CipherLocker is yet another malware variant that encrypts user data and demands a ransom. The only difference between this threat and its brethren is the unrealistic greed of its developers, who ask for as much as 1.5 BTC per file. Today I will shed some light on this threat and tell you what it is and how to get rid of it.
CipherLocker Ransomware Overview
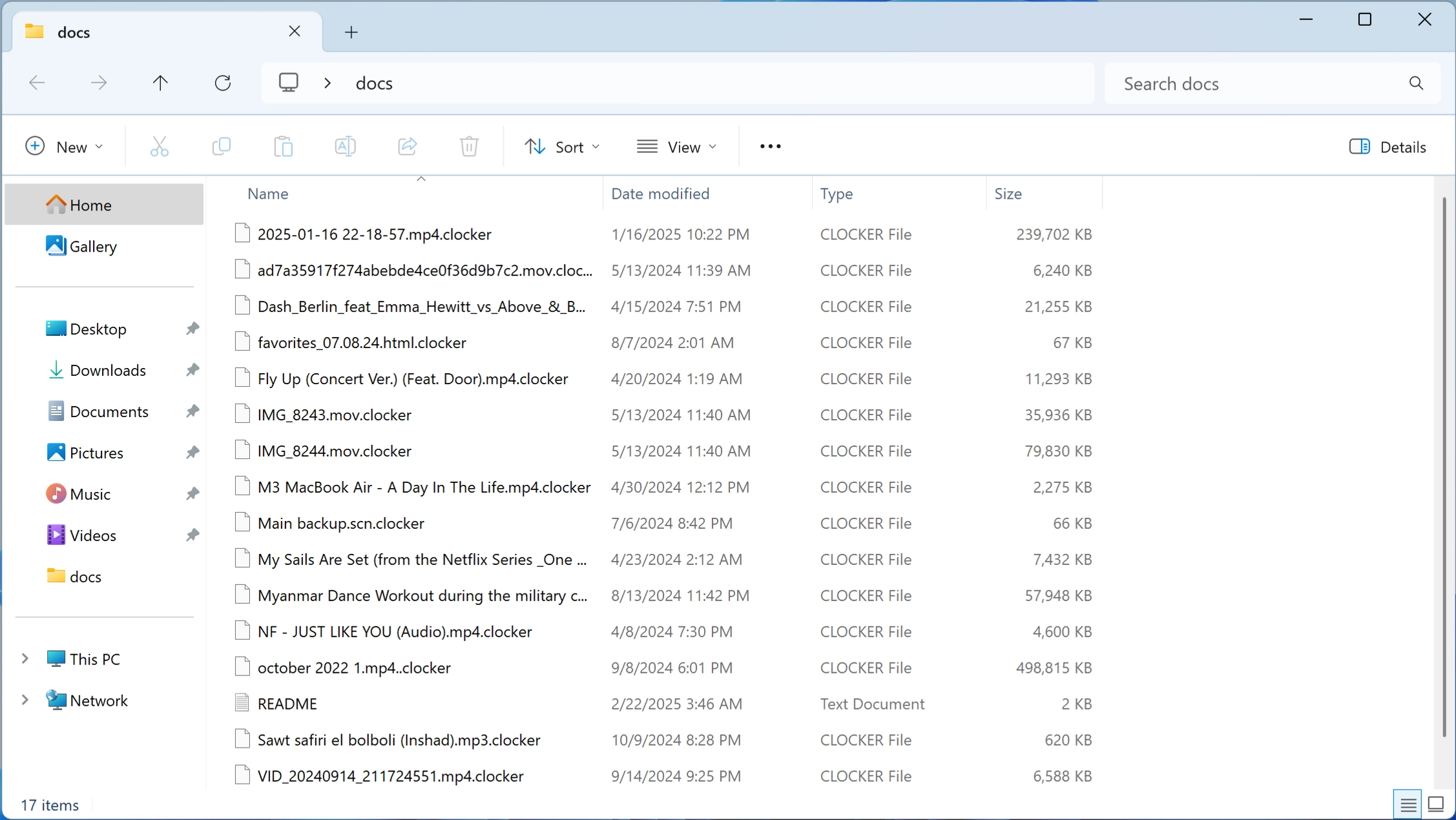
CipherLocker is a newly identified ransomware variant that encrypts user data and appends the “.clocker” extension to the affected files. This follows a typical attack pattern—locking victims’ files and demanding a ransom for decryption. While it may seem like a no name ransomware, it’s just as good as its more established counterparts and can also give you trouble.
This ransomware has a pretty common distribution pattern for this type of malware. It is spreading primarily through infected email attachments, torrents, and malicious advertisements. The attackers behind CipherLocker demand payment in Bitcoin, also popular among cybercriminals. Based on current analysis, no free decryption tool is available.
Ransom Note Overview
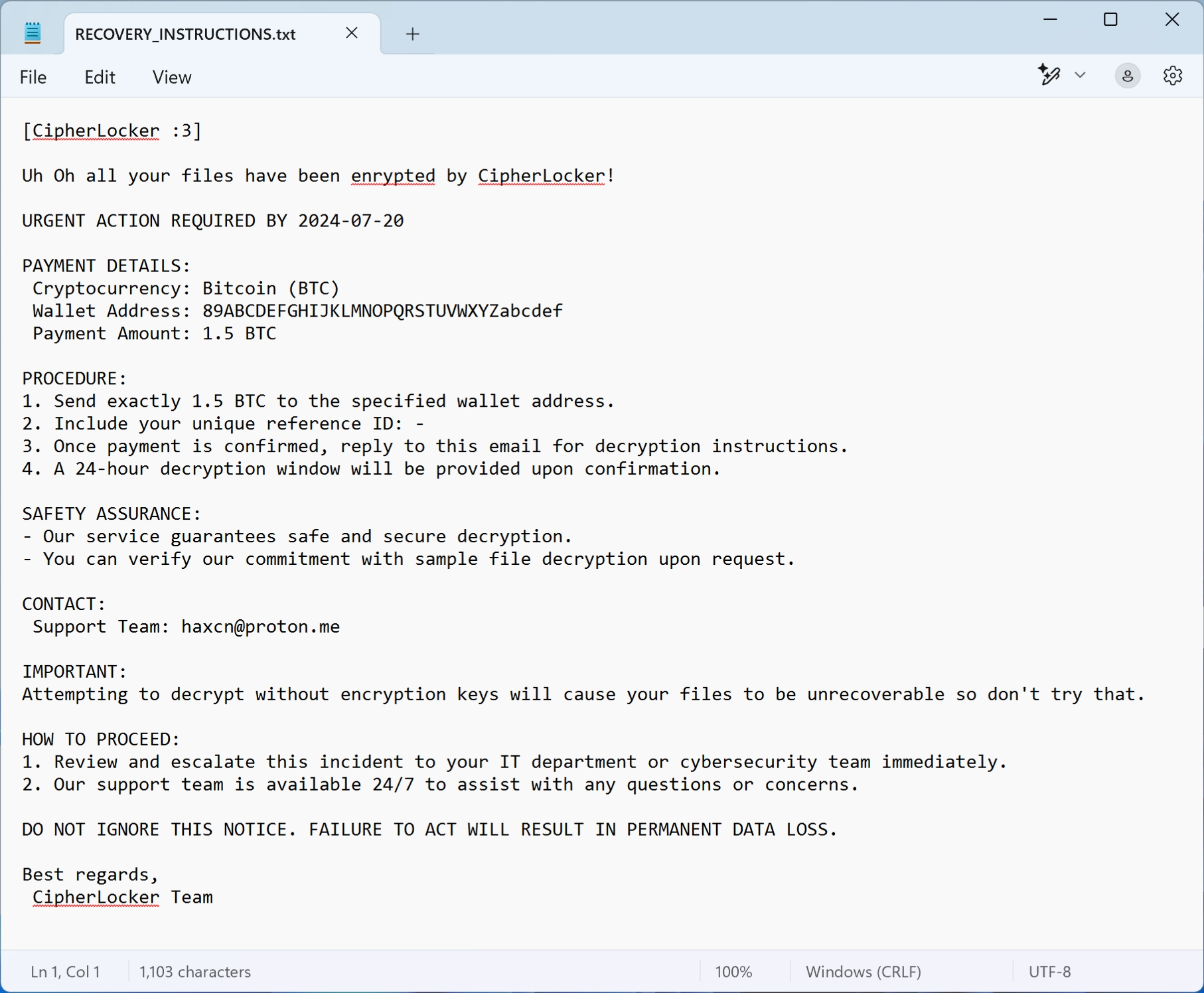
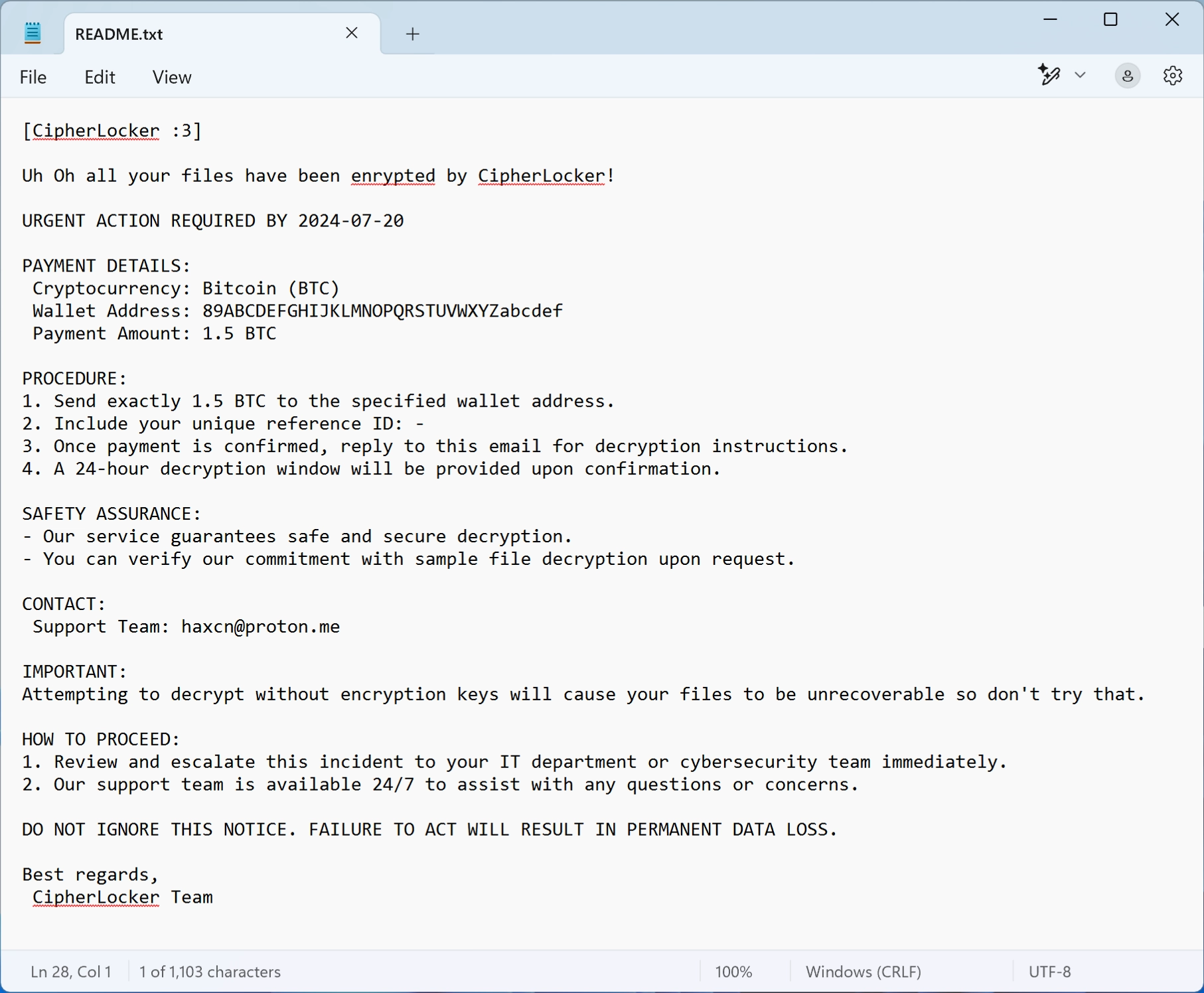
In each folder with locked files, CipherLocker delivers its ransom note. This is a text file, typically named “README.txt” or “RECOVERY_INSTRUCTIONS.txt.” The message informs victims that their files have been encrypted and that all potential backup solutions, including Windows Shadow Copies and recycle bin contents, have been removed. To regain access to their files, victims are instructed to pay 1.5 BTC (~$147 998,37 at the current price) to a specified Bitcoin wallet.
The ransom note sets a strict deadline, and says that failure to comply will result in permanent data loss. The attackers claim that payment guarantees a safe decryption process, even offering sample file decryption as proof. Victims are provided with an email address ([email protected]) for further communication. However, there is no certainty that paying will lead to file recovery, as cybercriminals (especially no name) frequently fail to provide decryption keys even after receiving payment.
How Does It Work?
CipherLocker operates using a multi-stage infection process. Once executed on a system, it immediately scans for user files and encrypts them with a strong encryption algorithm, adding the “.clocker” extension. This makes the files inaccessible without the corresponding decryption key, which only the attackers possess. Although some ransomware sometimes encrypts only part of the files, this is not specified with a particular sample.
The CipherLocker also deletes Windows Volume Shadow Copies, disables system restore points, and wipes backups stored on the machine. This ensures that users cannot recover their data through standard recovery methods. Security researchers have identified that the ransomware uses Telegram as an intermediary command-and-control (C2) channel.
How to Remove Virus?
The first and most critical step in dealing with CipherLocker is to remove the ransomware from the system. This will prevent further encryption of new or recovered files. Before attempting file recovery, users should boot their computers into Safe Mode with Networking to prevent the ransomware from actively running. But before that, download and install GridinSoft Anti-Malware by clicking the banner you see below.
Once in Safe Mode, run the Full scan with GridinSoft Anti-Malware. This will search the system down to the most remote config files, guaranteeing the removal of CipherLocker virus. Additionally, users should always have proactive security measures in place to prevent such infections in the future. Regularly updated anti-malware solutions can block ransomware before it executes, minimizing damage.
Can I Recover Encrypted Files?
Unfortunately, there is no publicly available decryption tool for CipherLocker, meaning that recovering files without the attackers’ decryption key is not feasible. However, paying the ransom is strongly discouraged, as there is no guarantee that victims will receive working decryption software after payment. Supporting cybercriminals financially also fuels further attacks against others.
Instead, users should focus on prevention and best security practices. Since CipherLocker spreads primarily through pirated software and phishing campaigns, avoiding unverified downloads and suspicious email attachments is crucial. Regularly backing up important files to an offline or cloud-based storage system ensures that even if ransomware strikes, data loss is minimized. For those without backups, forensic data recovery specialists may be able to assist in some cases, but success is not guaranteed.