The Security Blog From Gridinsoft
Lumma Stealer Spreads Via Fake Browser Updates, Uses ClearFake
Recent research uncovered a selection of websites that deploy Lumma Stealer under the guise of a browser update. They pose…
Microsoft Patches Critical MSMQ Vulnerability
In the latest Patch Tuesday, on June 11, 2024 Microsoft disclosed fixing a substantial number of flaws, including a remote…
Hamster Kombat Game Rises Concern Over Russian Origins
Hamster Kombat, a recently released tap game in Telegram Messenger, raises significant discussions regarding its safety. Investigations show that its…
New Embargo Ransomware Discovered, Possible ALPHV Reborn
A new strain of ransomware, named Embargo, written in Rust, recently surfaced along with its Darknet infrastructure. It uses double…
GitHub Enterprise Server Auth Bypass Flaw Discovered
On May 21, 2024 GitHub disclosed a new authentication bypass flaw in their Enterprise Server. Encoded as CVE-2024-4985, it is…
Google Creates a Red Team to Attack AI Systems
Google says it is creating a red team that will…
Ivanti 0-day exploited to target Norwegian government
Software development company Ivanti (formerly MobileIron Core) has patched a…
Luca Stealer Spreads Via a Phishing Microsoft Crypto Wallet Site
With the ever-increasing number of cyber threats, hackers and cybersecurity…
Trojan HotRat Is Distributed through Pirated Versions of Software and Games
Avast experts have warned that a new variant of AsyncRAT…
Gozi and IcedID Trojans Spread via Malvertising
Malvertising on Google Search is an unpleasant occurrence where malicious…
Vulnerability in WordPress Plugin WooCommerce Payments Is Actively Used to Hack Sites
Hackers use a vulnerability in the widely used WooCommerce Payments…
Fake Ads on Facebook Promote Scam AI Services
Facebook has been hit by a wave of fake ads…
FIN8 Updated Sardonic Backdoor to Deliver Noberus Ransomware
FIN8, an infamous group of cybercriminals, has updated its backdoor…
Citrix and Adobe Vulnerabilities Under Active Exploitation
Citrix was able to patch a zero-day vulnerability, while Adobe…
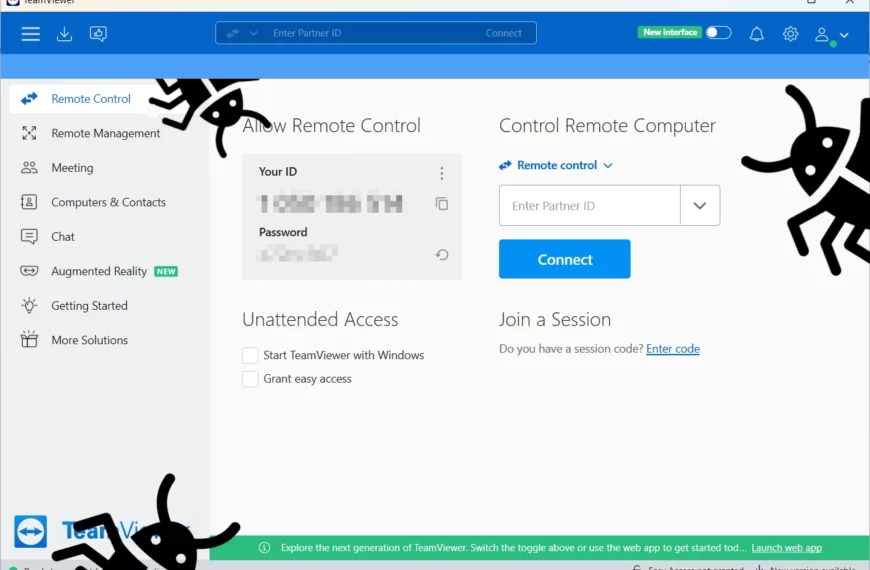
Trojanized TeamViewer Installer Spreads njRAT
Threat actors reportedly started using fake TeamViewer to distribute malware.…
Hundreds of Military and Intelligence Agencies Uploaded Data to VirusTotal
An employee of the Google-owned platform VirusTotal accidentally uploaded a…
WormGPT Helps Cybercriminals to Launch Sophisticated Phishing Attacks
SlashNext noticed that cybercriminals are increasingly using generative AI in…