On May 7, 2024, UK National Crime Agency published the detailed dossier on the LockBit ransomware group’s leader. Dmitry Khoroshev, known as LockBitSupp, leads one of the most vicious ransomware groups since its inception in 2020. After unmasking, law enforcement initiated sanctioning the hacker in numerous countries around the world.
NCA Unveils LockBitSupp Identity
Several days ago, on May 5, 2024, a changed LockBit site variant, that appeared after the law enforcement hack in February of the same year, got back online. Earlier, it used to contain the hefty list of information that law enforcement agencies managed to leak from the network of the threat actor. This time, however, they went further: instead of court judgments, they promised to publish personal information of the LockBit gang leader.
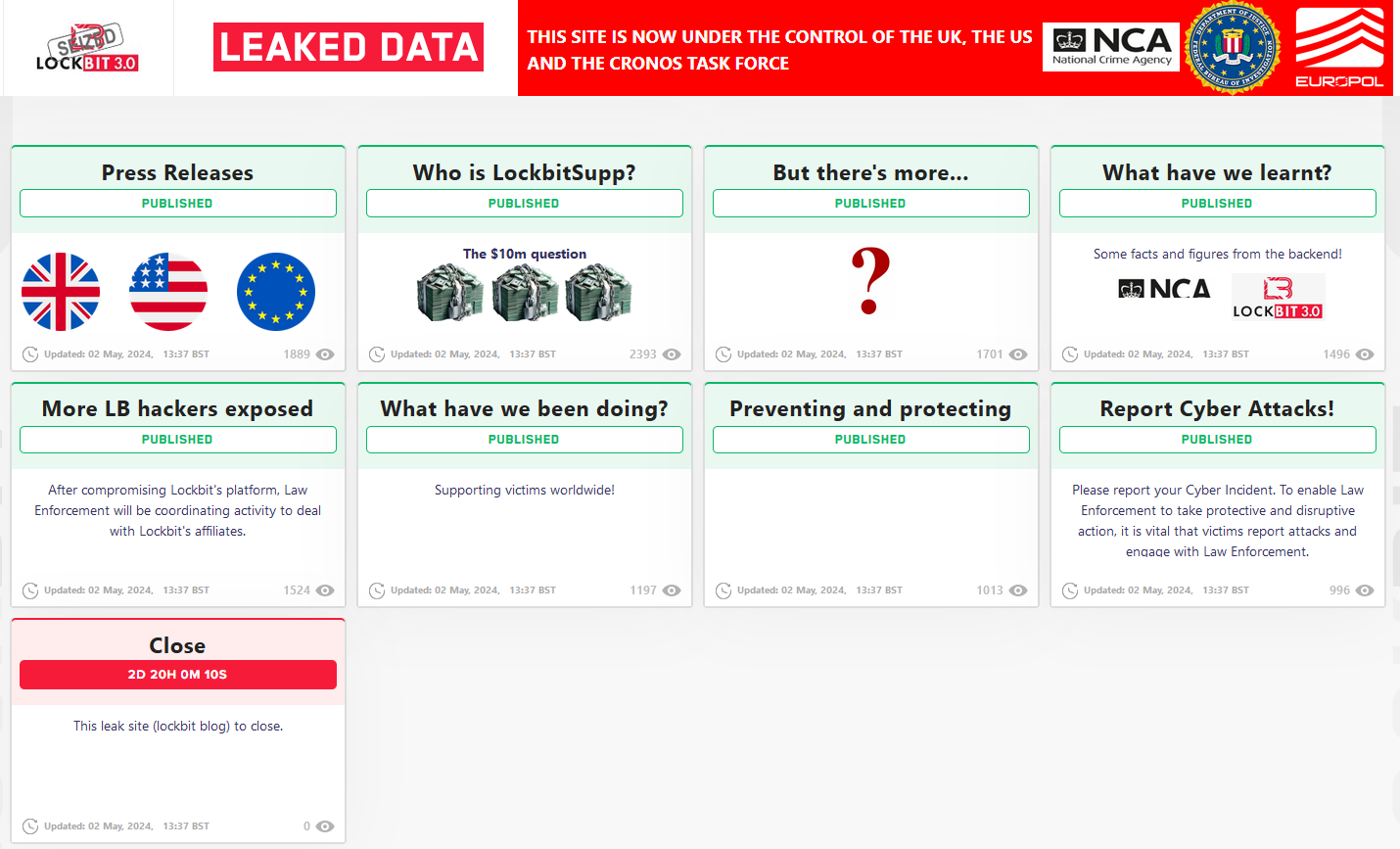
Man under the nickname LockBitSupp always attracted a lot of attention: both due to the success of his ransomware group and unusual publicity of a ransomware group leader that was never seen before. What’s more tempting is the promise to pay $10 million to a person who’d reveal his identity. He was outstandingly confident about his anonymity, and for a good reason, so the huge reward was left unclaimed ever since this “contest” was first announced.
Though now, by the looks of it, Dmitry Yurievich Khoroshev owes $10 million to NCA specialists. During the first summary of Operation Cronos, NCA already threatened to publish his identity, but that was probably a mere bluff. But not this time – the full list of the guy’s personal information was both published and turned into courts in order to imply personal sanctions. They in particular suppose arrest of the personal assets and implying travel bans.
LockBit Leader Compromised: Will This Stop the Gang?
Despite the overall excitement around the identity reveal of LockBitSupp, it won’t make that much difference to the gang. Just another stain on the reputation, that has got the first, and much stronger blow back in February. Deanonymizing of the gang’s leader places it in the row with Evil Corp, whose chief Maksim Yakubets is a long-term guest of the FBI’s wanted board.
A more important news of the fresh release is an updated pack of data about the affiliates and operations of the ransomware group. NCA, together with law enforcement agencies, leaked attack statistics, affiliate counters and names, and the geography of attacks.
As far as the fresh leak says, after the February attack, 2/3 of the LockBit affiliates escaped the business. This was somewhat noticeable by the decline in the group’s activity, but not to that extent. Still, the quality of these attacks noticeably decreased: no loud names in the last two months. At the same time, the number of attacks on the UK companies plummeted to a similar extent (-73%) – definite reaction to the NCA’s effort.







Myself and company were victims of lockbit on Dec 5, 2020 in North Carolina.
where can I get a decrypt key? I would like to recover my locked files i kept. I was able to recover from this disasterous intrusion without paying a ransom. Would you like to hear my story? please get in touch.