“Hacker Who Has Access To Your Operating System” is a type of email scam that targets unsuspecting internet users. This scam can take various forms, but the core idea remains the same – to pressure the victim into paying money.
“Hacker Who Has Access To Your Operating System” Overview
The “Hacker Who Has Access” scam is a type of email spam that targets impressionable users. The idea is as follows: the scammer presents himself as a hacker and claims to have hacked the victim and asks the victim to pay money for non-disclosure of sensitive information. To make the scam more convincing, the attacker uses deceptive social engineering techniques. This specific campaign is somewhat similar to other email scams of this direction, namely “Professional Hacker” or “Have you heard of Pegasus?”. This one, however, has a different text, though the motivation and threats are almost the same.
All the threats revolve around the claim that the victim’s computer was allegedly hacked, the attacker gained full access to it and caught the victim watching 18+ content. Additionally, the scammer claims to have a webcam recording of the moment when the victim watched adult content. And even if the victim has a computer without a webcam, the “hacker” convincingly claims that he has the video. To confirm the authenticity of his words, the attacker absurdly uses technical jargon incomprehensible to the average user, such as “successfully managed to hack your operating system” or “the malware it uses integrates at driver level” and the like. In reality, this is simply a lie meant to intimidate the victim.
How Does This Scam Work?
So, let’s dissect the “Hacker Who Has Access” email and understand why it’s not true. While it’s theoretically possible, there are too many red flags that expose this scam. The entire email relies on social engineering techniques. Let’s analyze the beginning of the text.
Worrying Claims At The Very Beginning
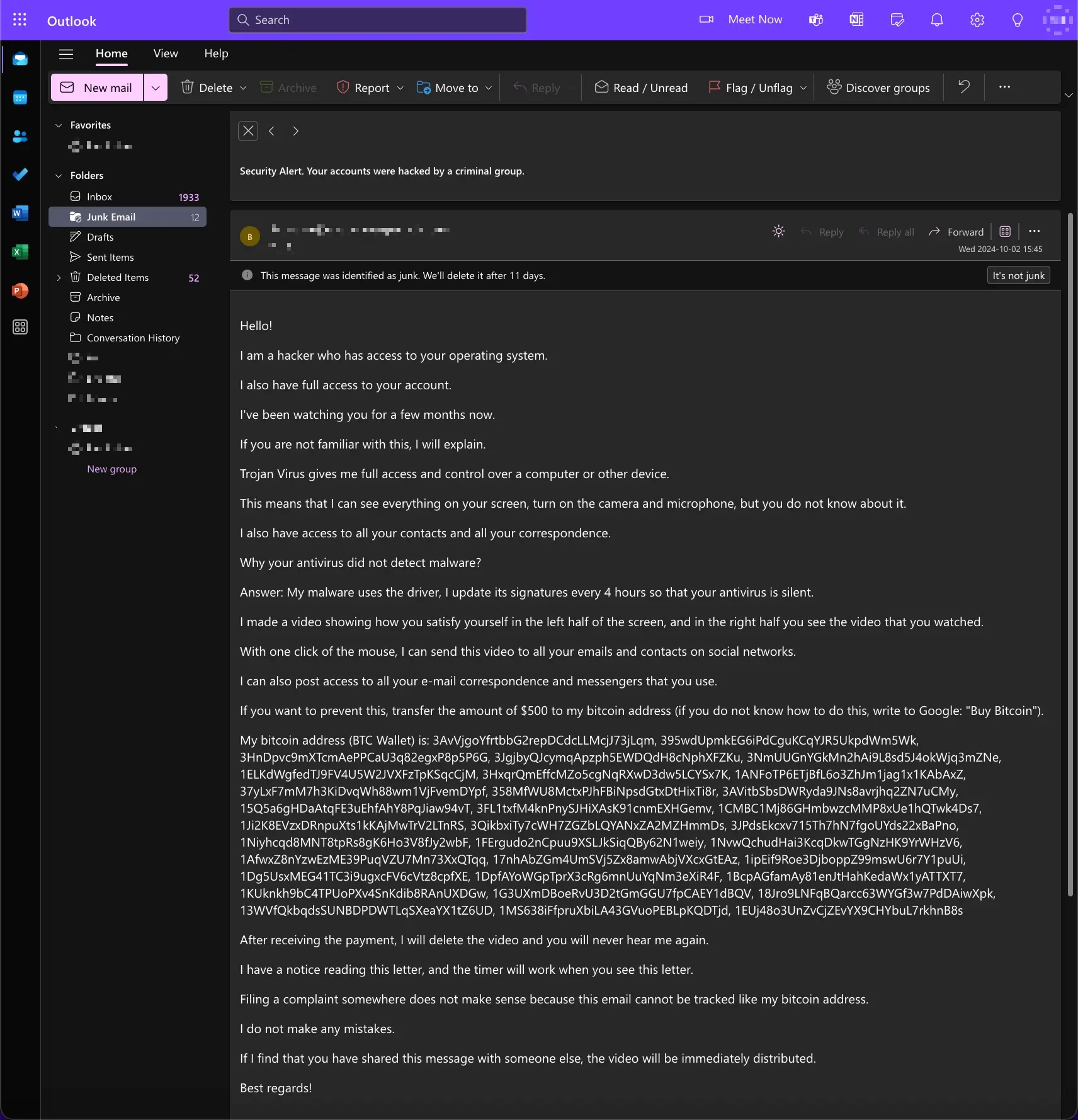
Subject: Security Alert. Your accounts were hacked by a criminal group.
Hello!
I am a hacker who has access to your operating system.
I also have full access to your account.
I’ve been watching you for a few months now.
The first thing to notice is the inconsistency of information. The subject line claims that a criminal group hacked the victim’s accounts. But further, the author goes on to say that he is acting on behalf of one person. Although it is a small thing, this is what helps with identifying the “Hacker Who Has Access” email as fraudulent. But let’s set that aside for now and move on.
Fake Hacker Activities Description
The fact is that you were infected with malware through an adult site that you visited.
If you are not familiar with this, I will explain.
Trojan Virus gives me full access and control over a computer or other device.
This means that I can see everything on your screen, turn on the camera and microphone, but you do not know about it.
I also have access to all your contacts and all your correspondence.
Why your antivirus did not detect malware?
Answer: My malware uses the driver, I update its signatures every 4 hours so that your antivirus is silent.
And now for the best part – infection through adult sites, which was once a popular tactic for attackers. Though, this was so long ago only a few people remember porn viruses as a real threat. Although modern adult sites have their dangers, they are not about malware injection. And sure enough, there are different tricks on making the user download and run the malware. But most of such attacks are large-scale, and the attackers do not email individual victims that they have been hacked. On the contrary, they collect stolen data and sell it on the Darknet, and any notifications will even disrupt the possibility of using hacked accounts.
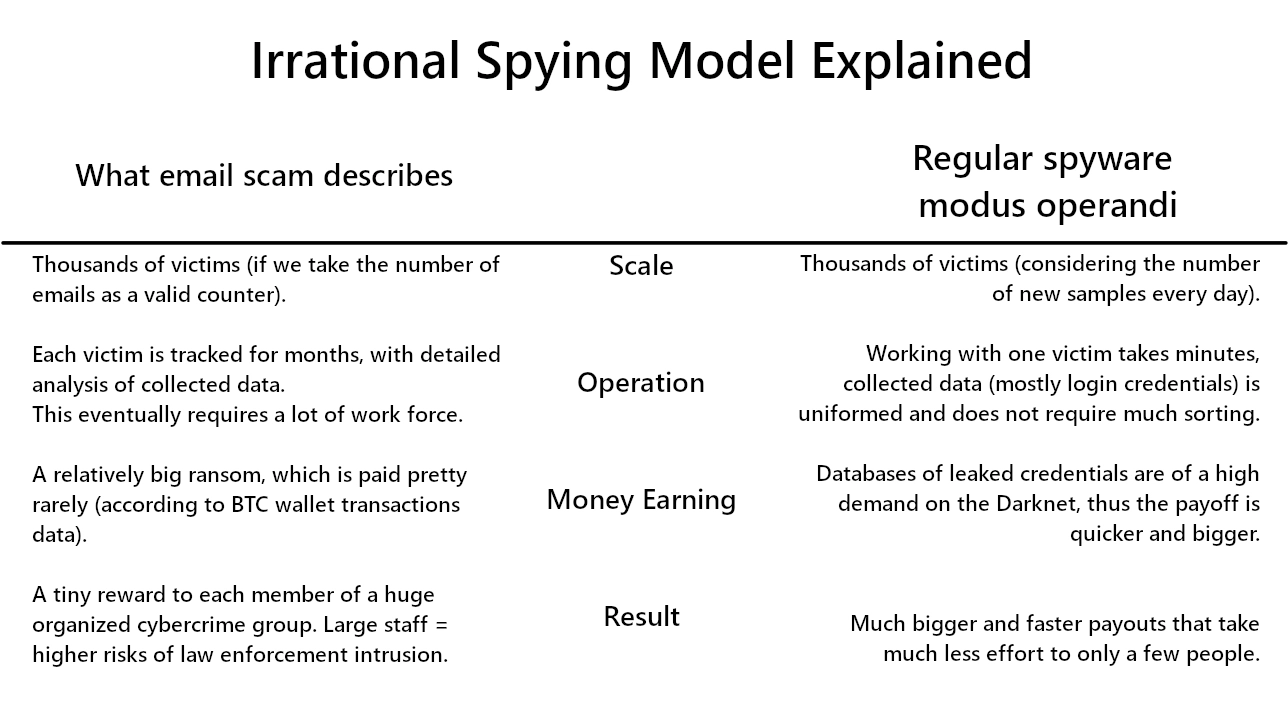
Next, the most ridiculous part of the “Hacker Who Has Access” email is the description of how the “malware” bypasses the protection. While some viruses really install themselves on the driver level, this trick still requires a user action to install it. Meaning, the user must run the file with administrator privileges, which is not the case according to the letter text. Overall, the description of how the malware operates is fundamentally inconsistent with how such malware actually works.
Claims On Compromised Video Being Recorded
I made a video showing how you satisfy yourself in the left half of the screen, and in the right half you see the video that you watched.
With one click of the mouse, I can send this video to all your emails and contacts on social networks.
I can also post access to all your e-mail correspondence and messengers that you use.
If you want to prevent this,
transfer the amount of $500 to my bitcoin address (if you do not know how to do this, write to Google: “Buy Bitcoin”).
The culmination of the scam starts with claims about possessing a video that captures the victim watching 18+ content. Clearly, this is meant to further convince the unsuspecting victim of the scam’s authenticity. While this claim is actually difficult to prove or disprove, given all the red flags in the letter, there is ample reason to believe the sender is lying. As I mentioned earlier, some devices are equipped with a special physical lens blocking. This shutter physically covers the camera which cannot be opened by software.
In addition, some devices lack a camera entirely, which further undermines such claims. For the devices that do have a camera, most modern laptops and webcams feature an indicator light directly wired to the camera’s power circuitry. This ensures that whenever the camera is in use (whether by the user or by malware), the indicator light will turn on. This security feature cannot be bypassed, at least without physical access to the device or some specific wiring used inside the camera.
Ransom Demands & Publishing Threats
After receiving the payment, I will delete the video and you will never hear me again.
I give you 50 hours (more than 2 days) to pay.
I have a notice reading this letter, and the timer will work when you see this letter.
Filing a complaint somewhere does not make sense because this email cannot be tracked like my bitcoin address.
I do not make any mistakes.
If I find that you have shared this message with someone else, the video will be immediately distributed.
Best regards!
At the end, the scammer demands payment within 50 hours (the value may vary from one email to another) and promises to disappear from your life if you pay. While it is theoretically possible to track the moment of email being read and count 50 hours from that point in time, the probability of this working as intended is fairly low. Thus, this is yet another point where hackers’ theory falls apart.
An important point is the statement that if the victim shares the “Hacker Who Has Access” email with someone, the scammer will publish the available videos. This is actually impossible, as the recipient can share the email by other means, for example in messenger. Lastly, the claim “I do not make any mistakes” sounds laughable, as the letter is pouring the mistakes one over another.
Scan your PC for malicious programs
Now that we’ve determined why this is a scam, there’s no reason to worry. But to be completely sure your system is clear of any malware, you can perform an anti-malware scan. For this purpose, I recommend using GridinSoft Anti-Malware. Follow the instructions below to scan and clean your system.

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.





