After a brief decline in loader-based malvertising, the FakeBat loader has re-emerged as a notable threat. This loader delivers follow-up malware payloads—in this case, a LummaC2 information-stealer designed to extract sensitive data from infected devices.
FakeBat Loader Returns to Malvertising
After a brief period of low activity, the FakeBat malware loader has reappeared through a malvertising campaign, targeting users through Google ads. This malware may also be known to you as Eugenloader or PaykLoader, with its main function being delivering other, more damaging malware after infecting a device.
The most recent attack of FakeBat involves a fake search ad for the productivity app Notion, which redirects users to a malicious website imitating the real Notion site. With an official logo and authentic-looking domain, the ad appears credible, making it an effective trap for unsuspecting users.
The search engine-based malvertising is a method where attackers leverage ad platforms like Google Ads to spread malware to a broad audience. While loaders like FakeBat were less common in recent months, now we can see that attackers can easily revert to trusted tactics whenever needed. Using Google Ads for brand impersonation remains a major vulnerability, as attackers can bypass detection to make fraudulent ads look legitimate.
Technical Overview of FakeBat’s Distribution and Evasion Techniques
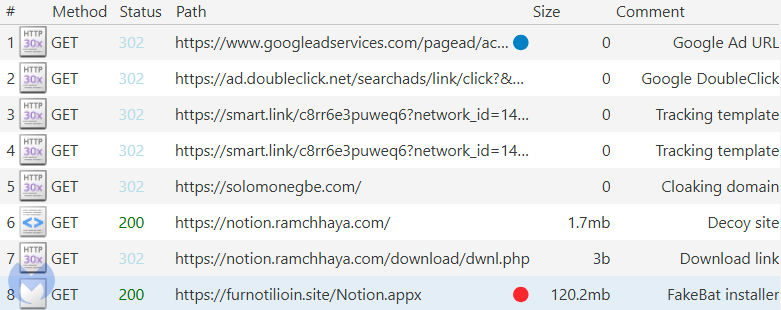
The distribution method of FakeBat relies on carefully orchestrated redirect sequences, which allow it to bypass standard security controls. When a victim clicks on the malicious Google ad, they’re first sent to a click-tracking template (such as “smart.link”).
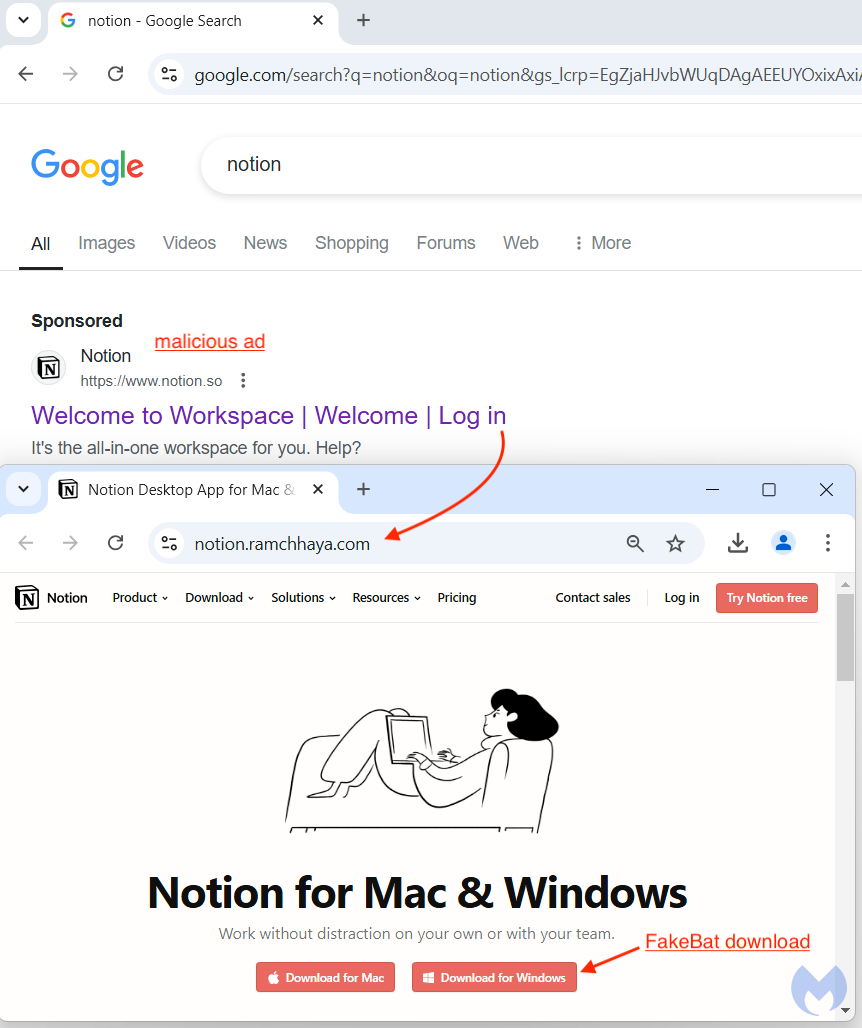
This step conceals the destination, redirecting users through a second, so-called cloaking domain (e.g., solomonegbe[.]com) before ultimately delivering them to the fake Notion website. If a user doesn’t fit the attacker’s target profile, the tracking template reroutes them to Notion’s actual website, making the fraudulent ad harder for Google to detect.
To execute its attack, FakeBat employs multiple stages, starting with an initial PowerShell script—a powerful Windows command line often misused by malware for its access to system processes. FakeBat’s code is obfuscated using .NET Reactor, a tool that scrambles the malware code to hinder analysis. The loader also uses process hollowing, a stealthy technique where it injects malicious code into MSBuild.exe (a legitimate Windows process), allowing it to run covertly without immediately alerting antivirus software.
FakeBat Delivers LummaC2 Stealer
As for the payload delivered by FakeBat in this campaitn, it is LummaC2 – an infostealer malware focused on collecting sensitive user information. It appeared at the beginning of 2024, and has become massively widespread almost immediately.
Once installed, LummaC2 can access browser history, login credentials, cryptocurrency wallet information, and other private data, relaying this to a command-and-control (C2) server. This version of LummaC2 included a unique identifier, signaling the presence of a potentially new or targeted campaign aimed at tracking specific victims.
How to Stay Protected?
To protect your system and avoid threats, remember two rules: cyber hygiene and preventive measures.The first rule is not to click on links unless you are sure they are safe. This applies to links in both emails and private messages.
Preventive measures include using advanced anti-malware software. Consider using GridinSoft Anti-Malware, as this solution offers advanced protection along with an Internet Security module, which is particularly effective against online threats.