Dire Wolf ransomware surfaced in late May 2025 as another player in the increasingly crowded ransomware landscape. What sets this threat apart isn’t revolutionary technology, but rather its methodical approach to double extortion and global targeting strategy.
Security researchers have tracked Dire Wolf attacks across multiple continents, affecting organizations from small businesses to larger enterprises. The ransomware’s creators chose Go as their programming language – a decision that tells us something about their technical sophistication and cross-platform ambitions.
For organizations, Dire Wolf serves as a reminder that effective ransomware doesn’t need to be revolutionary – it just needs to exploit common security gaps. The focus should remain on fundamental security practices: regular backups, network segmentation, user training, and incident response planning.
The mathematics of modern encryption mean that prevention remains far more effective than recovery. Organizations that find themselves facing Dire Wolf have already lost the most important battle – the one that happens before the ransomware executes.
In the end, Dire Wolf is less about the specific technical details and more about the ongoing failure of organizations to implement basic security hygiene. The wolves are always at the door; the question is whether you’ve bothered to lock it.
| Detection Name | Dire Wolf Ransomware |
| Threat Type | Ransomware (File Encryption + Data Theft) |
| Primary Function | Encrypts files and steals sensitive data for extortion |
| File Extension | .direwolf |
| Ransom Note | HowToRecoveryFiles.txt |
| Encryption Method | Curve25519 + ChaCha20 (Military-grade encryption) |
| Programming Language | Go (Golang) for cross-platform compatibility |
| Discovery Date | May 29, 2025 |
| Geographic Spread | Global (USA, Thailand, Australia, Bahrain, India, Italy, Canada, Mexico, Singapore, Taiwan, France) |
| Risk Level | CRITICAL – Complete file encryption with data theft |
Text in the ransom note:
Dear Mr or Ms,
If you are reading this message, it means that:
- your network infrastructure has been compromised
- critical data was leaked
- files are encrypted
--------------------------------------------------------------------------
The best and only thing you can do is to contact us
to settle the matter before any losses occurs.
--------------------------------------------------------------------------
We can maintain confidentiality for 3 days for you, during which we will not disclose any information about your intrusion or data leakage.
We can extend the confidentiality period free of charge until we reach an agreement if you contact us within 3 days and communicate effectively with us.
If the confidentiality period expires, we will disclose the relevant information.
We provide complimentary decryption testing services. For specific details, please contact us.
--------------------------------------------------------------------------
We have provided a sample document as proof of our possession of your files and you can download and check it:
- hxxxs://gofile.io/d/3*****
Please be advised that your files are scheduled for public release after 30 working days.
If you want to secure your files, we urge you to reach out to us at your earliest convenience.
--------------------------------------------------------------------------
Contact Details:
- live chat room:
- url:hxxx://direwolf3ddtab5anvhulcelauvoxu2a7l264hqs6vtxtgrqsjfvodid.onion/
- roomID: thairung
- username: tha*****
- password: E27*****
--------------------------------------------------------------------------
Our official website:
- url:hxxx://direwolfcdkv5whaz2spehizdg22jsuf5aeje4asmetpbt6ri4jnd4qd.onion/
--------------------------------------------------------------------------
How to access .onion website:
1.Download and install TOR Browser https://torproject.org
2.Open it and try to access our onion address
3.Maybe you need to use VPN if it can not open our onion address
Immediate Response Steps
Time is critical when dealing with ransomware. Your first actions determine how much damage the attack causes. Here’s what to do right now.
Step 1: Disconnect from the Internet
Stop the ransomware from spreading to other computers on your network. Disconnect immediately.
- Unplug your Ethernet cable from your computer
- Turn off your WiFi adapter
- Disable network connections in Windows:
Settings > Network & Internet > Status > Change adapter options - Right-click each network adapter and select “Disable”
Step 2: Identify Infected Systems
Check which computers on your network are affected. Look for these signs:
- Files with .direwolf extension
- Desktop wallpaper changed to ransom message
- HowToRecoveryFiles.txt file on desktop
- Unusual system slowness or crashes
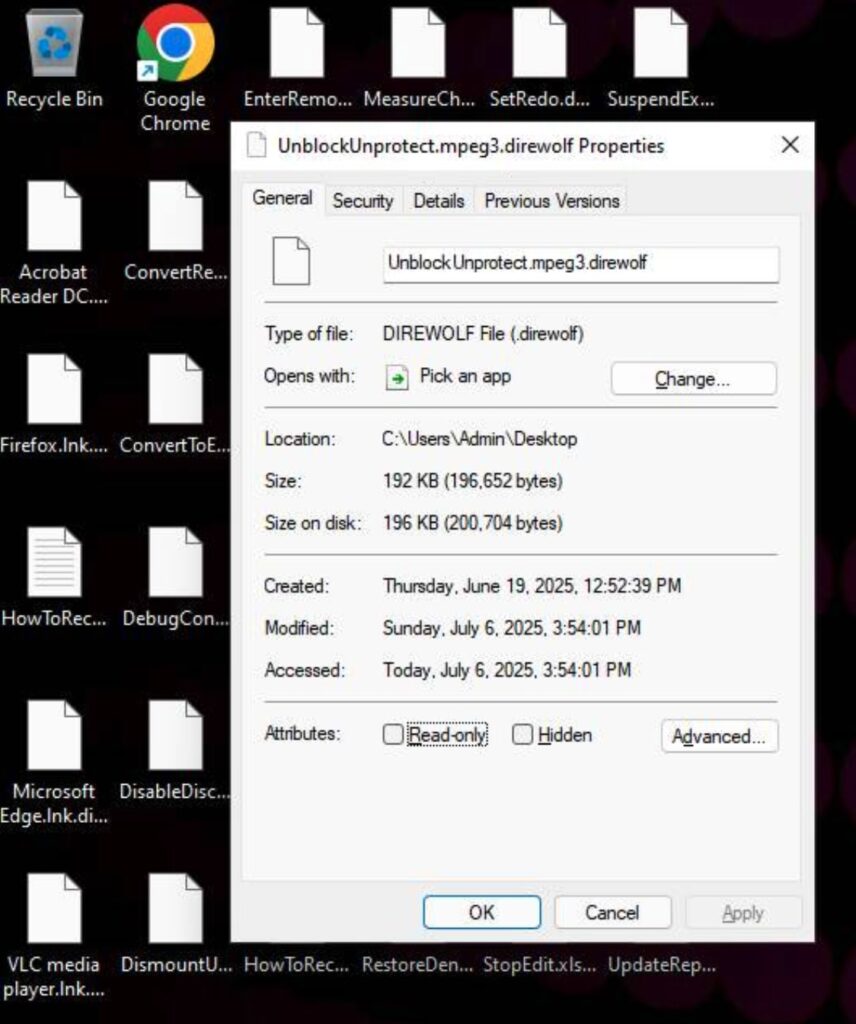
Step 3: Document the Attack
Take screenshots of the ransom note and affected files. You’ll need this information for recovery.
- Screenshot the ransom note
- List encrypted file types and locations
- Note the exact time you discovered the attack
- Record any suspicious emails or downloads from the past 48 hours
Dire Wolf Technical Analysis
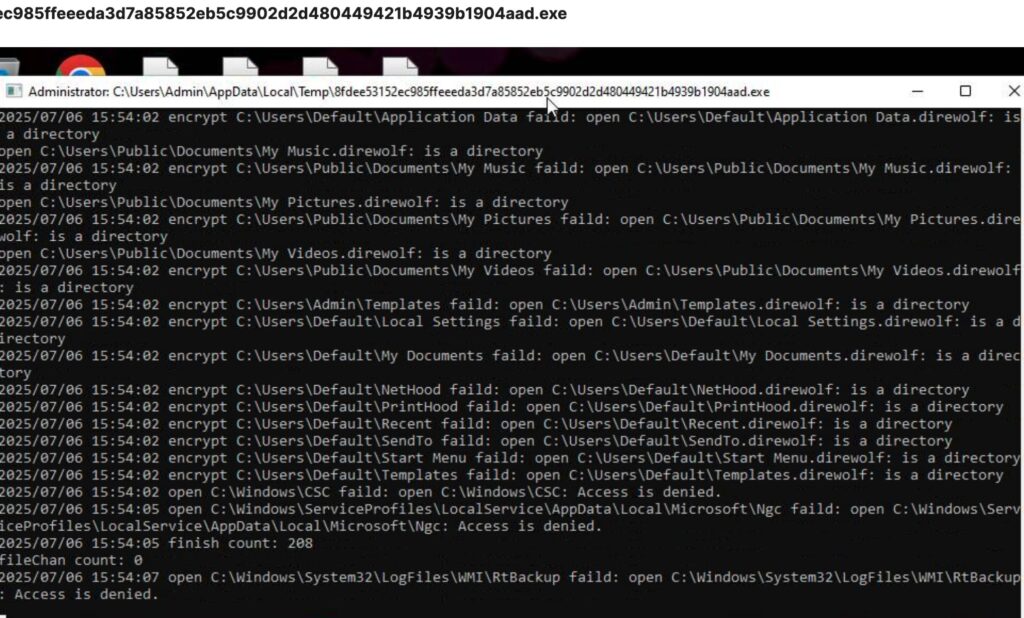
Understanding how Dire Wolf works helps you protect against future attacks. The ransomware uses sophisticated techniques that make file recovery nearly impossible without the decryption key.
Encryption Implementation
Dire Wolf uses military-grade encryption that cannot be broken:
- Curve25519: Modern elliptic curve cryptography for key exchange
- ChaCha20: Stream cipher developed by Google and used in TLS
- Go Programming Language: Cross-platform compatibility for Windows, Linux, and macOS
- Unique Keys: Each victim gets a different encryption key
Attack Timeline Strategy
Dire Wolf operators follow a calculated timeline (see more details on tria.ge) designed to maximize pressure:
- Day 1-3: “Confidentiality window” – No data leak if you contact them
- Day 4-30: Escalating pressure with threats of data publication
- Day 30+: Stolen data published on dark web leak sites
Double Extortion Tactics
Dire Wolf doesn’t just encrypt files. The attackers also steal your data before encryption:
- Initial Access: Compromised RDP, phishing emails, or software vulnerabilities
- Environment Mapping: Scan network for valuable targets and data
- Data Harvesting: Steal sensitive documents, databases, and credentials
- File Encryption: Encrypt files using Curve25519 + ChaCha20
- Ransom Demand: Threaten to publish stolen data if payment isn’t made
Security Vendor Detection
Major antivirus companies now detect Dire Wolf ransomware. The signatures vary because the threat is still being analyzed:
- Microsoft Defender: Trojan:Win32/Casdet!rfn, Ransom:Win64/Dire Wolf.A
- Gridinsoft: Ransom.Win64.DireWolf.dd!s1
- Dr.Web: Trojan.Encoder.42458, Trojan.Encoder.42473
- BitDefender: Trojan.Generic.38142181, Trojan.Generic.38138312
- ESET: A Variant Of WinGo/Filecoder.JB
- Kaspersky: Trojan.Win32.DelShad.nrj, Trojan.Win32.DelShad.nrn
- Trend Micro: Ransom.Win64.DIREWOLF.THFBOBE
If your antivirus detected Dire Wolf, the damage might already be done. The encryption happens faster than most security software can stop it.
Manual Dire Wolf Removal Steps
Manual removal focuses on cleaning the ransomware executable and stopping ongoing processes. This won’t decrypt your files, but it prevents further damage.
Step 1: Boot into Safe Mode
Safe Mode prevents the ransomware from running during cleanup:
- Press
Windows + Rto open Run dialog - Type
msconfigand press Enter - Go to Boot tab and check “Safe boot”
- Select “Minimal” option
- Click Apply and restart your computer
Step 2: Identify Malicious Processes
Look for suspicious processes that might be Dire Wolf components:
- Press
Ctrl + Shift + Escto open Task Manager - Click “More details” if needed
- Look for processes with random names or high CPU usage
- Check the “Details” tab for suspicious .exe files
- Note the location of suspicious processes
Step 3: Delete Ransomware Files
Remove Dire Wolf executables from common infection locations:
- Open File Explorer and navigate to:
C:\Users\%USERNAME%\AppData\Local\Temp - Look for recently created .exe files with random names
- Delete suspicious executables (check creation dates)
- Check Downloads folder:
C:\Users\%USERNAME%\Downloads - Remove any suspicious files downloaded in the past 48 hours
Step 4: Clean Registry Entries
Remove Dire Wolf startup entries from Windows Registry:
- Press
Windows + Rand typeregedit - Navigate to:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run - Look for entries with random names or suspicious paths
- Delete any entries pointing to ransomware executables
- Check:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
Step 5: Remove Scheduled Tasks
Check for persistent ransomware tasks:
- Press
Windows + Rand typetaskschd.msc - Expand “Task Scheduler Library”
- Look for tasks with random names or suspicious triggers
- Delete any tasks that run suspicious executables
- Check task history for recently executed suspicious tasks
Step 6: Clear System Restore Points
Dire Wolf may have infected backup files:
- Right-click “This PC” and select “Properties”
- Click “System Protection” on the left
- Select your main drive and click “Configure”
- Click “Delete” to remove all restore points
- Create a new restore point after cleanup
Automatic Removal with GridinSoft Anti-Malware
Manual removal can be complex and time-consuming. For a faster, more reliable solution, GridinSoft Anti-Malware offers automatic detection and removal of Dire Wolf ransomware components. Professional anti-malware software can find hidden components and registry changes that you might miss.
GridinSoft Anti-Malware specializes in advanced threat detection. It can identify Go-based malware like Dire Wolf and clean infected systems completely.

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.

File Recovery Options
Dire Wolf uses unbreakable encryption. Your files cannot be decrypted without the attackers’ key. Here are your recovery options:
Backup Recovery
Your best option is restoring from clean backups:
- Check external drives that weren’t connected during the attack
- Look for cloud backups (OneDrive, Google Drive, Dropbox)
- Verify backup integrity before restoring
- Restore backups to a clean system only
Shadow Volume Copies
Windows might have automatic backups that survived:
- Download Shadow Explorer from shadowexplorer.com
- Install and run the software
- Select your drive and a date before the infection
- Browse for important files and export them
File Recovery Software
Try recovering deleted originals (low success rate):
- Use Recuva or similar file recovery tools
- Scan for recently deleted files
- Look for temporary file versions
- Check application cache folders
How to Decrypt Dire Wolf Files
Let’s address the question everyone asks: “Can I decrypt my files without paying?” The short answer is no. Here’s why and what you can do instead.
Why Decryption Is Impossible
Dire Wolf uses Curve25519 + ChaCha20 encryption. This isn’t some amateur crypto that security researchers can crack:
- Mathematical Reality: Breaking this encryption would require more computing power than exists on Earth
- Unique Keys: Each victim gets a different encryption key stored only on the attackers’ servers
- No Weaknesses: Security experts have found no flaws in the encryption implementation
- Time Factor: Even with quantum computers, decryption would take millions of years
Free Decryption Tools Status
Security companies regularly release decryption tools for ransomware with flawed encryption. Here’s the current status for Dire Wolf:
- No-More-Ransom Project: No decryption tool available
- Emsisoft: No decryption tool available
- Kaspersky: No decryption tool available
- Avast: No decryption tool available
Check these resources periodically in case researchers discover a flaw, but don’t hold your breath. Modern ransomware like Dire Wolf uses proper encryption.
Avoid Fake Decryption Tools
Scammers exploit ransomware victims with fake decryption tools. Here’s how to spot them:
- Payment Required: Legitimate decryption tools are always free
- Suspicious Websites: Only download from official security company sites
- Too Good to Be True: If it claims to decrypt any ransomware, it’s fake
- Multiple Infections: Fake tools often install more malware
What About Paying the Ransom?
The attackers do have the decryption key. But paying comes with serious risks:
- No Guarantee: 40% of victims who pay never get their files back
- Partial Recovery: Some victims receive decryption tools that only work on some files
- Repeat Attacks: You’re marked as someone who pays, increasing future attacks
- Legal Issues: Paying ransoms may violate sanctions laws in some countries
- Funding Crime: Your payment funds more ransomware attacks
Alternative Recovery Methods
Instead of trying to decrypt files, focus on these proven recovery methods:
- Restore from Backups: Your best bet if you have clean backups
- Shadow Volume Copies: Windows automatic backups that might survive
- File Recovery Tools: Might find deleted originals before encryption
- Previous Versions: Windows File History might have older copies
- Application Caches: Some programs keep temporary copies
- Dire Wolf files cannot be decrypted without the attackers’ key
- No legitimate free decryption tools exist for this ransomware
- Paying the ransom is risky and may not work
- Focus on backup recovery and file restoration instead
- Accept that some files may be permanently lost
Frequently Asked Questions
What is Dire Wolf ransomware and why is it dangerous?
Dire Wolf is a ransomware that encrypts your files and steals your data. It’s dangerous because it uses military-grade encryption that cannot be broken. The attackers also threaten to publish your stolen data if you don’t pay the ransom.
How did Dire Wolf get on my computer?
Dire Wolf spreads through phishing emails, compromised remote desktop connections, and software vulnerabilities. Attackers often use legitimate-looking email attachments or exploit unpatched security holes in your system.
Can I decrypt my files without paying the ransom?
No, Dire Wolf uses Curve25519 + ChaCha20 encryption which is mathematically impossible to break. Your only options are restoring from backups or using file recovery tools to find deleted originals.
Should I pay the ransom to get my files back?
Security experts recommend against paying ransoms. There’s no guarantee you’ll get your files back, and payment encourages more attacks. Focus on backup recovery instead.
How can I prevent Dire Wolf ransomware?
Keep regular offline backups, update your software, use strong passwords, and avoid suspicious emails. Install reputable antivirus software and keep Windows Defender enabled.
What if manual removal doesn’t work?
Use GridinSoft Anti-Malware for automatic detection and removal. Professional anti-malware tools can find hidden components that manual removal might miss.
How do I know if my computer is completely clean?
Run a full system scan with GridinSoft Anti-Malware after manual cleanup. Check that no suspicious processes are running and that the ransom note files are gone.
Can Dire Wolf spread to other computers on my network?
Yes, Dire Wolf can spread through network connections. Disconnect infected computers immediately and scan all systems on your network for the threat.
Dire Wolf in the Ransomware Landscape
Dire Wolf represents the evolution of ransomware tactics. The threat shows several concerning trends:
Technical Sophistication
Using Go programming language shows the attackers understand modern development practices. Go creates efficient, cross-platform malware that’s harder to analyze than traditional Windows-only threats.
Double Extortion Standard
What was once exclusive to major ransomware groups is now standard practice. Even new players like Dire Wolf implement data theft alongside encryption. This mirrors the evolution we’ve seen with groups like LockBit and REvil.
Global Coordination
Attacks across multiple continents indicate organized operations with significant resources. This isn’t a lone hacker but a coordinated criminal enterprise.
Psychological Manipulation
The 3-day “confidentiality window” creates false urgency. It’s designed to prevent victims from consulting security professionals or law enforcement.
Understanding these trends helps organizations prepare for the evolving ransomware landscape. Consider reading our analysis of nation-state threat actors to understand the broader context of modern cyber threats.
Quick Summary
- Uses unbreakable Curve25519 + ChaCha20 encryption
- Written in Go for cross-platform compatibility
- Steals data before encryption (double extortion)
- Files cannot be decrypted without paying ransom
- Focus on backup recovery, not file decryption
- Use GridinSoft Anti-Malware for thorough cleanup
- Prevent future attacks with offline backups
Dire Wolf ransomware represents competent execution of proven attack methods. The threat actors understand both technical and psychological aspects of successful extortion campaigns.
For victims, the focus should be on cleanup and recovery from backups rather than attempting to decrypt files. The mathematics of modern encryption make file recovery without the key virtually impossible.
Prevention remains more effective than recovery. Organizations and individuals who maintain proper backups and security practices can recover from Dire Wolf attacks without paying ransoms.
The emergence of threats like Dire Wolf reinforces the importance of basic security hygiene. Regular backups, software updates, and security awareness training remain the best defenses against ransomware attacks. For comprehensive protection strategies, consider our guide on internet safety tips and cybersecurity best practices.





