Hkbsse.exe is a name of a process related to Amadey Dropper, that you can observe while browsing through the system. This malware delivers other malware to the target system, disables security solutions and does a lot of other dirty things that harm the system pretty badly. In this article, I will explain how to remove this malware and prevent its appearance in future.
Hkbsse.exe Overview
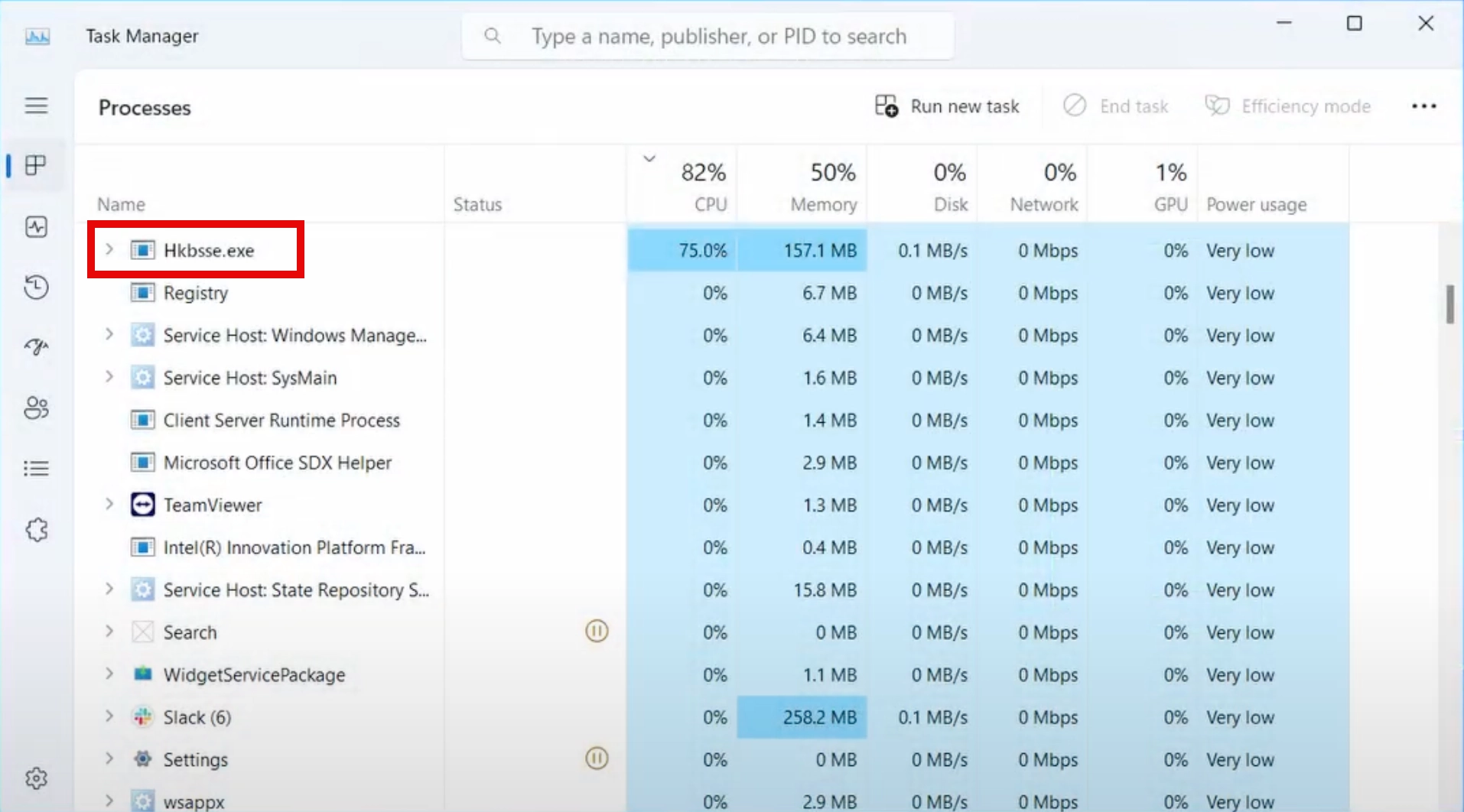
Hkbsse.exe is a malicious process that users can notice in Task Manager. This process has no window, which is typical and hints that malware, namely Amadey Dropper, is present on the system. Its main task is to stealthily deliver payloads in the form of other threats to the computer. I.e., it can deliver any malware, such as spyware or ransomware, to the target system. Due to the fact that Hkbsse.exe runs in the background and has a name similar to a system process, users may not immediately notice its presence.
The main method of spreading this malware is spear phishing. That is, the attacker likely has some knowledge about the victim. However, this malware is also spread through hacked programs, games, and generally anything that can be downloaded from torrents or pirate sites. The most common carriers of this malware are cracks, activators, and other software cracking tools. Once on the system, the threat tries to disable built-in defenses and gain the highest privileges on the system. This allows downloaded viruses to run without any restrictions.
Technical Analysis
Let’s take a closer look at what the Hkbsse.exe process is actually doing on the system. Even though it has no visible windows or any signs of activity, the most important actions happen behind the scenes. As I mentioned earlier, if you see the Hkbsse.exe process, then your system is infected with Amadey Dropper malware (sample on VirusTotal). Let’s break down the entire lifecycle of this malware.
Step 1. Initial Access
Throughout the lifecycle, the threat abuses the legitimate Windows Error Reporting Service to avoid triggering anti-malware. Once on the system, the first thing it does is check if there are other instances of this malware running on the system. To do this, it checks for the following mutexes:
Global\SyncRootManager
Local\__DDrawCheckExclMode__
CicLoadWinStaWinSta0
Local\WininetConnectionMutex
Local\WininetProxyRegistryMutex
Local\WininetStartupMutex
Local\_!MSFTHISTORY!_
Local\c:!users!admin!appdata!local!microsoft!windows!history!history.ie5!
If any mutexes are found, the malware terminates further execution. If no mutexes are detected, the malware creates them. As I said above, this is a standard malware practice that prevents multiple copies from running on the same system.
Local\SessionImmersiveColorMutex
Local\ZoneAttributeCacheCounterMutex
Local\ZonesCacheCounterMutex
Local\WininetConnectionMutex
Local\WininetProxyRegistryMutex
Local\WininetStartupMutex
The next step is to check for anti-malware programs and whether the system is virtualized. Depending on the results, the behavior of the malware may vary, but it is not always about stopping the execution completely. Most likely, when seeing an enterprise VM, the virus will move on . Specifically, the threat checks the following values:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion
HKEY_LOCAL_MACHINE\Software\Microsoft\LanguageOverlay\OverlayPackages\en-US
HKEY_LOCAL_MACHINE\HARDWARE\DESCRIPTION\System\CentralProcessor\0
HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap
As you can see, some keys determine the geographical location of the system and its language. Since Amadey Dropper has Russian roots, it has a hard-coded rule not to attack computers located in Russia. In addition, this data is needed to create a fingerprint of the system.
Step 2. Persistence
Next, the malware tries to gain persistence on the system. After performing all the checks, making sure that the threat is not running on a virtual system, it adds a copy of itself to sections responsible for autorun. The malware adds itself to the following partitions:
C:\Windows\System32\Tasks\Hkbsse
C:\Windows\System32\Tasks\Microsoft\Windows\SoftwareProtectionPlatform\SvcRestartTask
C:\Windows\System32\Tasks\Microsoft\Windows\SoftwareProtectionPlatform\SvcRestartTaskLogon
C:\Windows\System32\Tasks\Microsoft\Windows\SoftwareProtectionPlatform\SvcRestartTaskNetwork
C:\Windows\Tasks\Hkbsse.job
This allows the threat to run with the system even if the process has been forcefully terminated. This includes both user interrupting the execution and any of the actions from security programs.
Step 3. C2 Connection and Payload
After all the preparations are done, the malware accomplishes its main task: deliver the payload to the system. But before it does that, the malware contacts the C2 server, sends the system’s fingerprint and waits for further commands. It sends the following requests:
POST http://185.215.113.26/Dem7kTu/index.php 200
POST http[:]//epohe.ru/tmp/
POST http[:]//sevtvd17ht.top/v1/upload.php 200
Next, the malware gets a response from C2 containing instructions and the actual payload server address, which is as follows:
GET http://185.215.113.26/JLumma.exe 200
GET http://185.215.113.26/JUmer.exe 200
GET http://iakovosioannidis.com/parts/setup2.exe 200
This is how Amadey Dropper delivers the payload to the system. Next, the malware decompresses the payload, resulting in the Hkbsse.exe process that we talked about at the beginning. Among the files delivered by this specific sample, there is Lumma Stealer – a rather notorious virus in recent times.
How To Remove Hkbsse.exe?
If you have found Hkbsse.exe running in your Task Manager, it likely means that Microsoft Defender missed it for some reason. This may be because that you manually added the threat to the exceptions, or the threat may have disabled Defender. Anyway, you will now need a third-party anti-malware solution to neutralize the threat. I recommend GridinSoft Anti-Malware as it can effectively remove threats and does not conflict with Microsoft’s built-in solution. Follow these instructions to clean your PC from threats.

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.