Recorded Future analysts have discovered a new hack group accompanying the BlackMatter ransomware that attacks large companies and combines the “best” features of the now defunct DarkSide and REvil.
Researchers say the group is currently recruiting “partners” through announcements on hacker forums Exploit and XSS.
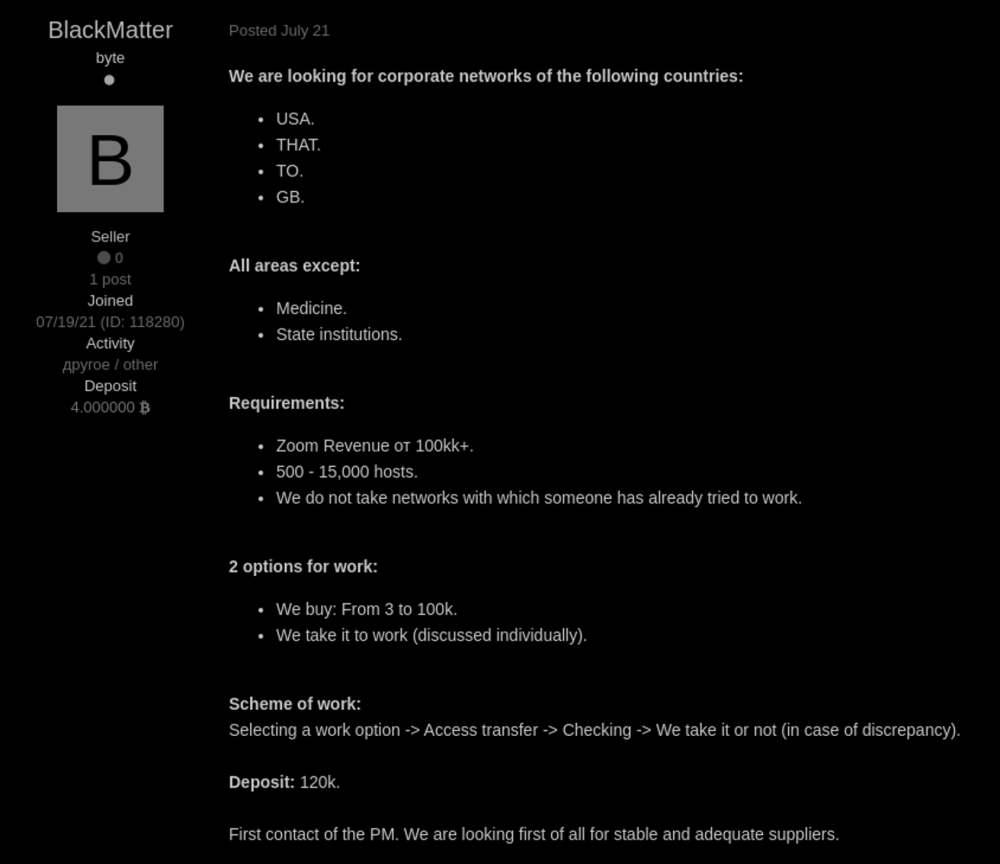
Although any advertising related to ransomware has been banned on these sites since May 2021, BlackMatter members do not advertise Ransomware-as-a-Service (RaaS), but advertisements for finding “initial access brokers”, that is, people who have access to compromised corporate networks.
According to the announcement, BlackMatter is only interested in working with brokers who can provide access to the networks of large companies, whose income is $100 million per year or more. Such a network must have between 500 and 15,000 hosts and must be located in the United States, United Kingdom, Canada, or Australia.
Hackers write that they are willing to pay up to $100,000 for exclusive access to any of the suitable networks.
The members of the group boast that they can encrypt data in different versions of operating systems and architectures. Including: Windows (via SafeMode), Linux (Ubuntu, Debian, CentOS), VMWare ESXi 5+, as well as NAS Synology, OpenMediaVault, FreeNAS and TrueNAS.
Like most modern ransomware, the BlackMater group has already launched its own data leak site, where hackers intend to publish information stolen from victims if the hacked company does not agree to pay the ransom for decrypting files. So far, the resource is empty, but BlackMatter announced themselves only this week and have not attacked anyone yet.
The BlackMatter website lists targets that the group is not going to attack (in case of accidental infection, the data of the victims will be decrypted for free). The list includes:
- hospitals;
- critical infrastructure facilities (nuclear power plants, power plants, water treatment plants);
- oil and gas industry (pipelines, oil refineries);
- defense industry;
- non-profit organizations;
- government sector.
Recorded Future analysts believe that the new group may be linked to other notorious ransomware, DarkSide, who ceased operations in May this year after the scandalous attack on the Colonial Pipeline company, which drew too close attention of the authorities to the hackers. However, while the researchers do not make final conclusions and continue to investigate.