Check Point analysts have discovered a new ransomware, Rorschach ransomware that has already been used to attack an unnamed American company.
This malware is notable for its extremely high speed of file encryption and the fact that it is deployed using a signed component of commercial security software.
Check Point calls this threat “one of the fastest ransomware” as Rorschach is even faster than LockBit 3.0.
Let me remind you that we also wrote that New Cuba Ransomware Variant Involves Double-Extortion Scheme, and also that New Pay2Key ransomware encrypts corporate networks in just an hour.
Also the media reported that New Prestige Ransomware Attacks Polish and Ukrainian Organizations.
The researchers say that the ransomware is delivered using a side-loading DLL technique through a signed component in the Cortex XDR in the Palo Alto Networks product. The attackers used the Cortex XDR Dump Service Tool (cy.exe) version 7.3.0.16740 to download the Rorschach loader and injector (winutils.dll), which resulted in the config.ini ransomware payload being launched into the Notepad process.
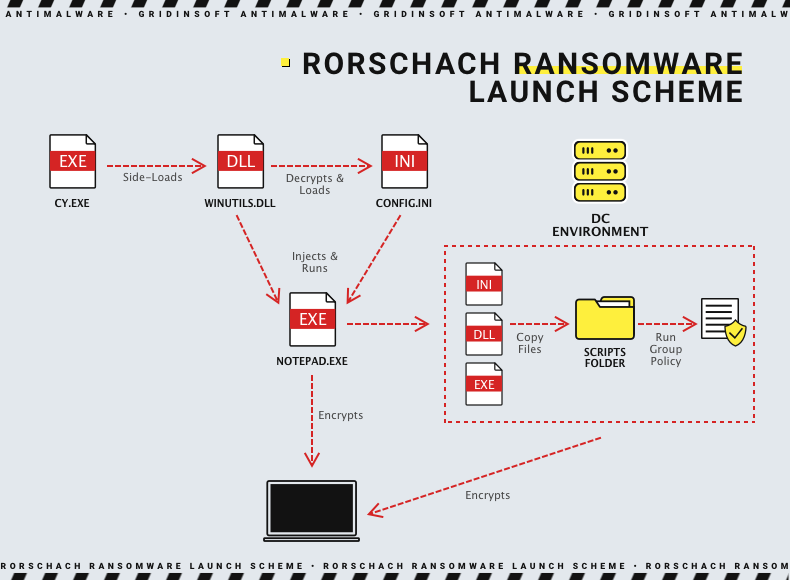
It is noted that the loader file is protected from UPX-style analysis, while the main payload is protected from reverse engineering and detection by virtualizing parts of the code using VMProtect.
Check Point experts warn that the ransomware creates a group policy on a Windows domain controller and can independently propagate to other hosts in the domain.
After compromising the victim’s computer, the malware erases four Application, Security, System, and Windows Powershell logs to cover its tracks.
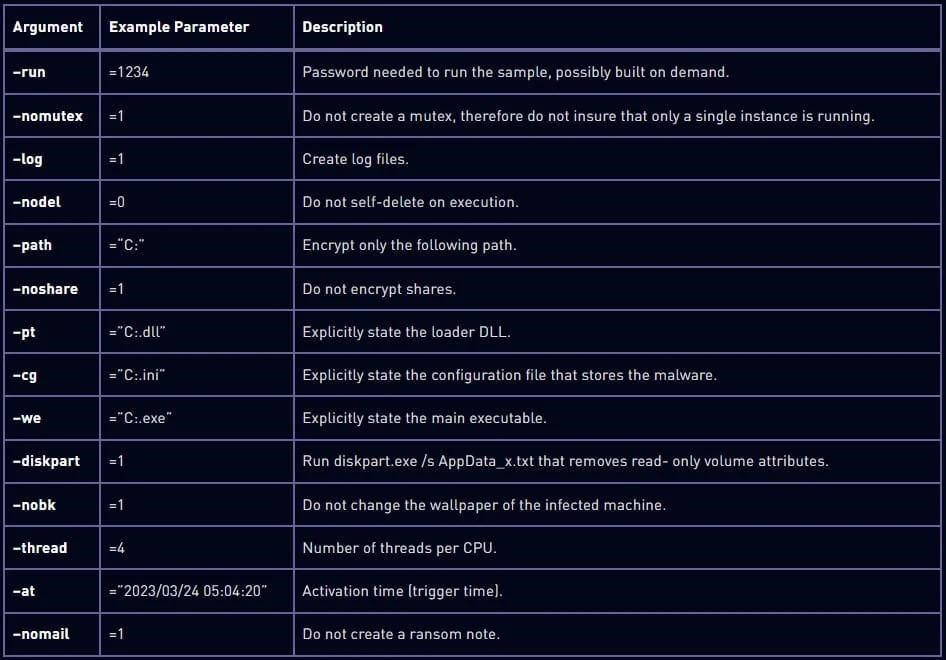
Although Rorschach’s configuration is generally hard-coded, the ransomware supports command-line arguments that greatly enhance its functionality. Below are some of them.
Rorschach will start encrypting data only if the infected machine does not work in the language of any of the CIS countries. The encryption scheme combines the curve25519 and eSTREAM hc-128 algorithms, using discontinuous encryption, meaning the malware encrypts files only partially, which increases its speed.
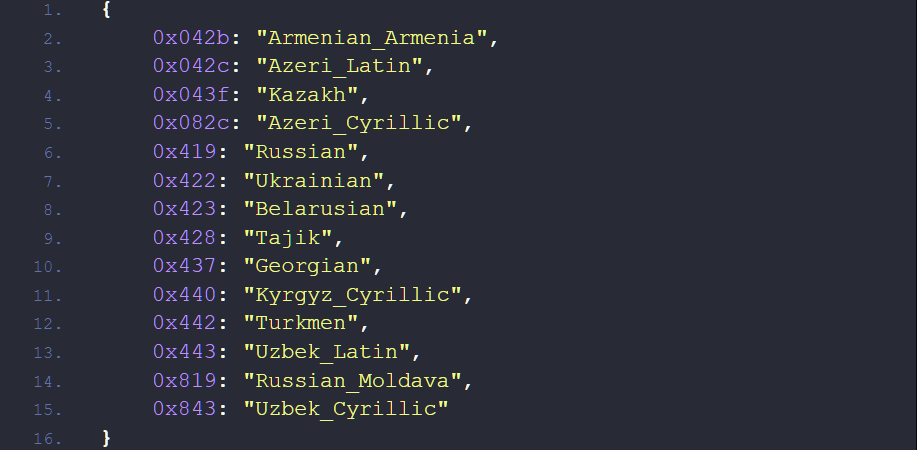
Languages that stop malware
The researchers note that the Rorschach encryption procedure demonstrates “a highly efficient implementation of stream distribution through I / O completion ports.”
To determine the speed of Rorschach encryption, experts conducted a test using 220,000 files on a machine with a 6-core processor. It took malware 4.5 minutes to encrypt the data, while LockBit 3.0, until recently considered the fastest ransomware, completed the same task in 7 minutes.
Check Point summarizes that Rorschach appears to have incorporated the best features of some of the leading ransomware programs previously leaked (Babuk, LockBit 2.0, DarkSide).




