Using SmartTube on your Android TV to escape YouTube’s aggressive ads? Bad news. The popular third-party YouTube client just got compromised, and Google Play Protect is forcibly disabling it on users’ devices with all the subtlety of a brick through a window.
Users woke up to “Your device is at risk” notifications, as documented in GitHub issue #5131. Google Play Protect identified SmartTube as dangerous and disabled it automatically. No warning, no appeal, straight to the digital quarantine zone.
Developer Yuliskov’s explanation via GitHub: “Signing keys compromised. Revoked them. New version will have different package ID.” That’s it. No details on how, when, or what the malware actually does beyond “looks like botnet stuff.”
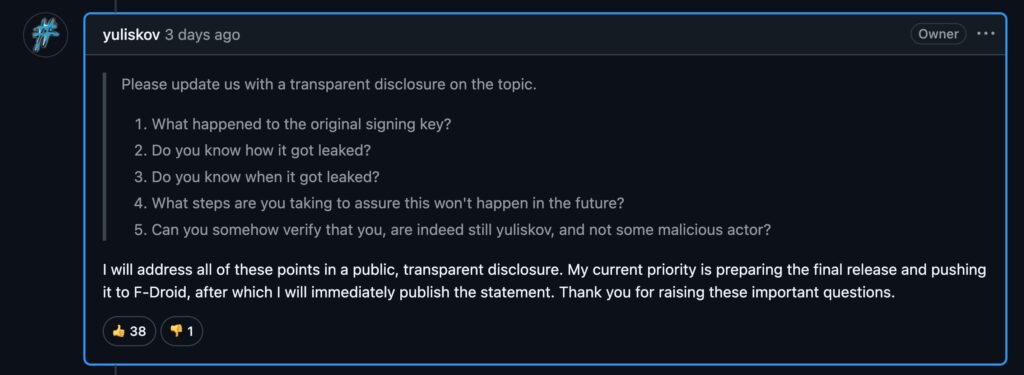
This minimal communication turned GitHub issues into a panic room. Users flooding comments with questions about which versions are safe, whether their credentials are stolen, and if they need to factory reset their TV boxes.
SmartTube exists because YouTube’s official Android TV app has become user-hostile. Longer unskippable ads, aggressive algorithms, and performance issues drove millions to seek alternatives. SmartTube provided ad blocking, SponsorBlock integration, and customization that actually worked.
There’s something darkly poetic about an ad-blocking app being used to install malware. You wanted to avoid YouTube’s unwanted content? Here’s some unwanted software instead.
How the Attack Worked
Classic supply chain compromise:
- Attackers obtained Yuliskov’s app signing keys
- Created malicious SmartTube version with botnet library
- Signed it with legitimate keys
- Pushed as official update
- Users with auto-updates got infected
- Google Play Protect eventually caught it
The malicious library behaves like typical botnet infrastructure—potentially turning your TV box into a DDoS zombie, crypto miner, or credential stealer. Android TV boxes are perfect botnet targets: always on, always connected, rarely monitored, owned by users who don’t realize they’re running full Android systems.
Making panic worse: GitHub showed 30.48 as latest stable. The official website served 30.56. Some users had 30.19 with no update notifications. In a “my app got hacked” scenario, version discrepancies are terrifying. Which versions are legitimate? Which contain malware? Is the website itself compromised?
What to Do Now
If you’ve been using SmartTube:
- Assume compromise if you had auto-updates enabled
- Uninstall completely (don’t just disable)
- Wait for official updates – monitor GitHub for clean version under new package ID
- Change credentials if you entered Google passwords
- Consider factory reset for maximum paranoia relief
The new clean version will have a different package ID because old signing keys are permanently burned. Your settings won’t transfer.
This incident showcases supply chain attack fundamentals. Compromising developer keys is easier than finding exploits. One breach = instant access to entire user base. SmartTube built years of credibility, destroyed in one security failure, as PCWorld’s analysis confirms.
The real failure wasn’t the breach—that happens. It was the aftermath communication. Cryptic three-sentence updates about malware affecting potentially millions of devices? Users deserved better.
Google’s aggressive Play Protect response was actually correct. A compromised app with botnet capabilities should be nuked immediately. But it created confusion about whether this specific version was malicious or if the entire app was permanently banned.
Welcome to the Supply Chain Attack Experience
SmartTube will probably recover. Developer will issue clean builds. Users will cautiously return. But this will make everyone more paranoid about updates.
Some will disable auto-updates entirely, making them vulnerable to different issues. Others will abandon third-party YouTube clients altogether, returning to the official app with its aggressive advertising.
Which might have been YouTube’s goal all along. Nothing kills alternative clients faster than a good malware scare.





