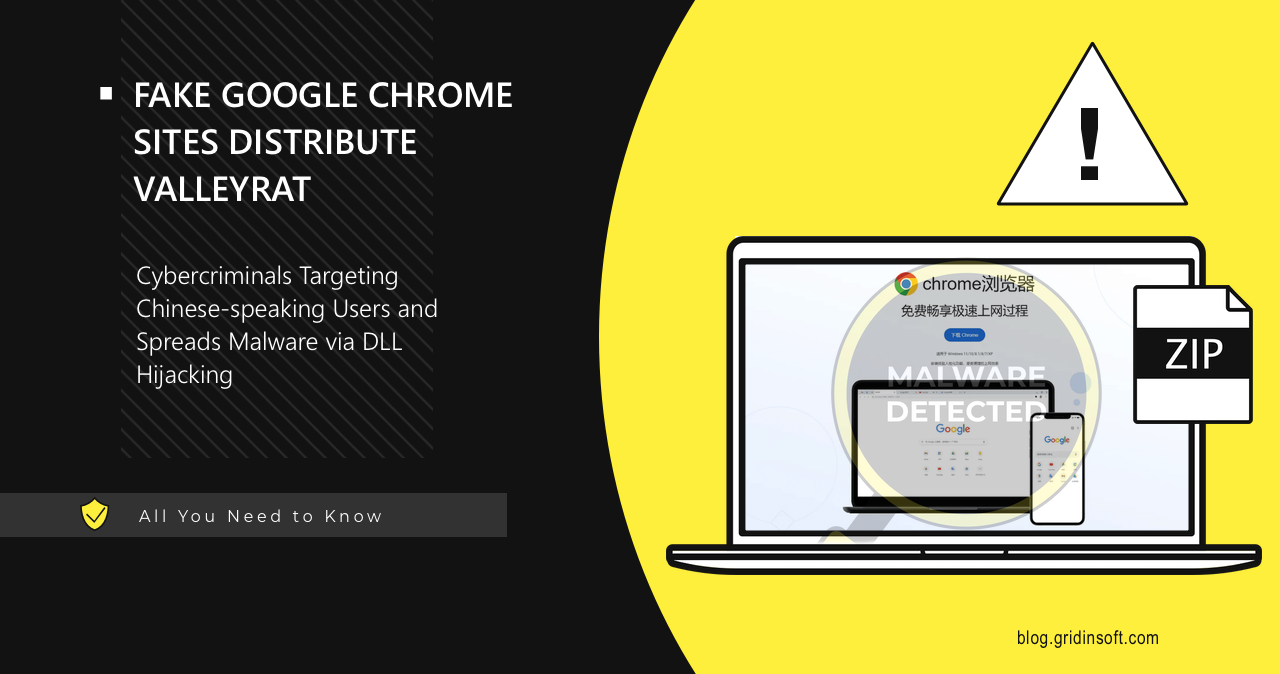
Cybercriminals have set up fake websites mimicking Google Chrome’s official download page to distribute the ValleyRAT malware. The campaign is attributed to the Silver Fox threat actor, which has historically targeted Chinese-speaking regions, including Hong Kong, Taiwan, and Mainland China.
Fake Google Chrome Sites Distribute ValleyRAT Malware via DLL Hijacking
Researchers at Morphisec Threat Labs discovered a malicious campaign targeting Chinese-speaking audiences. Victims searching for Google Chrome are redirected to a fake website, which offers a ZIP file containing a malicious executable (“Setup.exe”).
Experts say that the attackers have intensified their focus on high-value corporate positions, particularly in finance, accounting, and sales. This indicates a shift toward targeting individuals with access to sensitive data and critical business systems, who are quite expected to be the target.
Once executed, the installer checks for administrative privileges and downloads additional payloads. These include a legitimate Douyin/TikTok executable (“Douyin.exe”), which is used for DLL sideloading. A DLL file (“Tier0.dll”) is responsible for launching ValleyRAT, while another DLL file (“Sscronet.dll”) is designed to terminate specific processes on an exclusion list.
DLL hijacking is used to execute malicious code via legitimate executables. The attacker takes advantage of signed programs that are susceptible to DLL search order hijacking. This includes popular applications like WPS Office and Tencent software, as well as game-related binaries from Steam titles such as Left 4 Dead 2 and Killing Floor 2.
ValleyRAT Details
Current sample of the ValleyRAT written in C++ and compiled in Chinese. It operates as a remote access trojan with several malicious functionalities and includes keystroke logging to record user inputs and store them in a hidden file (“sys.key”). The malware captures screen activity using Windows API functions like EnumDisplayMonitors.
To maintain persistence, it creates a hidden executable (“GFIRestart64.exe”) and adds registry entries. Additionally, it employs anti-VM detection by scanning for specific processes and system attributes to avoid analysis. The malware establishes a connection with a C2 server to receive commands, execute arbitrary binaries, and exfiltrate data.
ValleyRAT is designed to monitor and control infected systems, enabling attackers to deploy additional malicious plugins for further damage. It can install additional malware, take screenshots, log keystrokes, download or steal files, and execute commands remotely. This allows cybercriminals to spy on victims, steal sensitive data, or use compromised machines for further attacks.
New Attack Vectors
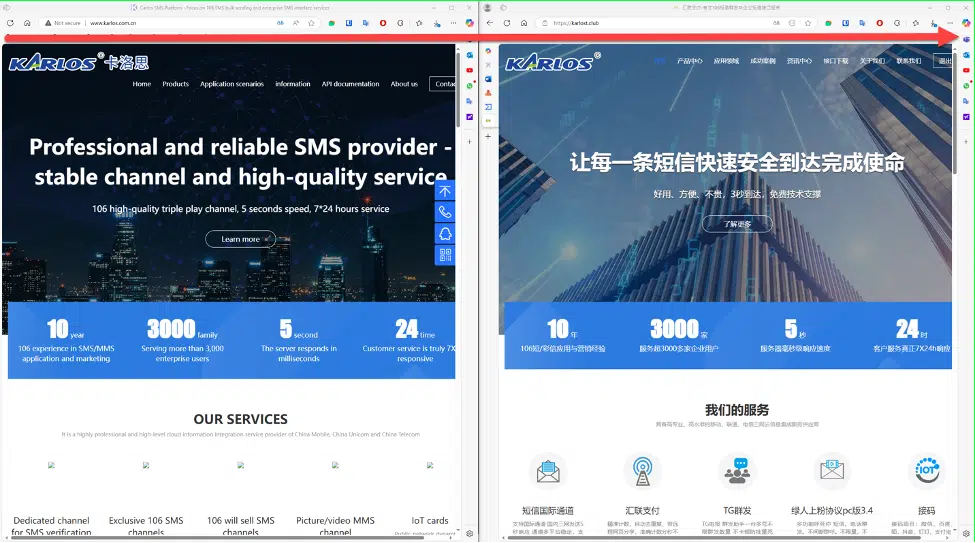
A notable change in Silver Fox’s tactics is the use of new phishing websites, such as anizom[.]com and karlost[.]club, to distribute the malware. The latter impersonates a Chinese telecom provider to increase legitimacy.
In previous campaigns, Silver Fox relied on malicious scripts (.bat and .ps1) to deploy RATs like GhostRAT and Purple Fox. The current attack demonstrates a shift towards more deceptive techniques, using fake software installers combined with DLL hijacking.
ValleyRAT injects malicious code into the legitimate Windows process “svchost.exe” to avoid detection. This is a common tactic for average malware. The malware stores its core components in an encrypted form within files like mpclient.dat.
Additionally, it evades security mechanisms by hooking critical Windows security functions such as AmsiScanString, AmsiScanBuffer, and EtwEventWrite. This effectively disables security monitoring features, making detection significantly more difficult. Given its focus on high-value corporate targets, businesses should adopt strict software download policies and monitor for unusual DLL loading behaviors to mitigate such threats.
How to Protect Against Malware?
The most effective protection against trojans is two things: vigilance during web surfing and reliable anti-malware software. In first case, it is essential for users to avoid suspicious sites like pirated content (programs, games, content) as well as online advertisements.
What about the second, anti-malware software would be the second line of defense if the first one didn’t work for some reason. I recommend considering GridinSoft Anti-Malware. Its functionality is capable of providing worthy protection from the threat and neutralize the threat before it will be downloaded and deployed.