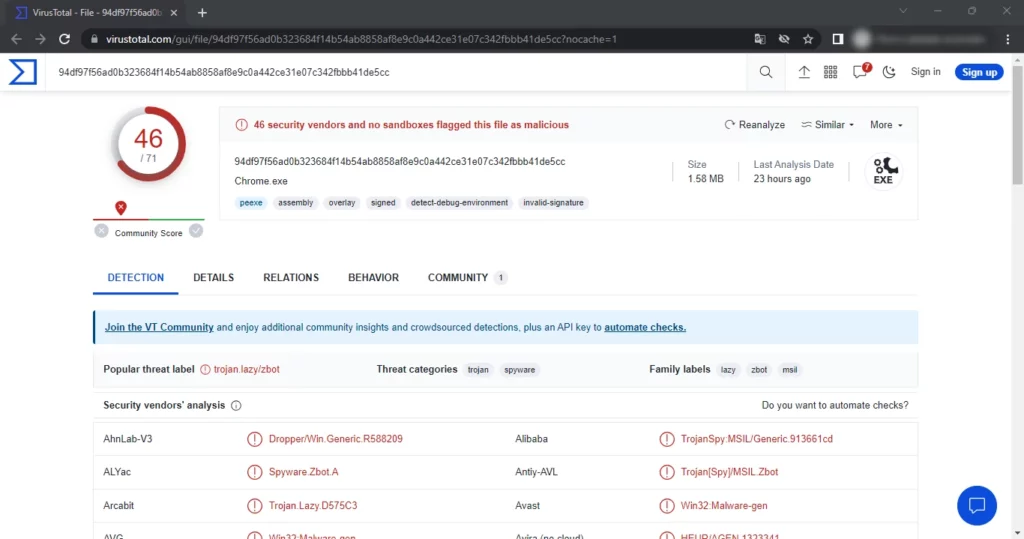
Researchers have discovered a new form of malware called RedEnergy Stealer. It is categorized as Stealer-as-a-Ransomware but is not affiliated with the Australian company Red Energy.
A malware called RedEnergy stealer uses a sneaky tactic to steal sensitive data from different web browsers. Its fundamental spreading way circulates fake updates – pop-ups and banners that bait the user to install what appears to be the malicious payload. RedEnergy also has multiple modules that can carry out ransomware activities. Despite using common method names, the malware has kept its original name. RedEnergy is classified as Stealer-as-a-Ransomware because it can function as a stealer and ransomware.
What is RedEnergy Malware?
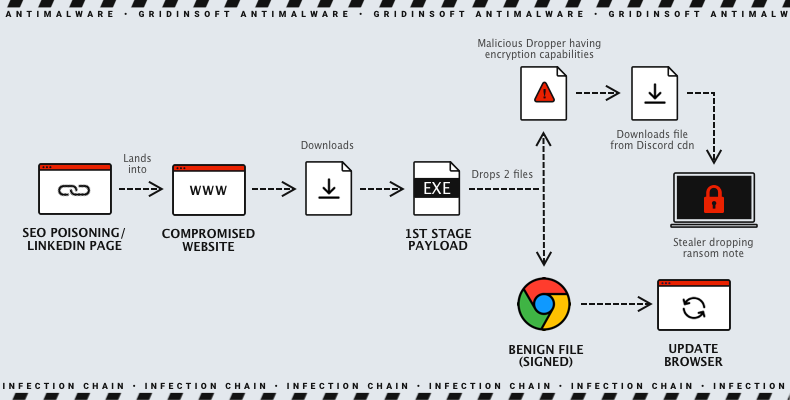
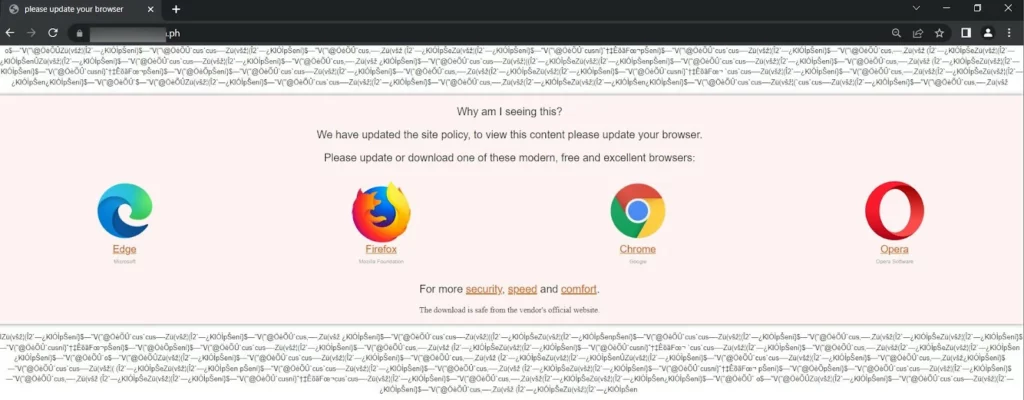
RedEnergy is a malware designed to appear as a legitimate browser update, tricking users into downloading and installing it. It imitates well-known browsers like Google Chrome, Microsoft Edge, Firefox, and Opera, and once triggered, it deposits four files (two temporary files and two executables) onto the targeted system. One of these files contains a malicious payload and initiates a background process. The load displays an insulting message to the victim once executed.
Also, RedEnergy is malicious software that remains on an infected system even after restart or shutdown. This allows it to continue its harmful activities uninterrupted. As part of its operation, it also encrypts the victim’s data and adds the “.FACKOFF!” extension to all the encrypted files. It then demands payment from the victim to restore access to the files through a ransom message (“read_it.txt“) and changes the desktop wallpaper.
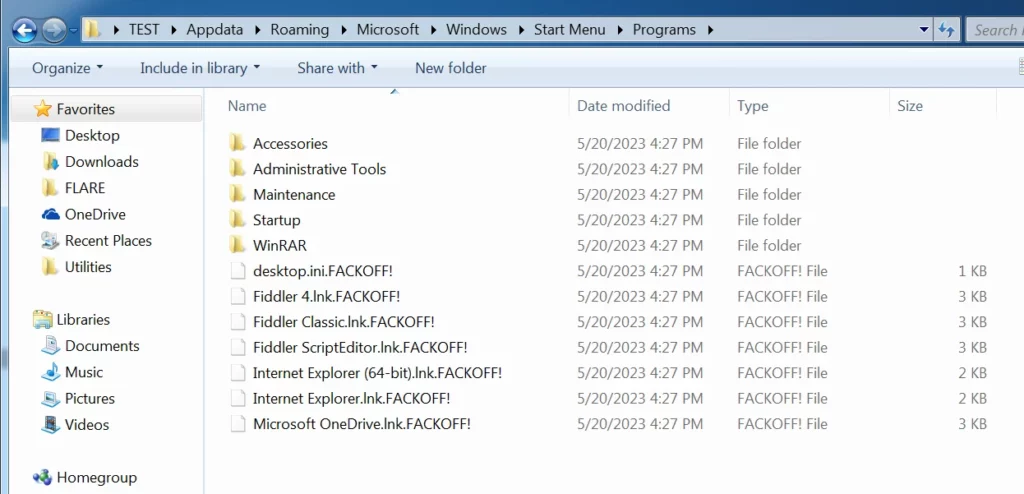
One of the things that the ransomware does is delete data from the shadow drive, which means that any backups are erased. In addition, the malicious software changes the desktop.ini file, which contains basic settings for file system folders. By doing this, RedEnergy can alter the appearance of the folders, making it easier to hide its activities on the system. Lastly, RedEnergy can also steal data from different web browsers, potentially giving it access to personal information, login details, financial data, online activities, session-related information, and other essential data.
Threat Summary
| Name | RedEnergy Stealer-as-a-Ransomware |
| Threat Type | Information stealer, ransomware |
| Encrypted Files Extension | .FACKOFF! |
| Ransom Demanding Message | read_it.txt |
| Cyber Criminal Contact | [email protected] |
| Ransom Amount | 0.005 BTC |
How does RedEnergy Malware work?
This threat campaign uses a deceitful redirection technique to trick users. When users try to access the targeted company’s website through their LinkedIn profile, they are unknowingly sent to a malicious website. On this website, they are asked to download what seems like a legitimate browser update, presented as four different browser icons. However, this is a trap, and the unsuspecting user downloads an executable file called RedStealer instead of an actual update.
A deceptive threat campaign uses a misleading download domain called www[.]igrejaatos2[.]org. The domain appears as a ChatGpt site, but it’s counterfeit and aims to trick victims into downloading a fake offline version of ChatGpt. Unfortunately, the zip file contains the same malicious executable as before, and victims unknowingly acquire it upon downloading.
How to avoid installation of RedEnergy Malware?
Individuals and organizations must exercise extreme caution when accessing websites, particularly those linked to LinkedIn profiles. Verifying browser updates’ authenticity and being wary of unexpected file downloads are paramount to protecting against such malicious campaigns.
To prevent negative consequences, there are several essential steps to take:
- Updating your operating system and software regularly.
- Essential to be cautious when dealing with email attachments or suspicious links, especially from unknown sources.
- Consider using reliable antivirus or anti-malware software to provide extra protection and conduct regular system scans.
- Avoid downloading files from untrusted websites and be wary of pop-up ads or misleading download buttons that may contain harmful content.





