In June this year, researchers from Check Point discovered a number of dangerous vulnerabilities that opened for attacks the Amazon Alexa virtual assistant and its users. The problem was in CORS and XSS bugs, which affected several Amazon subdomains, and in configuration issues. By exploiting these bugs, attackers could gain access to personal data (usernames,… Continue reading Vulnerabilities in Amazon Alexa opened access to user data for outsiders
Author: Vladimir Krasnogolovy
Vladimir is a technical specialist who loves giving qualified advices and tips on GridinSoft's products. He's available 24/7 to assist you in any question regarding internet security.
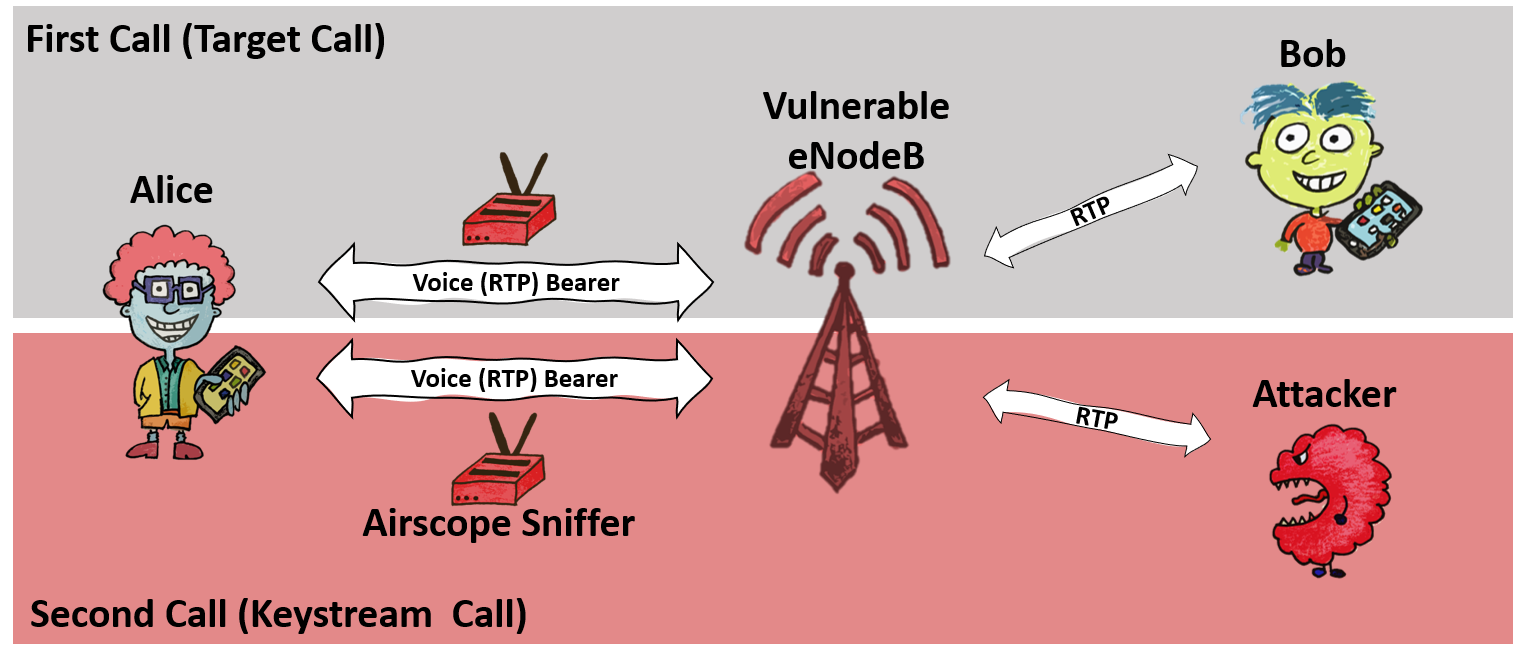
ReVoLTE attack allows overhearing other people’s conversations in LTE networks
Experts from the Ruhr University and New York University in Abu Dhabi have published information about the ReVoLTE attack, which allows decrypting and overhearing other people’s conversations on LTE networks. This attack already has its own website, and at the Usenix conference researchers demonstrated a video presentation of their report. I’d like to note that… Continue reading ReVoLTE attack allows overhearing other people’s conversations in LTE networks
Mozilla Downsizing Affects Security Professionals
Earlier this week, Mozilla fired 250 employees, and another 60 employees moved to other teams. The media reports that Mozilla’s downsizing has seriously affected security professionals. Mozilla head and Mozilla Foundation CEO Mitchell Baker said the organization is forced to rethink its plans and adapt to the new realities that have changed greatly after COVID-19,… Continue reading Mozilla Downsizing Affects Security Professionals
Citrix expects attacks on fresh issues in XenMobile
Citrix engineers released a number of Citrix Endpoint Management patches this week. Citrix expects attacks on XenMobile Server corporate mobile device management systems. These issues give an attacker the ability to gain administrative privileges on vulnerable systems. The severity of the encountered issues, which received CVE IDs CVE-2020-8208, CVE-2020-8209, CVE-2020-8210, CVE-2020-8211, and CVE-2020-8212, differs depending… Continue reading Citrix expects attacks on fresh issues in XenMobile
HIBP (Have I Been Pwned?) leak aggregator opens the source code
Founder of Have I Been Pwned? (HIBP) Troy Hunt announced that after a series of unsuccessful attempts to sell the project, about which he talked this spring, he decided to open the source code. Let I remind you that HIBP, founded in 2013, is a service for verifying credentials for compromise. Collecting information about various… Continue reading HIBP (Have I Been Pwned?) leak aggregator opens the source code
Kr00k problem threatens devices with Qualcomm and MediaTek Wi-Fi chips
In early 2020, ESET experts spoke about the Kr00k vulnerability (CVE-2019-15126), which can be used to intercept and decrypt Wi-Fi (WPA2) traffic. Then it was reported that any devices using the solutions of Cypress Semiconductor and Broadcom, from laptops and smartphones to routers and IoT devices, are susceptible to this problem. Now there is information… Continue reading Kr00k problem threatens devices with Qualcomm and MediaTek Wi-Fi chips
Intel investigates data leak: 20 GB of source codes and documents
Swiss programmer Till Kottmann has been studying various dumps in the public domain for a long time and it looks like he found something interesting, so now the IT giant Intel is investigating the data leak. Till Kottmann collects accidentally dumped data from large technological companies, information from which leaks through misconfigured repositories, cloud servers… Continue reading Intel investigates data leak: 20 GB of source codes and documents
US authorities offered $10000000 for information on planned cyberattacks for the elections
Less than 100 days are left before the start of the US presidential elections, and the US authorities have announced that they are ready to pay $10 000 000 for any information about people working for foreign governments and preparing cyberattacks for the upcoming elections. Namely, they try to protect employees of the US election… Continue reading US authorities offered $10000000 for information on planned cyberattacks for the elections
295 Chrome extensions injected ads in search results
AdGuard analysts have identified 295 malicious extensions in the Chrome Web Store that have been installed over 80,000,000 times. These Chrome browser extensions injected ads into Google and Bing search results. Most of the dangerous extensions masked themselves as ad blockers and were easily found by queries such as adblock, adguard, ublock, ad blocker, and… Continue reading 295 Chrome extensions injected ads in search results
Google: 11 0-day vulnerabilities identified in the first half of 2020
Google Project Zero experts estimate that 11 0-day vulnerabilities, actively exploited by hackers, were identified in the first half of 2020. The current number of 0-day problems indicates that, most likely, that overall this year will be identified the same number of zero-day vulnerabilities, as in 2019 (20). The link above leads to the company’s… Continue reading Google: 11 0-day vulnerabilities identified in the first half of 2020