Experts from the FBI, the US Department of Homeland Security (DHS CISA), the Australian Cybersecurity Center (ACSC), and the UK National Cybersecurity Center (NCSC) have published joint security advisories that list the most attacked and most popular vulnerabilities among criminals in 2020 and 2021.
Cybercriminals continue to exploit well-known, often old, software vulnerabilities against a wide range of targets, including organizations in the public and private sectors around the world.the experts write.
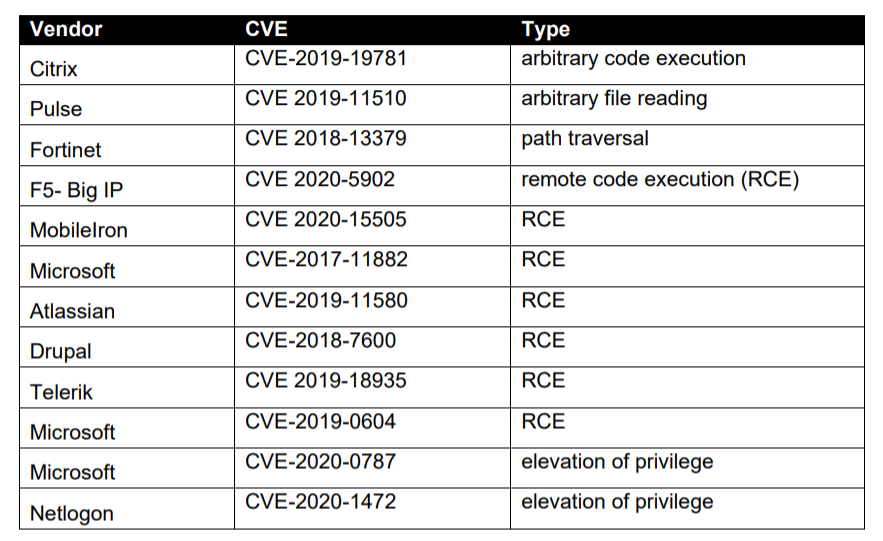
Based on data collected by the US government, most of the attacked vulnerabilities were discovered after early 2020, and many of the bugs are clearly related to the widespread transition to remote work. As a result, the four vulnerabilities most commonly exploited in 2020 were related to remote work, VPN and cloud services.
In 2021, attackers continued to target vulnerabilities in perimeter devices. Among the vulnerabilities that were actively exploited in 2021 were problems in Microsoft products, Pulse, Accellion, VMware and Fortinet.law enforcement officials say
As a result, the list of the most “popular” bugs of 2021 looks like this:
- Microsoft Exchange Server: CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, and CVE-2021-27065 (ProxyLogon vulnerabilities);
- Pulse Secure: CVE-2021-22893, CVE-2021-22894, CVE-2021-22899 and CVE-2021-22900;
- Accellion: CVE-2021-27101, CVE-2021-27102, CVE-2021-27103 and CVE-2021-27104;
- VMware: CVE-2021-21985;
- Fortinet: CVE-2018-13379, CVE-2020-12812, and CVE-2019-5591.
CISA, ACSC, NCSC and FBI believe that public and private organizations around the world remain vulnerable to compromise as a result of the exploitation of the listed CVEs. Attackers are likely to continue to exploit old and known vulnerabilities (such as CVE-2017-11882 affecting Microsoft Office) as long as they remain effective and systems do not receive patches. Attackers’ exploitation of known vulnerabilities complicates the attribution of attacks, lowers costs and minimizes risks, since [hackers] do not invest in developing 0-day exploits for their own use, which they risk losing if they become known, ” the experts conclude.
Let me remind you that I also wrote that the FBI and NSA release a statement about attacks by Russian hackers.