Corrupted Word Documents Phishing Attacks Avoid Security Checks
Hackers found a new way of bypassing the email security filters and…
Skyjem.com
Skyjem.com is a questionable search engine that you may see appearing in…
Ledger Recovery Phrase Verification Scam
“Ledger Recovery Phrase Verification” is a scam email that targets non-vigilant users.…
CISA Urges to Patch Critical Array Networks Vulnerabilities
The US cybersecurity agency CISA warned about the ongoing exploitation of a…
NodeStealer Returns With Python Codebase, More Functions
Researchers have identified an updated version of NodeStealer, now rewritten in Python.…
Opera GX
Opera GX is a special version of the Opera browser with extra…
GitLab Fixes Critical Kubernetes Agent Takeover Vulnerability
GitLab has released another update that fixes varying degrees of vulnerabilities. Users…
FakeBat Loader is Back With New Tactics and Payload
After a brief decline in loader-based malvertising, the FakeBat loader has re-emerged…
RCE Vulnerability in Ivanti Endpoint Manager Uncovered, Patch Now
In the latest update release, Ivanti disclosed the selection of critical vulnerabilities…
Hacker Leaks Corporate Data Stolen in 2023 MOVEit Breaches
The hacker, known as Nam3L3ss, posted the data of over 1000 corporations,…
Hacker Leaks BBVA Bank Data, Including User Details
On November 11, 2024 a hacker known as Gatito_FBI_NZ published an extensive…
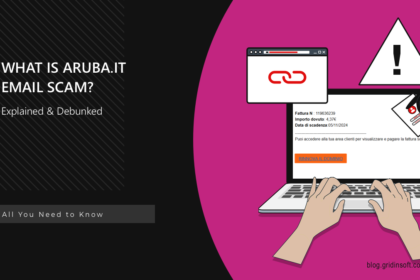
Aruba.it Email Scam
The Aruba.it email scam is a phishing campaign using fake emails that…