Data breach of a known US retailer Hot Topic leaks a selection of personally identifiable information of 350 million chain’s customers. Such a worrying conclusion comes from the database posted for sale on one of the Darknet forums. The breach likely touches not only the company itself, but also its subsidiaries – Box Lunch and Torrid. Analysts already define this data leak as one of the biggest ones that come from a corporation.
Hot Topic Hacked, 350 Million Customers Data Exposed
In the breach published on October 21, 2024 on BreachForum by a threat actor nicknamed Satanic, personal information of 350 million customers and employees is offered for sale, at a price of just $20,000. For Hot Topic themselves, however, the price tag is 5x of that – $100,000 for deleting the forum thread completely. Hacker does not disclose the way they’ve breached into the company, but shares quite extensive examples that allow us to judge on the scale and potential impact. Spoiler – it is tremendous.

Contrary to how it usually happens with Darknet leaks, Hot Topic breach features not just username, email and similar basic information. Leak samples offered by the hacker show complete addresses, emails, phone numbers and extensive payment information (including holder info and card details). This list goes on with account IDs and in-chain loyalty points tied to corresponding accounts. The latter may be quite handy if hackers (or someone who’d purchased the leaked DB) will try taking over the accounts.
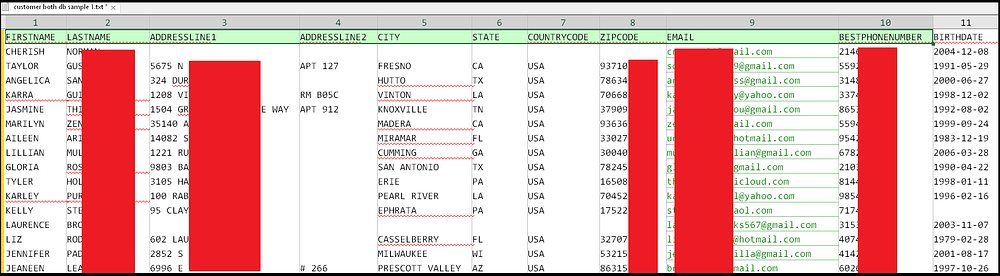
Aside from customers’ information, the data breach also contains data of employees of Hot Topic, and Torrid with BoxLunch – subdivisions of the company. This part of the breach generally touches email addresses and full names – not too much to brag about. Still, this exact part of the breach was the key for analysts to investigate the origins of the breach.
How Hot Topic Was Hacked?
Despite Satanic being (as expected) quite secretive on detailed information on how they’ve done the breach, Hudson Rock Infostealers’ analysts managed to do a pretty good job of analyzing the clues present in logs. They also communicated with the hacker on certain details, confirming their suspicions (though not trusting the hacker’s words entirely).
So, as far as analysis goes, the point of initial access was the PC of an outsource agent who’s working for big data analysis company Robling. The latter is doing data analysis for Hot Topic and its subsidiaries, eventually requiring access to the company’s cloud storages. By infecting this system with an undisclosed infostealer malware, the hacker managed to extract about 240 credentials stored in the system. Among them was login data from Hot Topic and Torrid Snowflake environments.
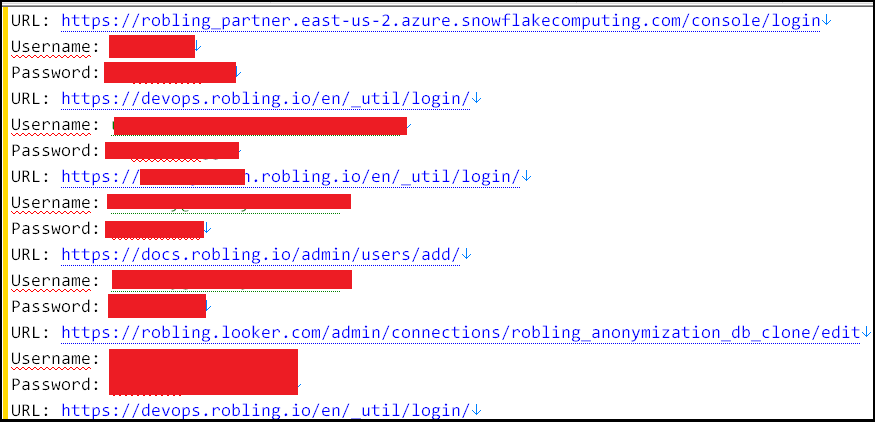
And that is it – from now on, Satanic got access to all the internal data of the company. It apparently took some time to browse and extract all the data, but that is it – no super-fancy movie-like hacking, just an infostealer that did all the dirty job.
What should I do?
If you are a customer of one of these three companies, I’d advise you to migrate your shop accounts to a different email address. This way, you will get the loyalty points secured from someone spending them for you. With card data and other sensitive information, however, things are much more complicated.
You are unlikely to change or remove this information from the company, especially considering it was already stolen. With this information, hackers can create invoices directed to your payment card, and then get the confirmation codes through various phishing ways. If that is the case, I’d recommend you to set a low daily payment limit, and thoroughly track the codes and requests that come to your phone or email. Report all the suspicious cases to your bank security, shall they appear, and never follow any instructions that ask you to type the confirmation code, if you are not the one who called for it.