In the latest update release, Ivanti disclosed the selection of critical vulnerabilities in their Endpoint Manager software. Among the fixed flaws, there are 3 of high severity, with a huge exploitation potential and impact to the affected environment. The company urges customers to install the update as soon as possible.
Critical Ivanti Endpoint Manager Vulnerabilities Uncovered
The huge list attached to the patch note reveals a grand total of 18 vulnerabilities, with most of them having high severity rating (7.2 CVSS score being the lowest). A lot of these flaws lead to SQL injection (CWE-89), though require either high privileges at the start, or other less-than-common circumstances. But among them, there are two flaws which raise much bigger concern.
First up is the CVE-2024-50330, one of the mentioned SQLi vulnerabilities, though it requires no authentication at all. Moreover, with the correctly crafted command, adversaries can achieve remote code execution – a rare yet still highly dangerous outcome of SQL injection attacks. This explains the notably high CVSS rating of 9.8.
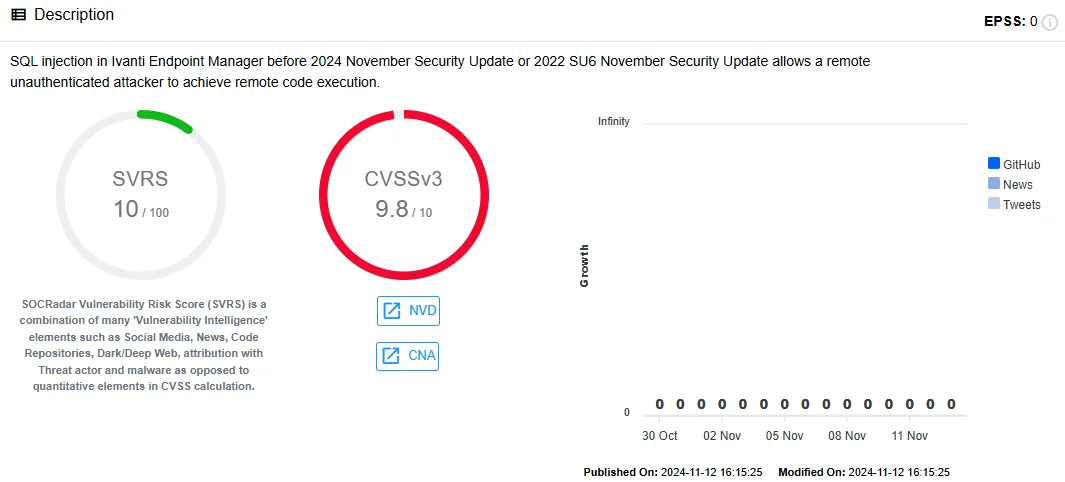
The other vulnerability is CVE-2024-50323, which allows for path traversal attack. In simple words, such flaws can grant the hacker access to directories that should normally be inaccessible from outside the network. However, as the software does not neutralize the query properly, it is possible to force the program into this unwanted behavior. As this specific vulnerability does not require adversaries to have any access privileges, it is quite easy to abuse in real-world scenarios.
Though, it would be shortsighted to consider only these two flaws a real danger, and the rest 16 of them just placeholders in the patch note. With a proper combination of vulnerabilities, hackers can extend the potential of even the most severe flaw from the list. Also, considering that we are talking about environment management software, any adversary activity here has huge potential, both in terms of malware injection and lateral movement.
Ivanti Releases Patches, Update Now
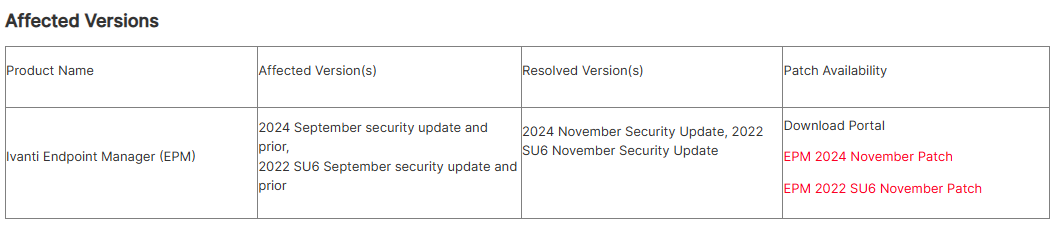
The good thing in all this story is that the flaws were published by the software vendor itself, and together with updates. Ivanti offers fixes for their EPM 2024 and 2022 SU6, with the detailed instructions on how to get them installed. Among vulnerable versions, the developer names 2024 September update and prior, along with the 2022 SU6 September update.
Another fortunate part of the story is that there are no known exploitation cases of any of these vulnerabilities. Software vendors rarely make such statements unfounded, so it is a great relief for all the users of Ivanti Endpoint Management. Though, I’d like to remind that when the flaw becomes public, chances of its active exploitation increase dramatically, meaning that it is better to get updates as soon as possible.