Just when you thought cybercriminals couldn’t get more creative, they’ve found a way to weaponize our collective obsession with AI. Meet Noodlophile Stealer, a newly discovered information-stealing malware that’s turning the AI revolution into a data theft operation. Because apparently, even malware developers want to ride the artificial intelligence wave.
- The AI Bait: Too Good to Be True
- How the Scam Works
- Meet Noodlophile: The New Kid on the Block
- The XWorm Connection
- Technical Analysis: Under the Hood
- The Vietnamese Connection
- Why This Campaign is Different
- Signs of Infection
- How to Remove Noodlophile Stealer
- Prevention: Staying Safe in the AI Era
- The Bigger Picture: AI as the New Attack Vector
- Industry Response
- The Bottom Line
| Name | Noodlophile Stealer, Noodlophile Malware |
| Threat Type | Information Stealer, Remote Access Trojan |
| Disguise | AI video generation platforms, fake content creation tools |
| What It Steals | Browser credentials, cryptocurrency wallets, session tokens, personal files |
| Distribution | Facebook groups (62K+ views), fake AI websites, viral social media campaigns |
| Communication | Telegram bot API for data exfiltration |
| Additional Payload | XWorm 5.2 remote access trojan |
| Risk Level | High (financial loss, account takeover, persistent remote access) |
The AI Bait: Too Good to Be True
Security researchers at Morphisec have uncovered a sophisticated campaign that exploits public enthusiasm for AI-powered content creation. Instead of the usual suspects like cracked software or phishing emails, cybercriminals are now building convincing fake AI platforms that promise cutting-edge video and image generation capabilities.
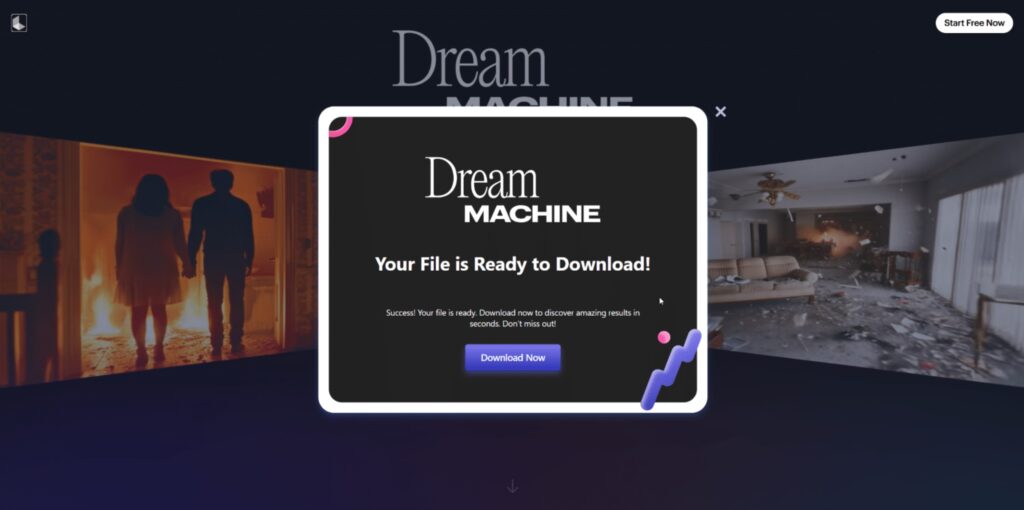
The operation starts innocently enough. Victims discover these fake AI platforms through Facebook groups boasting over 62,000 views, where users eagerly share links to “revolutionary” AI tools for video editing and content creation. The social engineering is brilliant in its simplicity: who doesn’t want access to the latest AI technology for free?
How the Scam Works
The attack chain is deceptively straightforward:
- Discovery: Users find fake AI platforms through viral Facebook posts and groups
- Engagement: Victims upload their images or videos, believing they’re using legitimate AI tools
- The Hook: After “processing,” users are prompted to download their enhanced content
- The Payload: Instead of AI-generated videos, they download malware disguised as their processed content
The downloaded file typically comes as a ZIP archive with names like “VideoDreamAI.zip” containing an executable masquerading as a video file: “Video Dream MachineAI.mp4.exe”. The filename exploits whitespace and misleading extensions to appear harmless, but it’s actually a sophisticated malware delivery system.
Meet Noodlophile: The New Kid on the Block
Noodlophile Stealer represents a new addition to the malware ecosystem. Previously undocumented in public malware trackers, this trojan combines multiple malicious capabilities:
Data Theft Capabilities
- Browser credential harvesting from all major browsers
- Cryptocurrency wallet exfiltration targeting popular wallets
- Session token theft for account takeover attacks
- File system reconnaissance to identify valuable data
Communication Method
Like its cousin Octalyn Stealer, Noodlophile uses Telegram bots for data exfiltration. The malware communicates through Telegram’s API, making detection more challenging since the traffic appears legitimate to most monitoring tools.
The XWorm Connection
In many cases, Noodlophile doesn’t work alone. Researchers discovered that the malware often deploys alongside XWorm 5.2, a remote access trojan that provides attackers with deeper system control. This combination creates a particularly dangerous infection that can:
- Steal credentials and sensitive data (Noodlophile)
- Maintain persistent remote access (XWorm)
- Propagate to other systems on the network
- Deploy additional malware payloads
Noodlophile Stealer attack flow analysis
Technical Analysis: Under the Hood
Security researchers discovered that Noodlophile employs sophisticated obfuscation techniques to evade detection. The malware uses approximately 10,000 repeated instances of meaningless operations (like “1 / int(0)”) to break automated analysis tools while remaining syntactically valid.
Key Technical Indicators
The malware communicates with command-and-control servers through several domains and IP addresses:
- C2 Domains: lumalabs-dream[.]com, luma-dreammachine[.]com
- Telegram Integration: Uses bot tokens for data exfiltration
- XWorm C2: 103.232.54[.]13:25902
- File Names: Various ZIP archives with AI-themed names
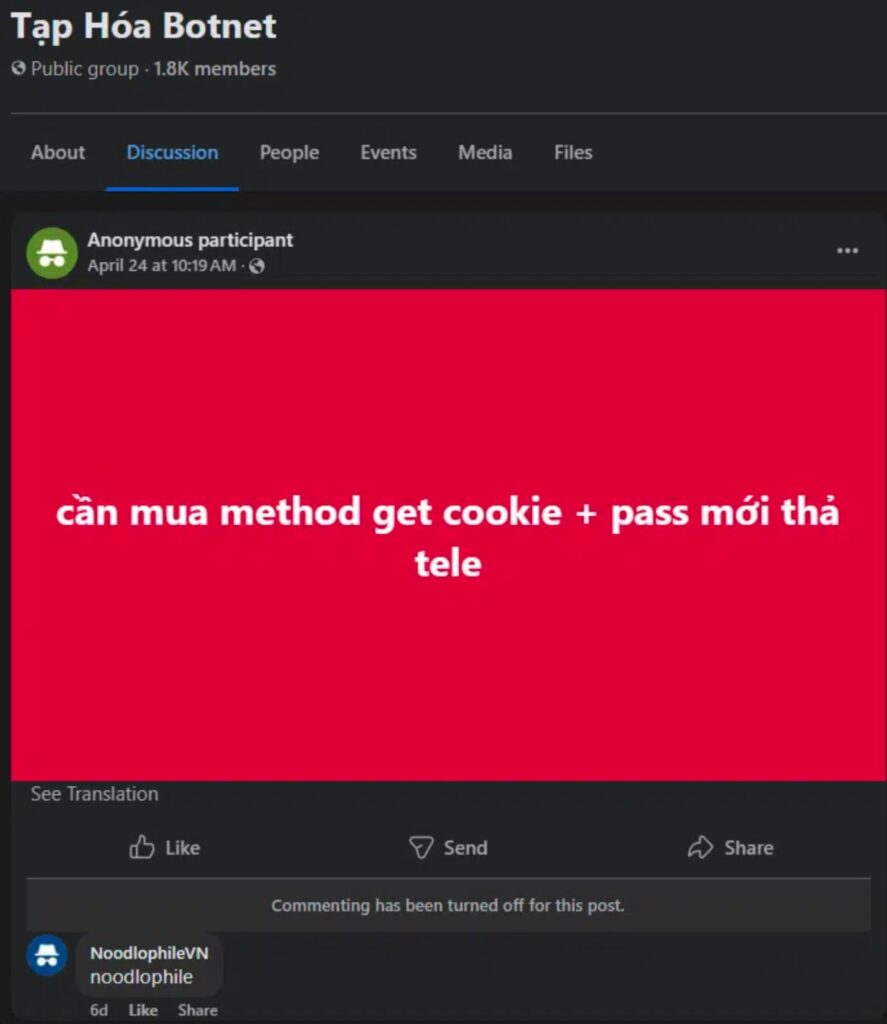
The Vietnamese Connection
Investigation into the malware’s origins suggests the developer is likely of Vietnamese origin, based on language indicators and social media profiles. The threat actor has been observed promoting this “new method” in cybercrime forums, advertising Noodlophile as part of malware-as-a-service (MaaS) schemes alongside tools labeled “Get Cookie + Pass” for account takeover operations.
Why This Campaign is Different
What makes this campaign particularly concerning is its exploitation of legitimate technological trends. Unlike traditional malware campaigns that rely on obviously suspicious lures, this operation targets users genuinely interested in AI technology – a demographic that includes creators, small businesses, and tech enthusiasts who might otherwise be security-conscious.
The use of Facebook groups with tens of thousands of views demonstrates the campaign’s reach and sophistication. By leveraging social proof and viral marketing techniques, the attackers have created a self-sustaining distribution network that continues to attract new victims.
Signs of Infection
If you’ve recently downloaded “AI-generated” content from suspicious platforms, watch for these warning signs:
- Unexpected network activity, especially connections to Telegram servers
- Browser settings or saved passwords changing unexpectedly
- Cryptocurrency wallet balances decreasing
- Unknown processes running with network access
- Antivirus alerts mentioning Noodlophile or XWorm
- Unusual system performance or unexpected file modifications
How to Remove Noodlophile Stealer
If you suspect your system is infected with Noodlophile Stealer:
Immediate Actions
- Disconnect from the internet to prevent further data exfiltration
- Boot into Safe Mode to limit malware functionality
- Run a complete system scan with updated anti-malware software

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.

Post-Removal Steps
- Change all passwords immediately, especially for financial and cryptocurrency accounts
- Enable two-factor authentication on all critical accounts
- Monitor financial accounts for unauthorized transactions
- Check cryptocurrency wallets and consider transferring funds to new addresses
- Review browser extensions and remove any suspicious additions
Prevention: Staying Safe in the AI Era
As AI technology continues to evolve, so will the tactics used to exploit our enthusiasm for it. Here’s how to protect yourself:
Red Flags to Watch For
- Too-good-to-be-true AI tools offering premium features for free
- Platforms requiring file uploads before showing capabilities
- Social media promotion through viral posts rather than official channels
- Download requirements for viewing “processed” content
- Executable files disguised as media content
Best Practices
- Stick to well-known, legitimate AI platforms with verified credentials
- Be skeptical of AI tools promoted through social media groups
- Never download executable files when expecting media content
- Use reputable antivirus software with real-time protection
- Keep your operating system and browsers updated
The Bigger Picture: AI as the New Attack Vector
The Noodlophile campaign represents a significant shift in cybercriminal tactics. As AI becomes mainstream, we can expect to see more attacks leveraging public interest in artificial intelligence. This trend mirrors how cybercriminals previously exploited interest in cryptocurrency, social media, and mobile apps.
The sophistication of these fake AI platforms – complete with convincing interfaces and viral marketing campaigns – demonstrates that cybercriminals are investing significant resources in this new attack vector. Organizations and individuals need to adapt their security awareness training to address AI-themed threats.
Industry Response
Security vendors are already updating their detection capabilities to identify Noodlophile and similar AI-themed threats. However, the rapid evolution of these campaigns means that user education remains the first line of defense.
The cybersecurity community is also working to identify and take down the infrastructure supporting these campaigns, including the fake domains and social media groups used for distribution.
The Bottom Line
Noodlophile Stealer serves as a wake-up call about the dark side of AI adoption. While artificial intelligence offers incredible opportunities for creativity and productivity, it also provides new avenues for cybercriminals to exploit our enthusiasm and trust.
The key to staying safe is maintaining healthy skepticism, especially when encountering “revolutionary” AI tools that seem too good to be true. Remember: legitimate AI companies don’t typically distribute their software through viral Facebook posts or require you to download suspicious executables.
If you suspect your system has been compromised by Noodlophile or any other malware, don’t wait. Download GridinSoft Anti-Malware and run a complete system scan immediately.
In the age of AI, the old cybersecurity adage remains true: if something seems too good to be true, it probably is. Stay vigilant, stay informed, and remember that the most sophisticated AI tool is still your own critical thinking.





