Hackers majorly use the Microsoft and DHL brands in phishing attacks. In Q4 2020, cybercriminals used more brands from the tech industry, followed by shipping and retail businesses.
Information security researchers from the Check Point Software team said that phishers love the Microsoft brand. 43% of all attempts at phishing attacks were associated with it – attackers tried to influence people working remotely during the second wave of the pandemic.
Top brands most frequently used in phishing attacks:
- Microsoft (43% of all phishing attacks attempts with the use of brand names worldwide)
- DHL (18%)
- LinkedIn (6%)
- Amazon (5%)
- Rakuten (4%)
- IKEA (3%)
- Google (2%)
- Paypal (2%)
- Chase (2%)
- Yahoo (1%)
How a brand-based phishing attack works
In a phishing attack that is using brands, criminals try to imitate the official website of a well-known company using a domain name, URL and design similar to the original website.
Victims can receive a link to the fake page via email or SMS. They can also be redirected to a phishing site while browsing the web or from a malicious mobile application. Fake sites often contain a form designed to steal credentials, billing information or other personal information.
Examples of phishing attacks using brands:
A phishing email allegedly from DHL – an example of password theft
In November, Check Point researchers noticed a malicious phishing email that used the DHL trademark. Then the attackers tried to steal user passwords. The email that came from a fake email address [email protected] contained the following text:
“RE: Your DHL Parcel (available to receive) – [
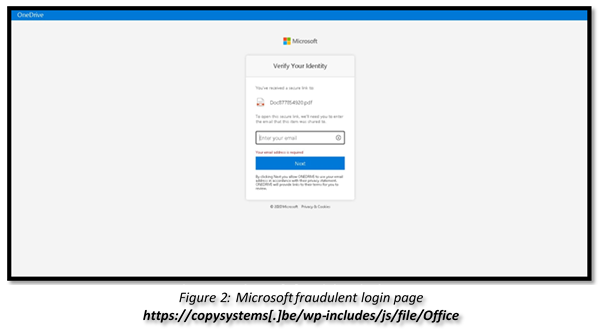
Phishing email allegedly from Microsoft – an example of credential theft.
In December, Check Point researchers discovered a malicious phishing email that attempted to steal user credentials from a Microsoft Office 365 account. In the subject of the email was indicated: “Daily Document Delivery # –
Let me remind you that I talked about cybercriminals that started using Google services more often in phishing campaigns.