A previously unknown payload of ransomware, that call itself WannaCry 3.0, targets Russian-speaking players of the Enlisted game. Hackers reportedly use a modified game installer and a spoofed official site to confuse unsuspecting users.
You might also be interested in this article One Year of Russian-Ukrainian War in Cybersecurity, or this: Stabbed in the back: Chinese Mustang Panda Cyberspies Attack Russian Officials.
Also information security specialists noted that Due to the sanctions, Russian hackers are looking for new ways to launder money.
How hackers mimic the Enlisted game
Trojanized versions of the game are distributed through fake sites, where the game installer comes with a ransomware that pretends to be the third version of the sensational WannaCry malware (the malware even changes the extensions of the affected files to .wncry).

Enlisted was released by Gaijin Entertainment in 2021 and has between 500,000 and a million active players every month. Since the game is free-to-play, the attackers were able to easily download the installer from the publisher’s website and modify it to distribute the malware to players.
WannaCry 3.0 Payload analysis
According to Cyble analysts who analyzed the threat, this supposedly new variant of WannaCry is actually based on an open-source Python locker Crypter created for educational purposes. The game installer downloaded from the fake site is named “enlisted_beta-v1.0.3.115.exe“, and when run, it dumps two executable files on the user’s disk: ENLIST~1 (the actual game) and enlisted (the malware’s Python launcher).
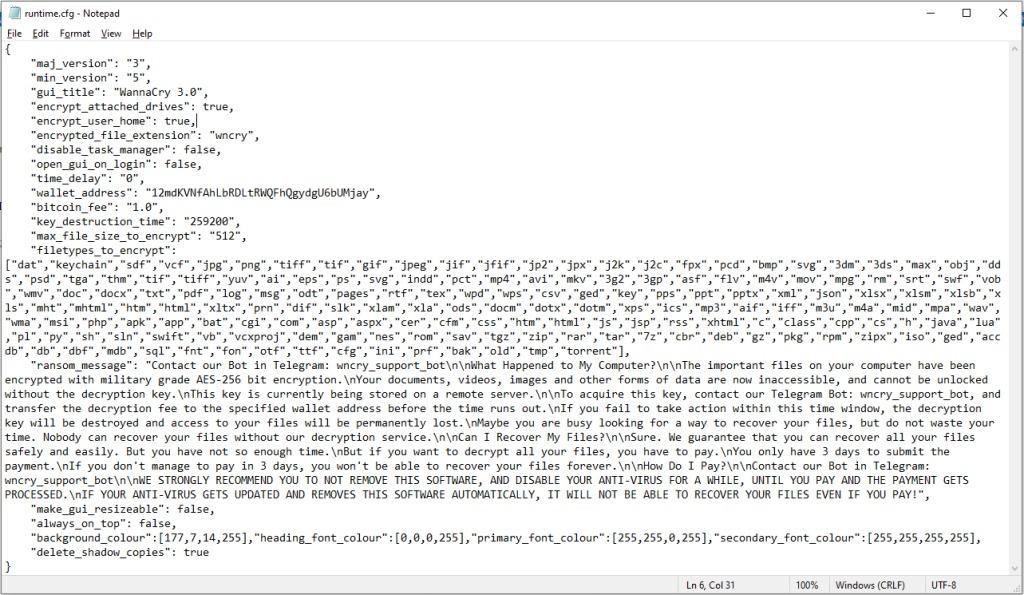
Upon initialization, the ransomware creates a mutex to avoid multiple running instances on the infected machine. It then parses its JSON config file to determine which file types to target, which directories to skip, which ransom note to generate, and which wallet address to enter to receive the ransom.
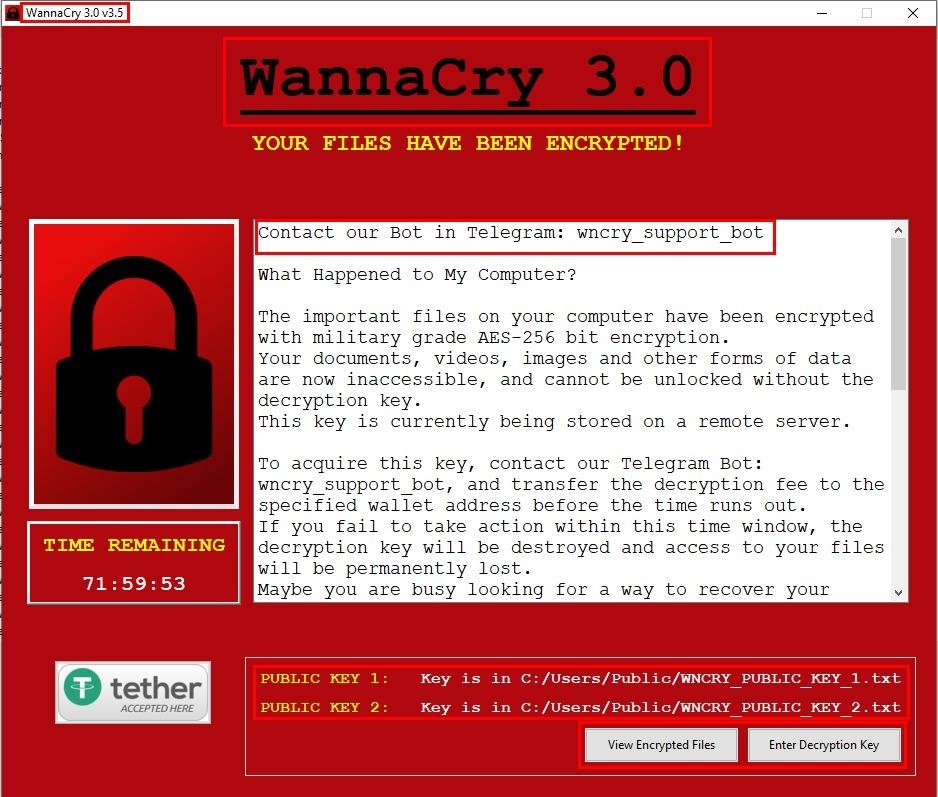
As a result, the ransomware scans the working directory looking for the key.txt file to use in the encryption step (if it does not exist, it creates it). The AES-256 algorithm is used for encryption, and as mentioned above, all locked files receive the .wncry extension.
Interestingly, the malware does not attempt to terminate processes or services, which is standard practice in modern lockers, but goes the usual way for ransomware and removes shadow copies to prevent data recovery.
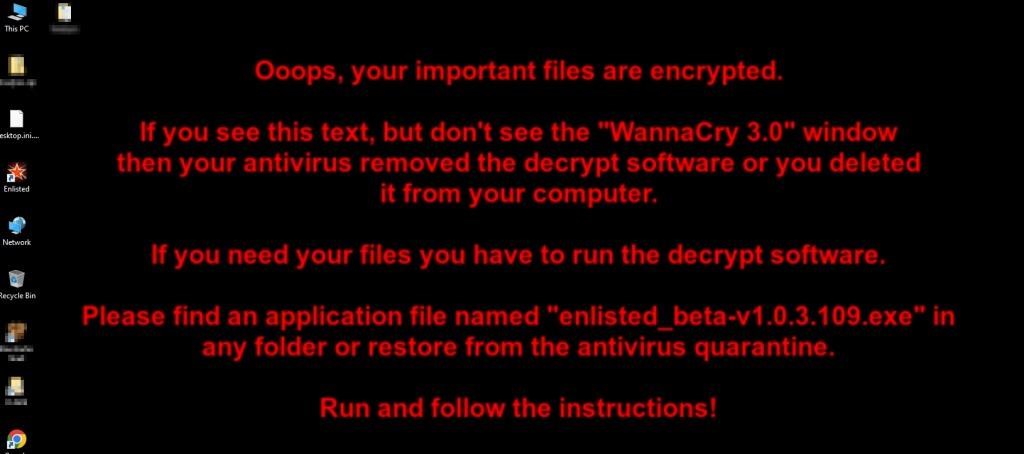
After verifying the process of encrypting files, the ransomware shows the victim a ransom note using a special application with a graphical interface for this and giving the victim three days to make a decision. In case the victim’s antivirus blocks the display of the ransom note, the ransomware also changes the background image on the user’s work slot.
What then?
The researchers note that the hackers do not use the Tor website, instead suggesting that victims use a Telegram bot to contact them. According to experts, many popular online shooters may now be unavailable to Russian users, so Enlisted has become an alternative for them. If the attackers have already paid attention to this, they can probably create other fake sites for similar games with Russian localization.
Well, what can I say? Being Russian-speaking now is not something that is not fashionable, but also dangerous. However, cybercriminals must be detected and punished, despite extenuating circumstances.




