For about four years, the Italian company CloudEyE was engaged in a seemingly legal business, offering protection of binaries from reverse engineering for Windows applications, however, at the same time, CloudEyE secretly advertised its services on the black market and collaborated with ransomware operators.
Check Point experts discovered this when they began to investigate the activities of the GuLoader malware, activity of which has significantly increased since 2020.
Researchers claim to have found in GuLoader code references to CloudEyE Protector, a security solution created by CloudEyE.
“And if usually such products for protecting source code are completely legal and widely used by developers of majority of commercial applications, then in this case, researchers are confident that CloudEyE and its owners have been active in hacker forums for many years”, – said Check Point experts.
The fact is that Check Point analysts were able to link the CloudEyE security product, promoted on the securitycode.eu website, with the advertising of a crypto service for the malware, DarkEyE, which was widely advertised on hacker forums back in 2014. Moreover, experts also linked the three users and three email addresses seen in the DarkEyE promotion to the real identity of one of the founders of CloudEyE.
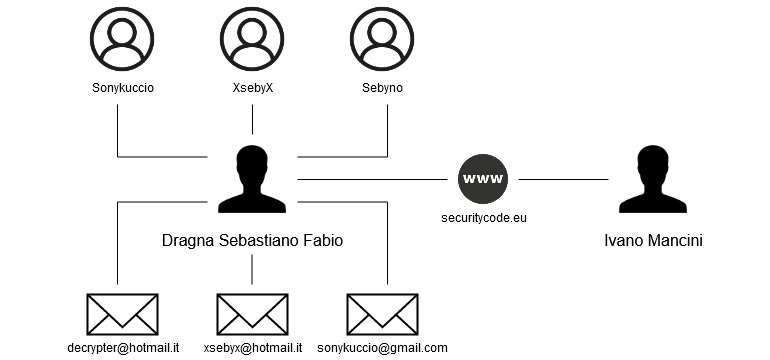
Researchers write that these email addresses and usernames appear in a number of posts on hacker forums. These publications advertise binary and encryption services, with messages referring back to DarkEyE.
Based on this, experts conclude that the person hiding under these pseudonyms for a long time was tightly connected with the community of cybercriminals. Experts believe that old ties helped the company to start a legitimate business. So, on the official website, CloudEyE developers boast that the company has more than 5,000 customers.
“Based on the minimum rate of $100 per month, in total, the company earned at least $500,000. However, the amount can be much larger if you take into account that the cost of some monthly subscriptions can reach up to $ 750, and many customers have obviously used this service for several months”, – calculated Check Point experts.
Researchers say that all the “evidence” indicates that CloudEyE operators tried to legitimize their criminal activity by hiding it behind a shell company in order to justify profits and avoid unnecessary attention from local tax authorities when cashing out considerable sums.
“CloudEyE operations may look legitimate, but the service that provides CloudEyE has been a common denominator in thousands of attacks over the past year”, — says the Check Point report.
Although experts claim that DarkEyE and CloudEyE have been quite extensively used in recent years, it seems that only one malicious campaign seems to be the main client of developers, and this is mentioned above the GuLoader ransomware.
I also remind you that recently, on hacker forums and on the black market, surged in price credentials of popular YouTube channels.
In his report, Check Point talks about connections between CloudEyE and GuLoader.
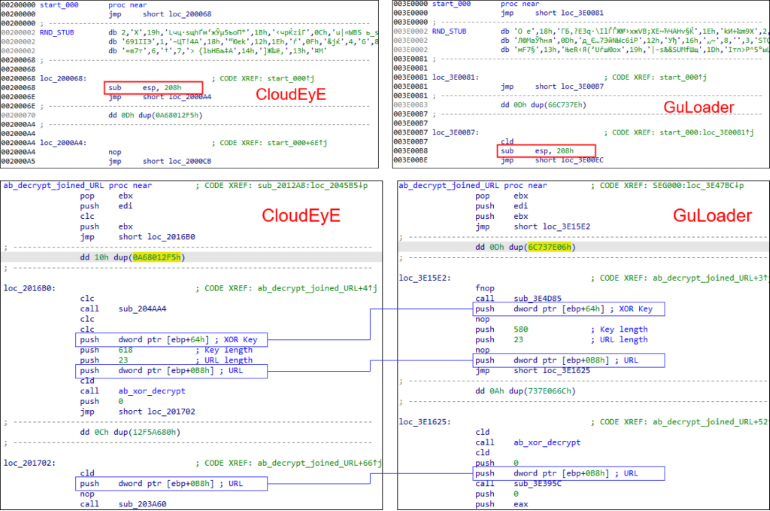
Firstly, the most obvious of them is the fact that the code of applications that passed through CloudEyE Protect contains patterns that are very similar to discovered by experts GuLoader samples.
Finally was reached the point, when CloudEyE Protect will detected any random application as GuLoader malware, although in fact it may be harmless and legitimate application.
Secondly, Check Point analysts noticed that the CloudEyE interface contained a URL stub, which was often found in GuLoader samples.
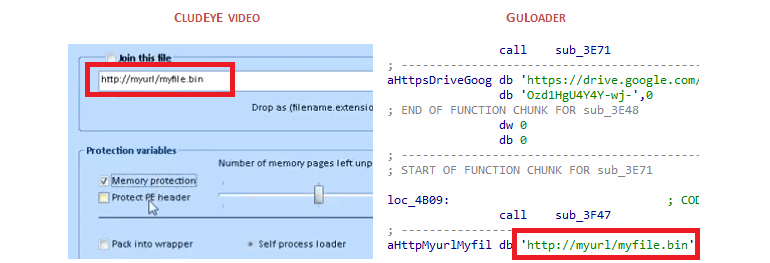
Thirdly, many of the CloudEyE features seem to have been specifically designed for GuLoader operations.
“The tutorials published on CloudEyE demonstrate how to store payloads in the cloud, including Google Drive and OneDrive. Cloud storages usually perform antivirus scans and technically do not allow downloading of malicious programs. However, payload encryption implemented in CloudEyE helps bypass this limitation”, — say the experts.
Researchers say that such functionality does not make sense for a regular application, but for malware, the ability to avoid cloud scans can be very useful. This can be especially true for GuLoader, which is a “network bootloader” that infects the victim’s computer and then downloads the second-level payload from Google Drive or Microsoft OneDrive.
After the publication of the Check Point report, CloudEyE representatives made an official statement and refuted all the conclusions of the experts. The company claims that criminals without the notification of the developers.

At the same time, the company’s work was stopped for an uncertain period.