The Security Blog From Gridinsoft
ChatGPT Causes New Wave of Fleeceware
Artificial intelligence is one of the most significant advances in technology. It is used in one way or another everywhere,…
PyPI Malware Storm Forces to Suspend New Uploads
Python Package Index, a software repository for Python developers, recently faced a massive attack. An enormous flow of malicious uploads…
3 Unpopular Malware Spreading Ways in 2023
The modern Internet space is like an endless ocean, where every wave can hide a danger. If you think you…
Visual Studio Code Malicious Plugins Steal Personal Data
Some plugins for Visual Studio Code, a popular code editing tool developed by Microsoft, appear to have malicious code. In…
Trend Micro: Millions of Android Devices Contain Malware Right in the Firmware
Trend Micro analysts presented an interesting report at the Black Hat Asia conference: according to their information, millions of Android…
Google Chrome fixed second 0-day vulnerability in two weeks
Google developers have released Chrome version 86.0.4240.183 for Windows, Mac…
CERT launched Twitter bot that comes up with names for vulnerabilities
Specialists from the CERT Coordination Center (CERT/CC) have launched a…
Google Project Zero discovered a 0-day vulnerability in the Windows kernel
Google Project Zero has discovered a 0-day vulnerability in the…
Microsoft experts talked about Iranian hackers attacks on security conference participants
Microsoft experts talked that Iranian government hackers have successfully hacked…
Gridinsoft becomes Google’s information security partner
Gridinsoft LLC is proud to be one of 68 partners…
Microsoft has released an update to remove Adobe Flash from Windows
As you know, very soon, on December 31, 2020, support…
KashmirBlack botnet is behind attacks on popular CMS including WordPress, Joomla and Drupal
Researchers from Imperva have found that the KashmirBlack botnet, active…
Attackers again deceived Apple’s notarization process
In September 2020, I talked about how the Shlayer malware…
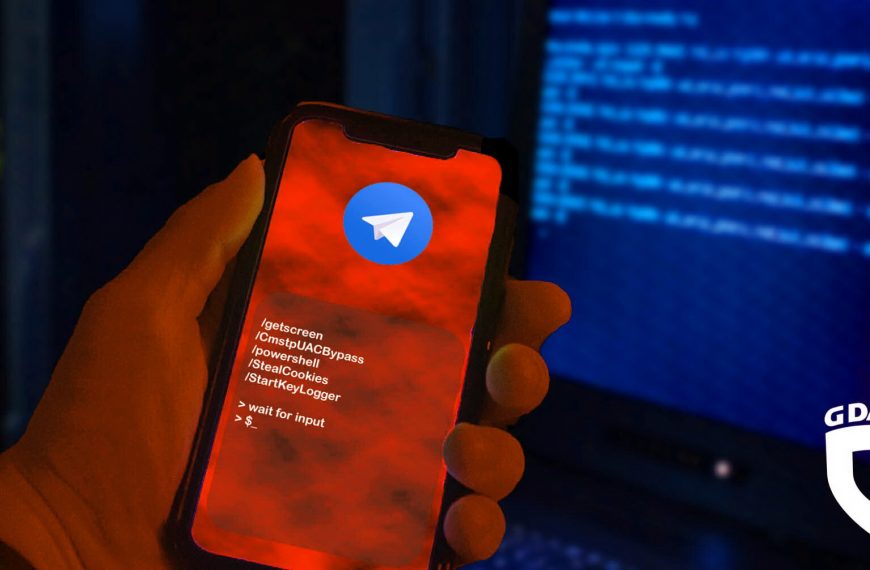
New T-RAT malware can be controlled via Telegram
G DATA’s specialists have published a report on the new…
Google engineers fixed Chrome 0-day vulnerability that was already under attacks
Google engineers have released an updated version of Google Chrome…
Bughunter stole a Monero exploit from another cybersecurity specialist and received a reward for it
Bleeping Computer reporters drew attention to an interesting case that…
P2P botnet Interplanetary Storm accounts more than 9000 devices
Bitdefender experts gave a detailed description of the work of…