The “Microsoft Account Locked” scam is a deceptive tech support fraud. Users receive pop-up messages falsely claiming their Microsoft account is locked due to suspicious or illegal activities, such as money laundering. These pop-ups, not affiliated with Microsoft, urge users to call a provided toll-free number, connecting them to scammers posing as Microsoft technicians. In this post, we will analyze this scam in more detail, and I will also give some recommendations on security and how to avoid falling victim to this scam.
“Microsoft Account Locked” scam Overview
The “Microsoft Account Locked” scam is classified as a tech support scam, a form of phishing and social engineering fraud. It targets users by displaying messages falsely claiming their Microsoft account has been locked. These messages allege detected illegal activities, such as money laundering. Foremost, this scam is not associated with Microsoft and is designed to deceive users. Its intent is to trick victims into contacting scammers, leading to potential financial losses, identity theft, and system infections.
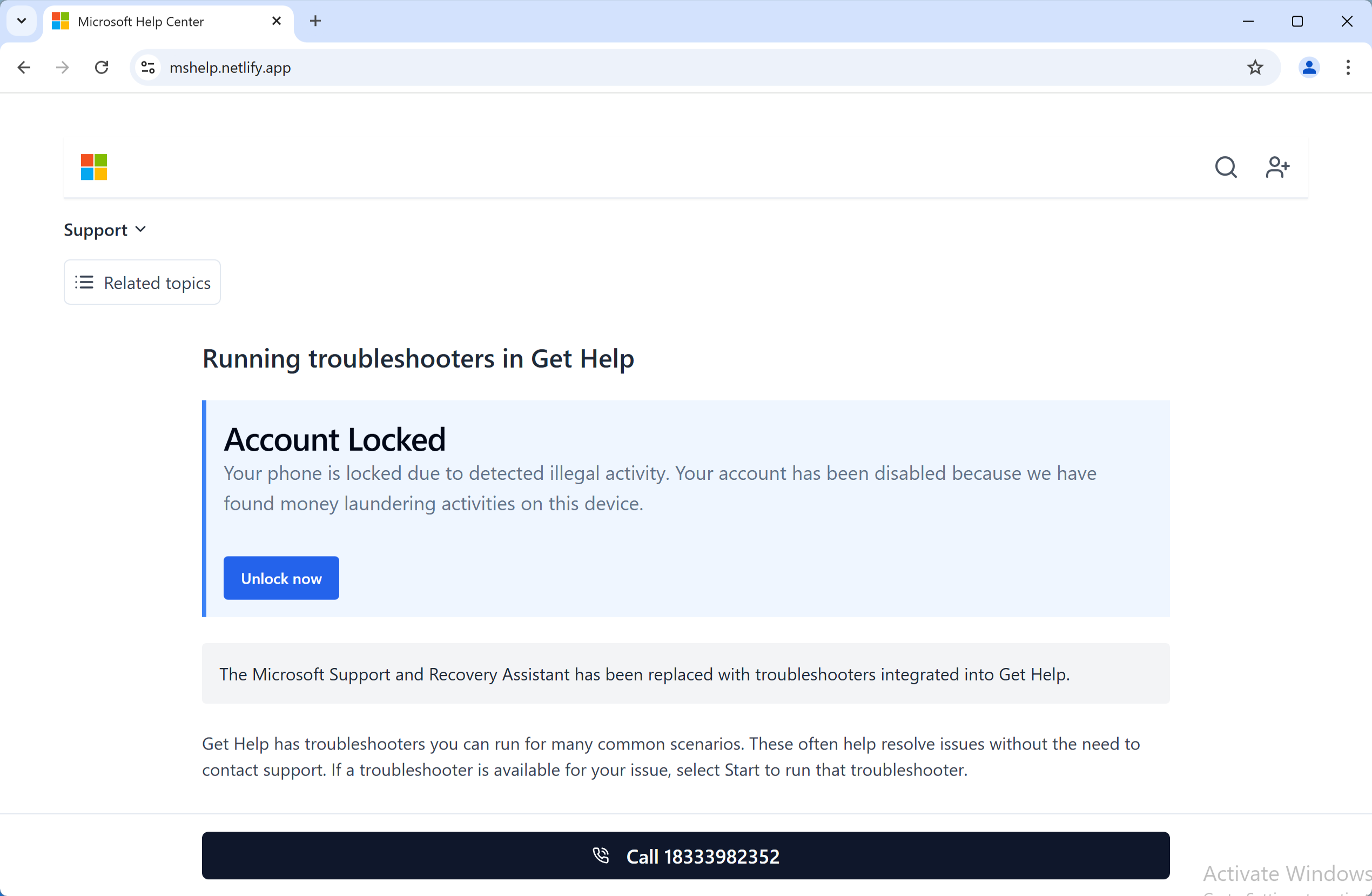
The scam poses a medium damage level, with impacts including loss of sensitive private information, monetary loss, and possible malware infections. The scam’s distribution methods include compromised websites, rogue online pop-up ads, and potentially unwanted applications. Recent data, as of March 2025, indicates its continued relevance, with variations observed in messaging and delivery.
How the Scam Operates
The scam operates through several carefully planned stages that exploit both user trust and technical vulnerabilities. It starts with a pop-up message appearing on the victim’s screen, usually triggered by visiting compromised websites or clicking rogue ads.
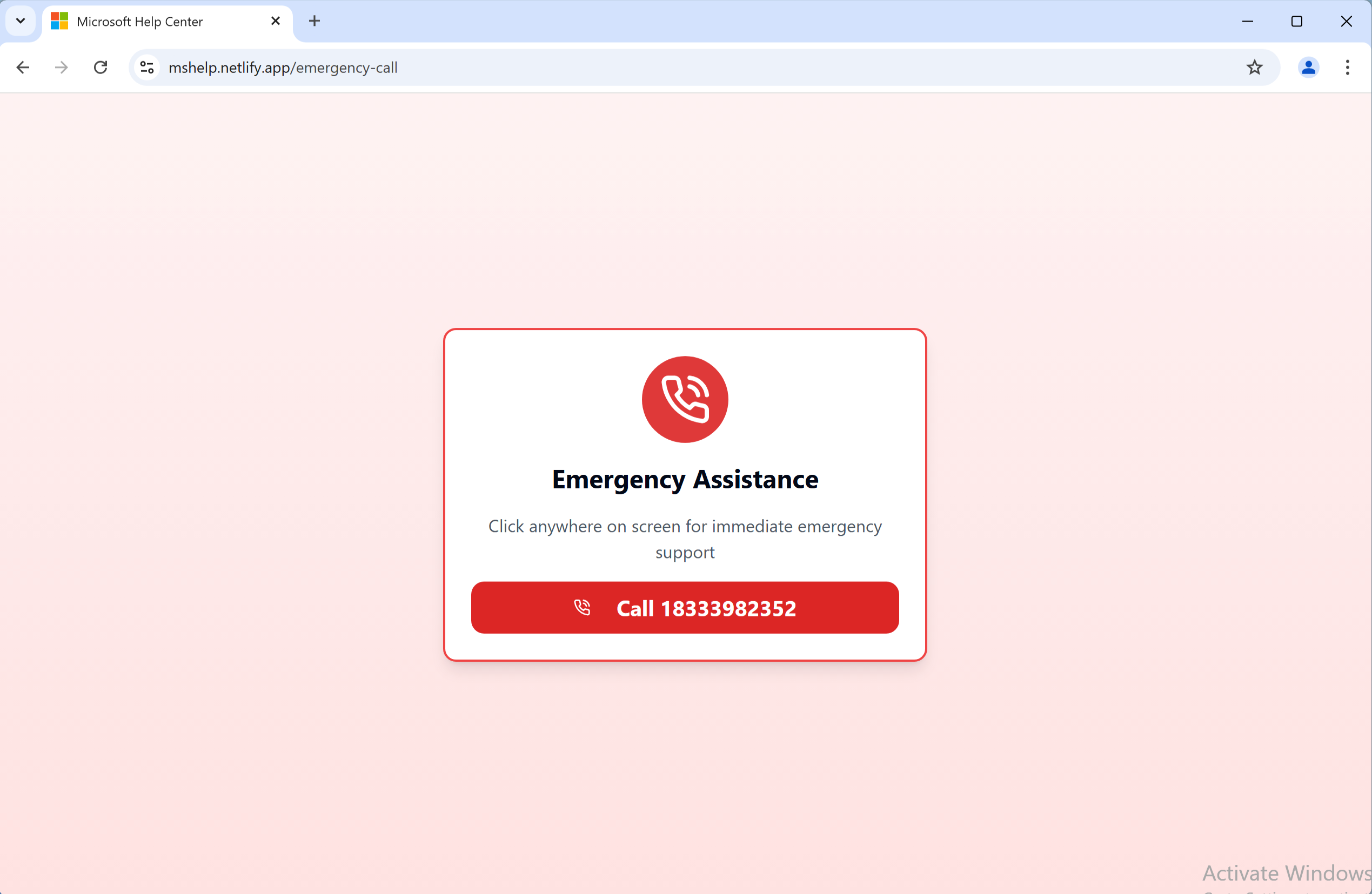
The messagemight claim, “Your Microsoft account has been locked due to detected illegal activity,” and originate from domains like mshelp.netlify[.]app. The associated IP address (34.234.106.80) currently has no detections on VirusTotal. These pop-ups are crafted to resemble legitimate Microsoft alerts, using branding and urgent language to create a sense of panic.
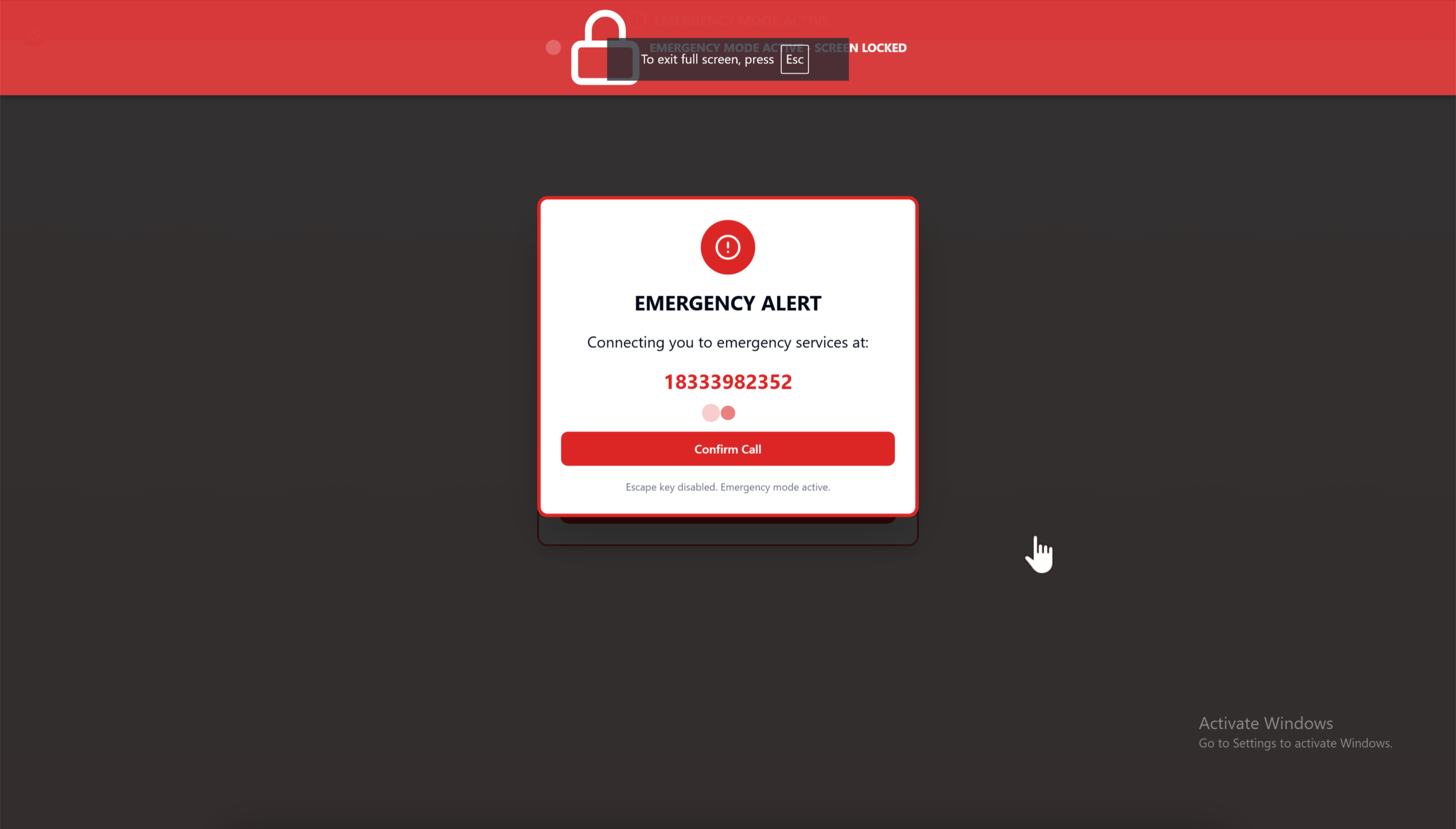
When users attempt to “unlock” their accounts, they are redirected to another pop-up instructing them to call a supposed “Emergency Assistance” number, such as 18333982352. This number is not affiliated with Microsoft and serves as a key indicator of the scam. If the user calls, scammers posing as Microsoft-certified technicians use social engineering tactics to build trust. They claim they need personal details or remote access to “fix” the issue, leveraging fear and urgency to manipulate the victim.
Once granted remote access – often via legitimate tools like TeamViewer or UltraViewer – scammers can engage in a range of malicious activities. They may steal login credentials, personal information, and financial data. They might install malware, including trojans, ransomware, or cryptominers, further compromising the system.
In some cases, they run fake antivirus scans that report non-existent threats, pressuring users into purchasing fraudulent software. Financial exploitation is also common. Scammers demand payments via hard-to-trace methods like gift cards, cash, or cryptocurrency, leading to direct monetary loss.
The scam spreads through multiple channels to maximize its reach. One method involves compromised websites that have been hacked to display malicious pop-ups. Another common tactic is rogue online pop-up ads, which are served through malvertising networks and can appear even on legitimate websites. Additionally, the scam can be delivered via potentially unwanted applications (PUAs), which may install adware that triggers fraudulent pop-ups.
There are multiple variants of this scam, each using slightly different messaging. For example, one version warns, “YOUR COMPUTER HAS BEEN BLOCKED”, and in the same post we explain how this scam works on the technical side.
Red Flags and Detection
First and foremost red flag – these notifications appear in the web browser. Let me make one thing clear – the website technically does not have the ability to scan your device for viruses or system errors. There are exceptions when the official website has a feature to automatically install/update drivers, but this works only if the official utility from the developer is installed on the system. Essentially, in this case, the website is part of the utility’s interface. In all other cases, if a third-party site shows a notification that errors have been detected in the system, it is a guaranteed scam.
So, let’s summarize: Recognizing this scam involves spotting several key red flags. Unsolicited pop-ups claiming account or system issues – especially those appearing without any user action. Another warning sign is the presence of a phone number in the pop-up. Legitimate companies like Microsoft do not display support numbers this way; their official contacts are only available on their official website.
Scammers also use high-pressure tactics, urging victims to call immediately or warning that their account will be permanently locked. Messages often contain grammatical errors or awkward phrasing, a common trait of scam communications. Additionally, scammers frequently request remote access via software like TeamViewer, which, while legitimate, is exploited in these schemes.
How To Stay Safe?
To protect against this scam, users should take several key precautions. Always verify the authenticity of messages or pop-ups by checking Microsoft’s official support page or contacting support through verified channels like their official website or app. Never call phone numbers provided in pop-ups; instead, look up Microsoft’s official contact information independently. You may want to consider using special tools to identify your phone number.
Avoid granting remote access to your computer unless you initiated the request and are certain it’s from a legitimate source, such as Microsoft’s official support. Keeping your operating system and software updated helps protect against vulnerabilities that scammers exploit through compromised websites. Just remember, official tech support NEVER requests remote access to resolve system issues.




