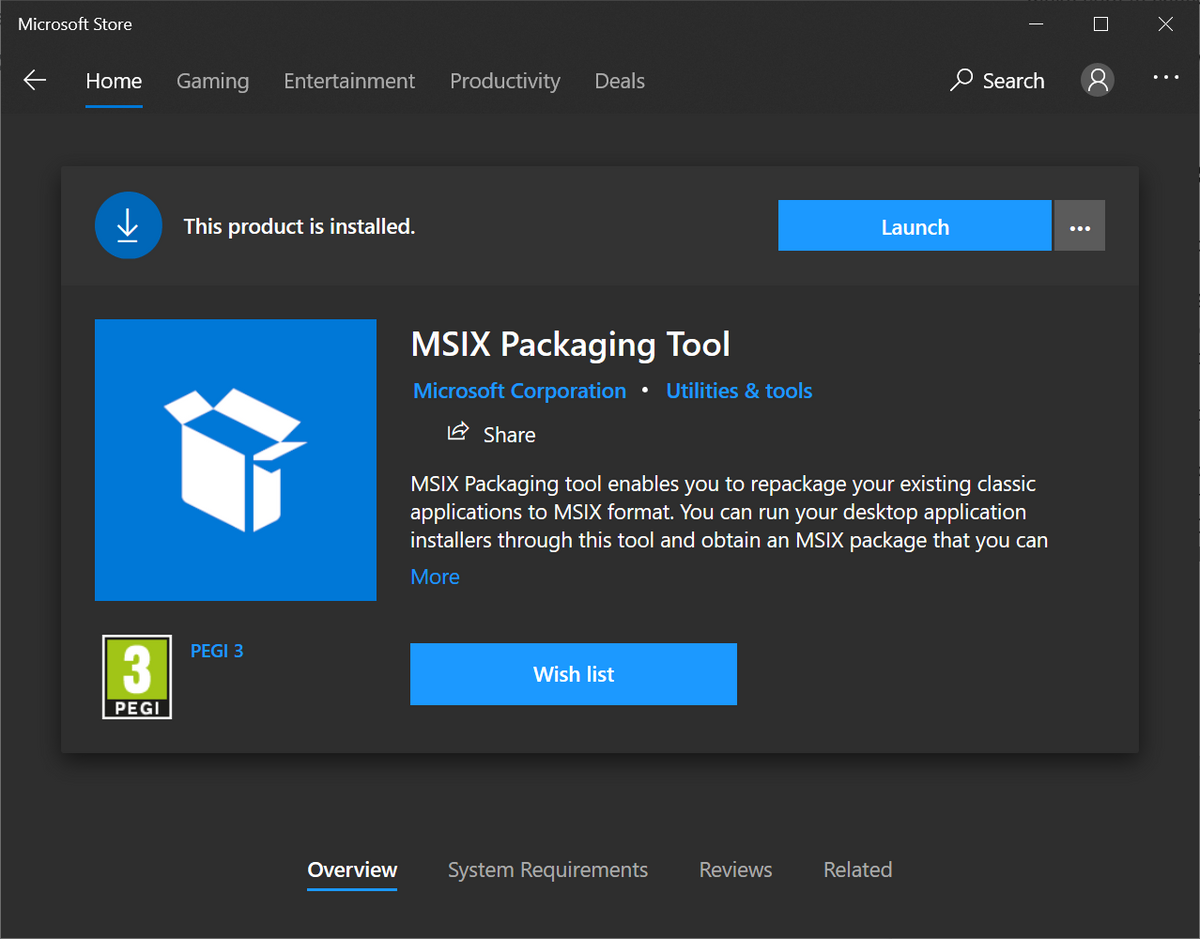
Microsoft Disables MSIX App Installer Protocol
Microsoft reportedly disabled MSIX installer protocol in Windows, due to its exploitation…
Cactus Ransomware Attacks – Microsoft Alerts
Microsoft has raised the alarm about a growing wave of ransomware attacks…
What is Microsoft Security Warning Scam?
Fraudsteds massively employ Microsoft Azure hosting to start Microsoft Security scam pages.…
Octo Tempest Threat Actor – The Most Dangerous Cybercrime Gang?
Octo Tempest, a financially-motivated hacking group, has been labeled "one of the…