Hackers are constantly finding new ways to infect your computer with malware and steal your data. With over 1.3 billion devices running Windows worldwide, hackers are more likely to impersonate Microsoft. Unfortunately, Microsoft email scams are more common than you might imagine. Scammers ask you to install the latest updates, confirm your account information, or contact customer support. This article will tell you how to identify fake Microsoft emails and not fall victim to them.
How Microsoft Email Scam happens?
There are different variants of Microsoft email scam. Let’s take a couple of the most common ones as an example. We’re all used to Microsoft, Apple, Google, and other companies notifying users via email when they find potentially unusual activity on their accounts. Unfortunately, scammers have taken advantage of this situation and started sending out fake notifications. Some people can easily fall for this scam. Such an email encourages recipients to secure their Microsoft accounts by logging into them using the link provided (the “Review recent activity” button or “Sign-in added details attached”).
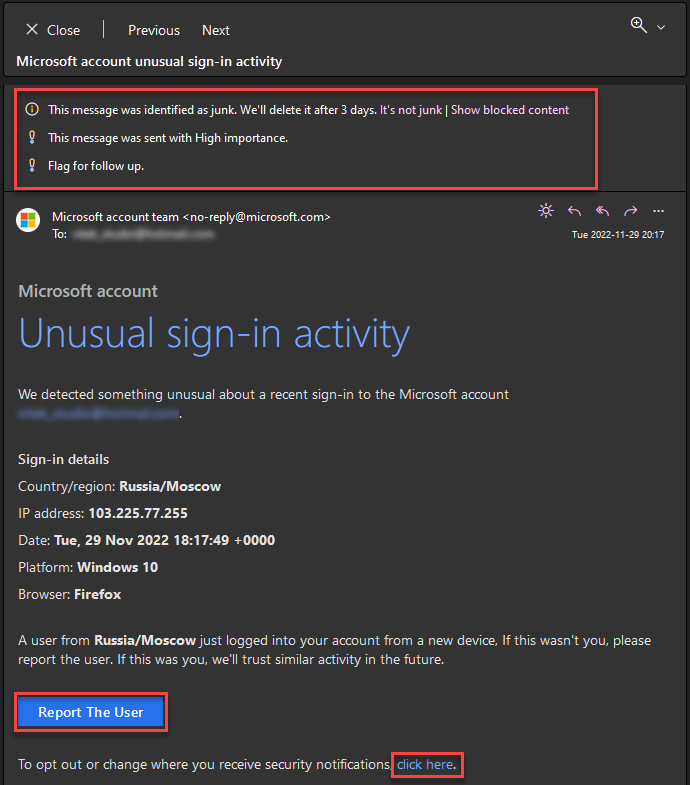
Clicking the link loads a fake Microsoft account login page that looks very similar to the real one. Next, the user is asked to provide their credentials. When the data is entered, it is sent to fraudsters who misuse it, for example, to hijack Microsoft accounts or sell them on the Darknet. In addition, fraudsters can use stolen accounts to spam other people’s contact lists, share various files (including malicious ones), or make purchases. Thus, people can become victims of identity theft, suffer monetary losses, and face privacy issues online. Therefore, you should ignore such emails.
Spam emails are popular among scammers who aim to get the victim to provide sensitive information, such as credentials and credit card details, or transfer money to them. For that, cybercriminals attach malicious files or links to websites designed to download malicious files. These can be ransomware, Trojans, and other malicious programs.
How does a computer get infected?
The email itself, if left untouched, will not harm. The infection only occurs when recipients open (execute) a malicious attachment or open a file downloaded from a link the email contains. In most cases, such emails include a malicious Microsoft Office or PDF document, an executable (.exe) file, a JavaScript file, or an archive file such as ZIP or RAR. Usually, these emails are disguised as critical official messages from legitimate companies.
How Can I Tell If an Email from Microsoft Is Genuine?
Sometimes Microsoft email scams are so well-crafted that it’s hard to tell if the email is genuine or fake. For example, the sender’s name and the content of the email may appear natural, but if you look closely, you see a lot of red flags. Here are essential points to help spot fake Microsoft emails:
The sender’s address
To check the sender’s address, hover your mouse over the “from” field and see if it is legitimate. For example, when you receive an email from Microsoft, ensure that the email address has the domain @microsoft.com and not something suspicious like @m1crosoft.com, @microsfot.com, @account-security-noreply.com, etc. Mismatched email domains indicate that it is a fake email.
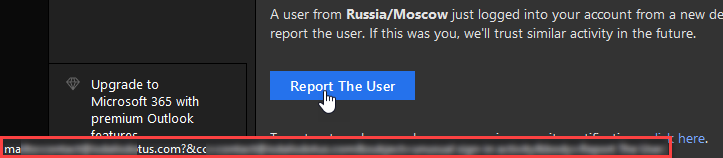
A link leading to a suspicious website
If the email contains a link, don’t rush to click on it. These links often lead to malicious or phishing sites. Instead, make sure it is secure. You can use many tools to ensure the security of a web page, e.g. VirusTotal service. However, the easiest one is to hover over the link and look below to see where it leads.
Urgent calls to action or threats
If the message you receive looks like a threat or tells you that your account will be shut down if you don’t do what you’re told, that’s a serious red flag. For example, cybercriminals often offer to update your version of Outlook, claiming that incoming emails will be stopped unless you install the update within 48 hours. This is probably a scam or phishing Microsoft email attempt. A sense of urgency is a common scam strategy.
Generic messages
If an email doesn’t address you by your first name but uses, for example, “Dear User,” “Dear @youremail.com,” or “Dear Dear Dear Customer”, this should make you suspicious. Usually, companies call you by your first name or nickname you used to register on the website. The absence of this information can signal a Microsoft email scam attempt.
Email attachments
Is this a phishing email from Microsoft? Often legitimate companies will ask you to log into their website and view or download any documents there. However, if you receive an email with an attachment, we do not recommend downloading it, much less opening it. You can, of course, download it and check it with an antivirus application. Unfortunately, infected email attachments are a common practice used by cybercriminals.
Grammatical and spelling mistakes
Beware of emails that contain grammatical and spelling errors. This is a clear sign of Microsoft scams. A company like Microsoft (or any severe organization) would never send an email containing mistakes. Also, Microsoft will never contact users by email to ask for more account information, send out emails about updates, or provide technical support. The company does not initiate communication. Users must initiate any contact with Microsoft. Refrain from trusting emails marked Microsoft that ask you to install the latest application updates. These are most likely phishing attempts. If you’ve noticed these signs, you’ve probably come across Microsoft account email scams.
Examples of Microsoft Email Scam
Failure of delivery emails
If you’ve tried sending an email to a full or non-existent mailbox, you’ve probably received a message that the email has not been delivered. Such an email is conventionally divided into two halves – the first contains details of the error, and the second contains the text of the email itself. For example, cybercriminals send a fake email that includes a “send again” button. When you click on the link, malware is downloaded to your computer.
Re-activation requests
Office 365 phishing attacks are successful because they are based on fear and reflexive reactions. Fake re-activation requests tell recipients that their accounts are deactivated. The user needs to follow an attached malicious link to re-activate their accounts. The link leads to a fake login website, where the victim’s credentials are sent to the cybercriminals.
Alert for hitting storage limits
This Microsoft phishing email is also supposedly sent from Microsoft. If you use a subscription service, you may believe you have reached your account’s storage limit. Fraudsters send fake emails telling you that the user must activate “Quota” to resolve storage problems. This is malware, as in the case of fake delivery error emails. Be careful to avoid stumbling upon signs of Microsoft hacking scams.
How to Report a Suspicious Email to Microsoft?
You can ignore or delete a fraudulent email, but being a decent Internet user, you can help fight this scam. To do so, you need to report a suspicious email to Microsoft. Please select the message, click Report message, and choose Phishing. If you are using the web-based version of Outlook, check the box next to the appropriate email address, select Junk, and then Phishing. Alternatively, you can create a new email and add [email protected] or [email protected] as recipients and drag and drop the spam email into the new message. Also, remember to add the sender’s address to the blocked list.





