Researchers detected fake company accounts on GitHub linked to a deceitful cybersecurity company. These accounts are promoting harmful repositories on the code hosting service. According to the experts, all repositories claim a proof-of-concept (PoC) exploit for alleged zero-day vulnerabilities in Discord, Google Chrome, and Microsoft Exchange. Though in fact, that was a yet another example of malware in GitHub.
What is GitHub?
GitHub is a massive platform for hosting code. Researchers worldwide use it to share PoC exploits with the information security community. This helps others test patches and determine the scale and impact of bugs. Last year, there were 10 million occurrences of secrets being exposed on GitHub, a 67% increase from the previous year.
Fake Security Company Spreads Malware in GitHub
A team of VulnCheck experts is closely monitoring a large number of GitHub repositories as part of an Exploit Intelligence offering. During a routine check in early May, researchers discovered a malicious repository on GitHub that claimed to be Signal 0-day. Then it was removed. The next day, an almost identical repository was discovered under a different account, this time claiming to be WhatsApp Zero Day. But it, too, was deleted by the GitHub team. This process continued for a month.
After that, the attackers created a whole network of accounts, including half a dozen GitHub accounts and several related Twitter accounts. These accounts pretend to be part of a defunct security company called High Sierra Cyber Security. Here is an example of one such account:
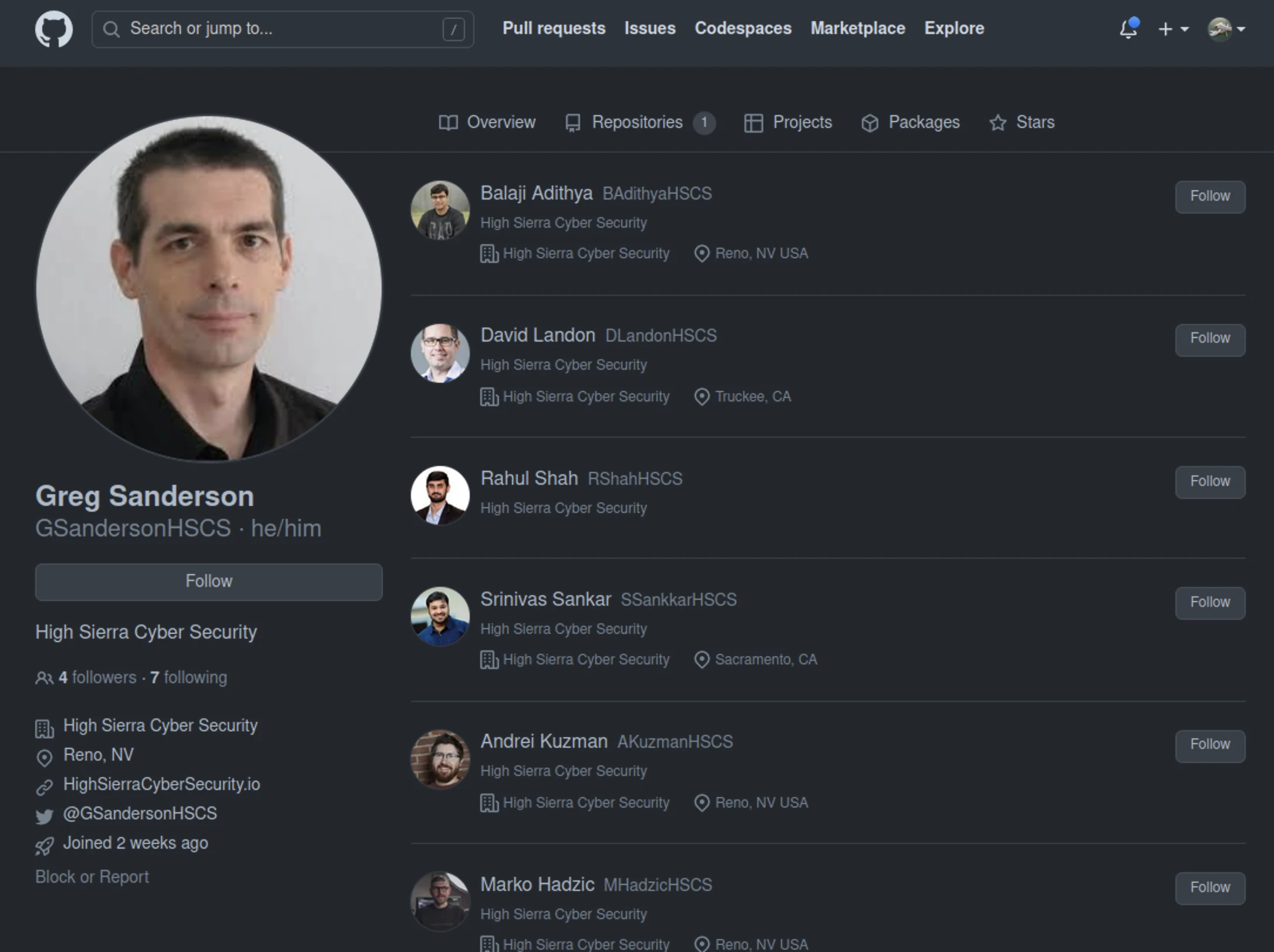
According to technical engineers, threat actors now use code repositories to trick unaware developers into doing their work for them. These actors have focused on social engineering tactics to make the repository owner appear legitimate, but their malware on Github is quite easy to identify. Since there’s plenty of room for improvement, these attacks may become much more effective.
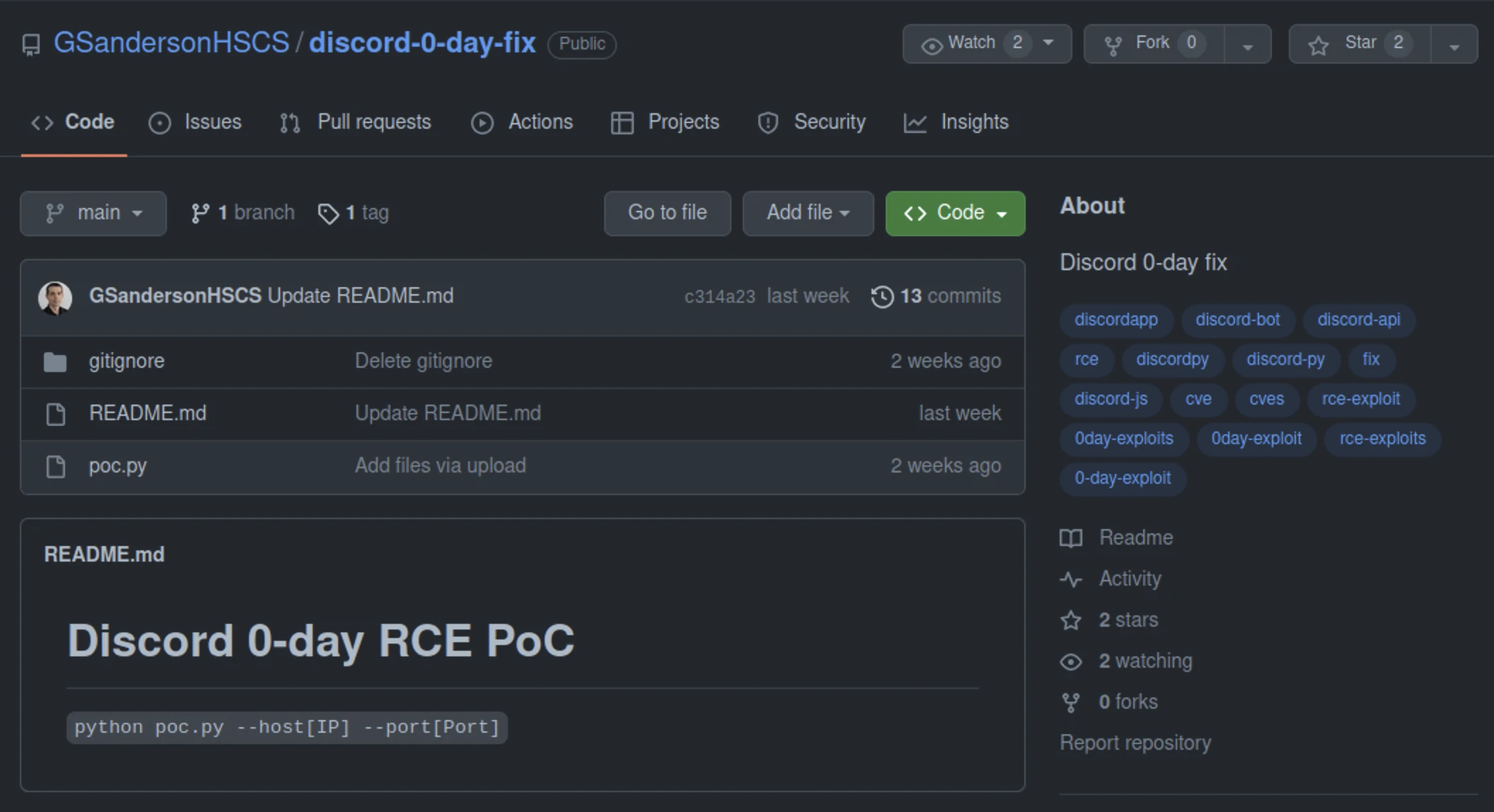
All the repositories have a straightforward structure depicted in the image below. Additionally, they use the “hot” CVE tagging to entice potential victims.
How it works?
The code in poc.py downloads a harmful binary and runs it. The Python script will download a particular payload based on the target’s operating system. This Discord “0-day” exploit utilizes the code mentioned above to carry out these tasks.
Afterward, poc.py obtains one of two zip files from GitHub: cveslinux.zip or cveswindows.zip. The program unzips the file, saves it to the computer’s disk, and then runs it. However, the Windows binary has a high detection rate on VirusTotal (43/71). In contrast, the Linux binary has a lower detection rate (3/62) but does contain some strings that suggest its purpose.
Conclusions:
An attacker has put much effort into creating fake identities to spread obvious malware in GitHub. They may have been successful, but since they continue to use this method, they must think it will work. It needs to be clarified if this is an individual with too much free time or a more advanced campaign like the one discovered by Google TAG in January 2021.
Regardless, security researchers should be aware that they are attractive targets for cybercriminals and should exercise caution when downloading code from GitHub. Constantly scrutinize the code you’re about to execute and avoid using anything you don’t understand. Use virtual or dedicated machines on which you do not risk losing your data. There, precautions are never excessive, especially considering the severity of malware on GitHub.