An infamous Remcos RAT reportedly started targeting South Korean users through the files shared on Webhards platform. By baiting users with cracked software and adult content, hackers manage to install a malicious script that in turn downloads and runs the dangerous remote access trojan.
Remcos RAT Uses Webhards to Spread
Recent research of South Korean cybersecurity firm AhnLab shares its observations regarding a new Remcos RAT spreading campaign. The company names Webhards as a source of choice for this malware to infiltrate user devices. Webhards is a file sharing platform, popular among computer pirates and people who seek free content. It may be used for legitimate purposes, though a selection of analysts name it a popular source of malware, along with torrents.
In the case of Remcos RAT, hackers use “hot topics” – either adult content or cracked versions of new games to make the user download the infected package. Then, the publication on the aforementioned site asks to run a Game.exe file, that is present in the downloaded archive. Upon running the executable file, a chain of VBS scripts are executed to download the final payload.
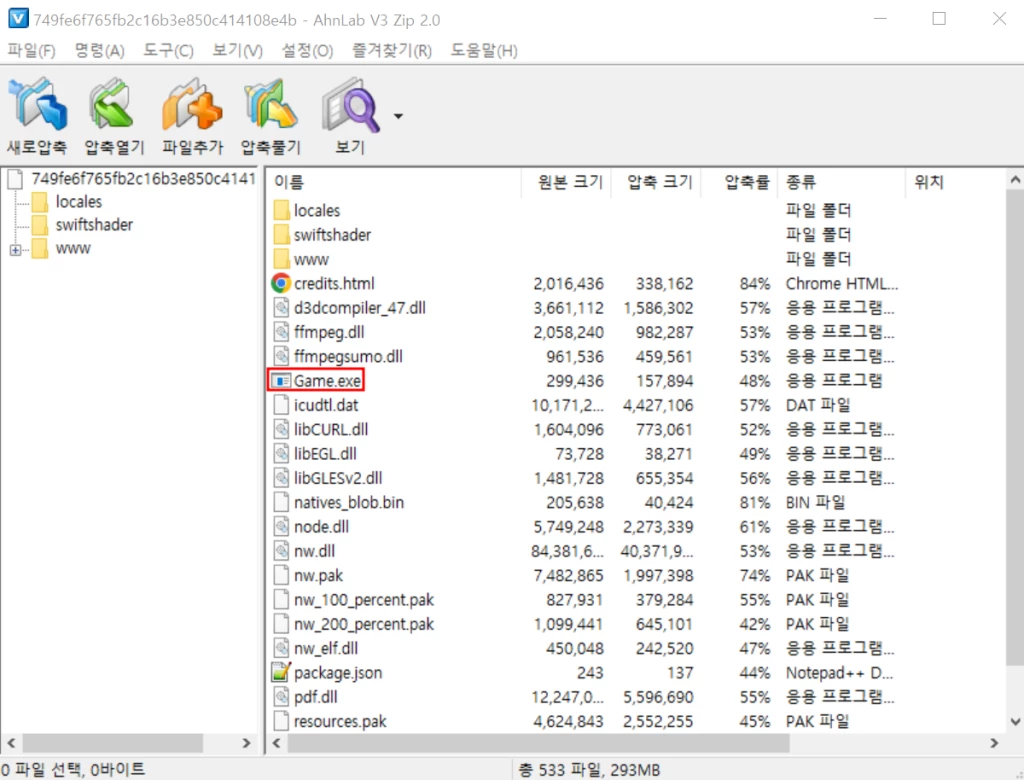
Upon downloading, another set of scripts injects Remcos into a system process called ServiceModelReg.exe. This is a built-in console utility that is, in fact, used only during the system installation and has no further application. Well, until this instance of Remcos finds its way to the machine, apparently.
What is Remcos RAT?
Remcos is a remote access trojan, marketed as a legit remote access tool by German firm BreakingSecurity. Released in 2019, it has become particularly popular in 2020 and 2021, when threat actors were using Covid-themed emails to spread it. Later though, its activity has become much more moderate, averaging at 30 samples per day during 2023.
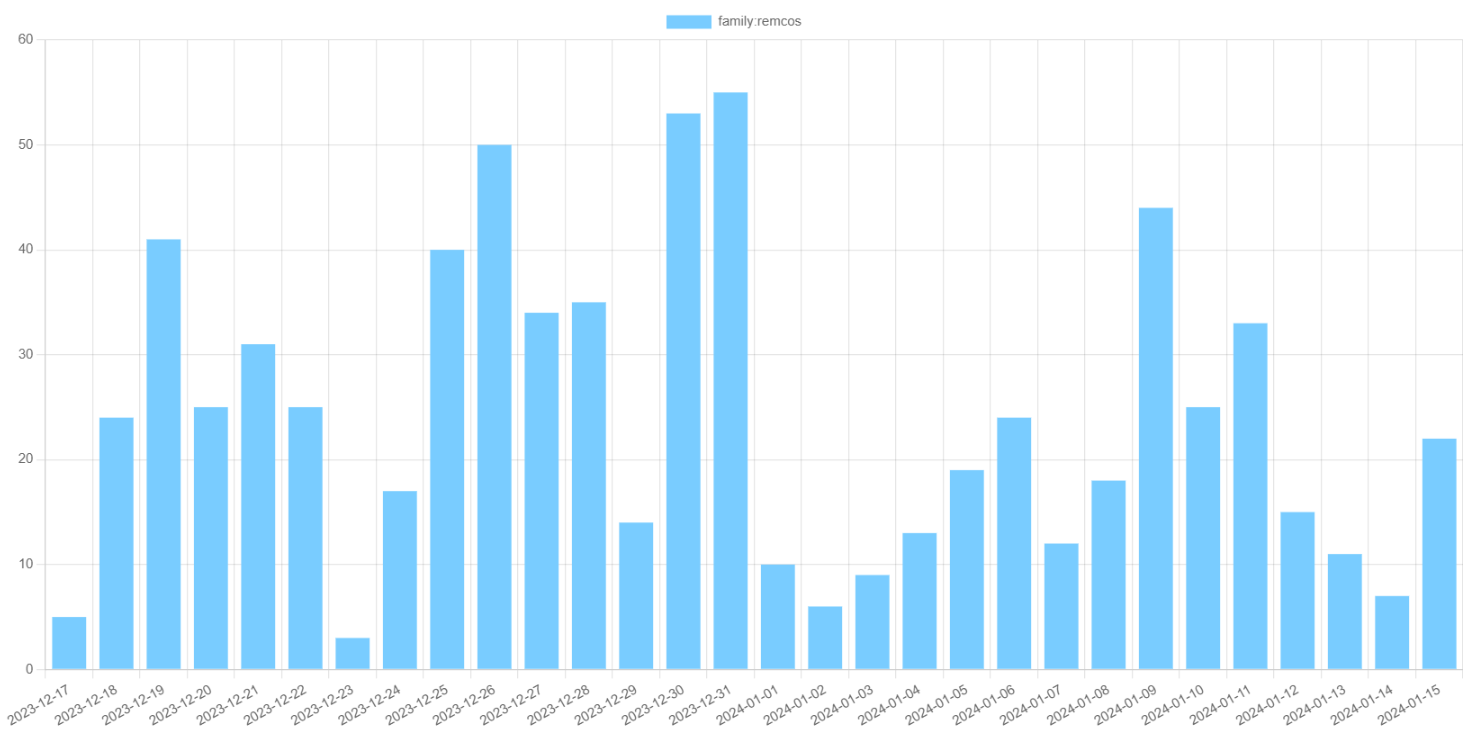
For functionality, this malware is a classic example of RAT: Remcos provides full-featured remote access to the infected system, including access to system menus and file system. Additionally, it is capable of recording the screen, taking screenshots and setting the activity alarm. To identify target systems from each other, malware collects some basic information – OS version, date, time, and some basic hardware info.
How to protect against threats?
By looking at the ways the malware spreads you can already get the answer on how to protect yourself. In the case of Remcos, the obvious answer is to avoid cracked software. As it is not just a malware risk but also a copyright infringement, avoiding it is pretty much recommended. This is especially relevant for websites that are known for being used for malware distribution.
For an additional, passive layer of protection, you can have anti-malware software running in the background. A modern, well-stocked antivirus can protect you from any attack, regardless of the type of malware. GridinSoft Anti-Malware is the one you can rely on – its detection system offers exceptional protection in both proactive and reactive approaches.





