RansomEXX ransomware operators attacked a large Taiwanese computer hardware manufacturer Gigabyte. The hackers are currently threatening to release more than 112GB of data stolen from the company if it does not pay the ransom.
The attack took place in the middle of last week and forced the company to partially shut down Taiwanese systems. The incident is known to have affected several Gigabyte sites, including the support site and parts of the Taiwanese site.
Gigabyte officials have already confirmed to the media that the company was affected by the cyberattack, but stressed that the incident affected only a small number of servers. Having discovered anomalous activity, Gigabyte specialists promptly took the remaining IT systems offline and notified law enforcement agencies about the incident.
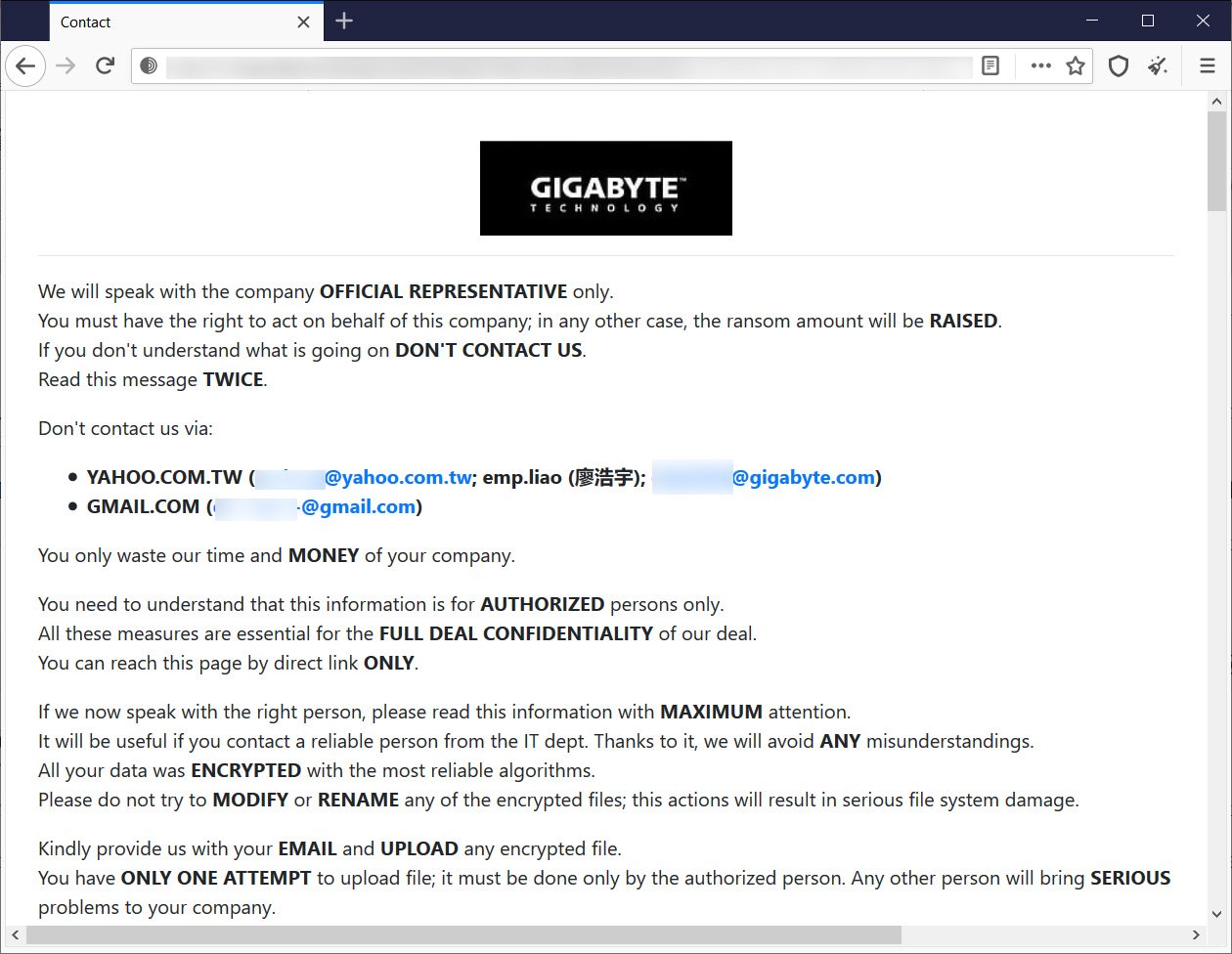
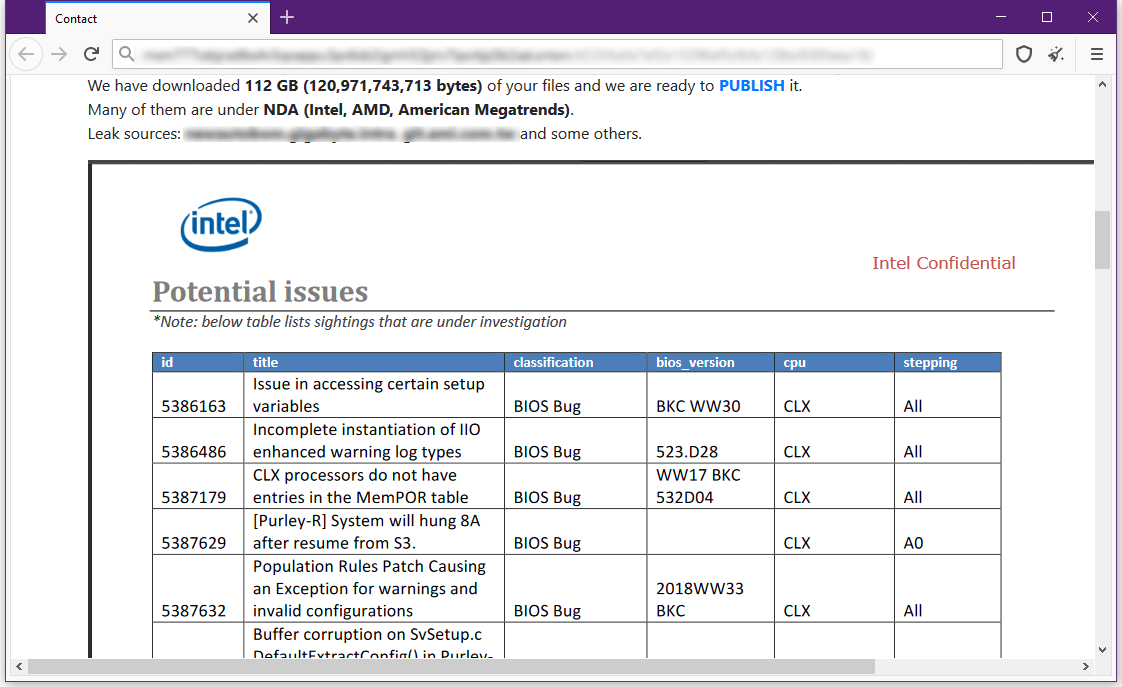
Bleeping Computer reports that the ransomware group RansomEXX is behind this attack. The fact is that its own source provided the publication with a link to a closed hacker page, created specifically for Gigabyte, where hackers claim that they stole 112 GB of data during the attack.
To prove their point, the attackers have already shared screenshots of four documents protected by non-disclosure agreements (including a debug document from American Megatrends and an Intel document entitled Potential Issues).
What is known about RansomEXX?
The ransomware RansomEXX started its activity under the name Defray in 2018, but in June 2020 it was renamed RansomEXX and became more active. Like other ransomware, RansomEXX can hack into the network using Remote Desktop Protocol, exploits, or stolen credentials. By gaining access to the network, RansomEXX operators will collect more credentials, gradually gaining control of the Windows domain controller. Cybercriminals will steal data from unencrypted devices.
RansomEXX not only targets Windows devices, but can also encrypt data on Linux virtual machines running VMware ESXi servers.
Over the past month, the RansomEXX gang has become more active, recently attacking the municipal authorities of the Lazio region in Italy and the Ecuadorian state corporation, Corporation Nacional de Telecommunication (CNT). Other high-profile attacks by the ransomware gang include attacks on Brazilian government networks, the aircraft manufacturer Embraer, the Texas Department of Transportation (TxDOT), Konica Minolta, IPG Photonics and Tyler Technologies.
I also talked about the fact that The new BlackMatter ransomware was created by the authors of recently “closed” DarkSide.