5 Security Mistakes You’re Making On Social Media
Leading digital life on various social media platforms can sometimes be a…
DDoS Attacks: 6 Tried-and-Tested Methods How to Prevent It
DDoS Attacks: 6 Tried-and-Tested Methods How to Prevent It Before considering how…
100% Disk Usage Windows 10: How to Fix Disk Issue
100% disk usage is a widespread problem among Windows users that has…
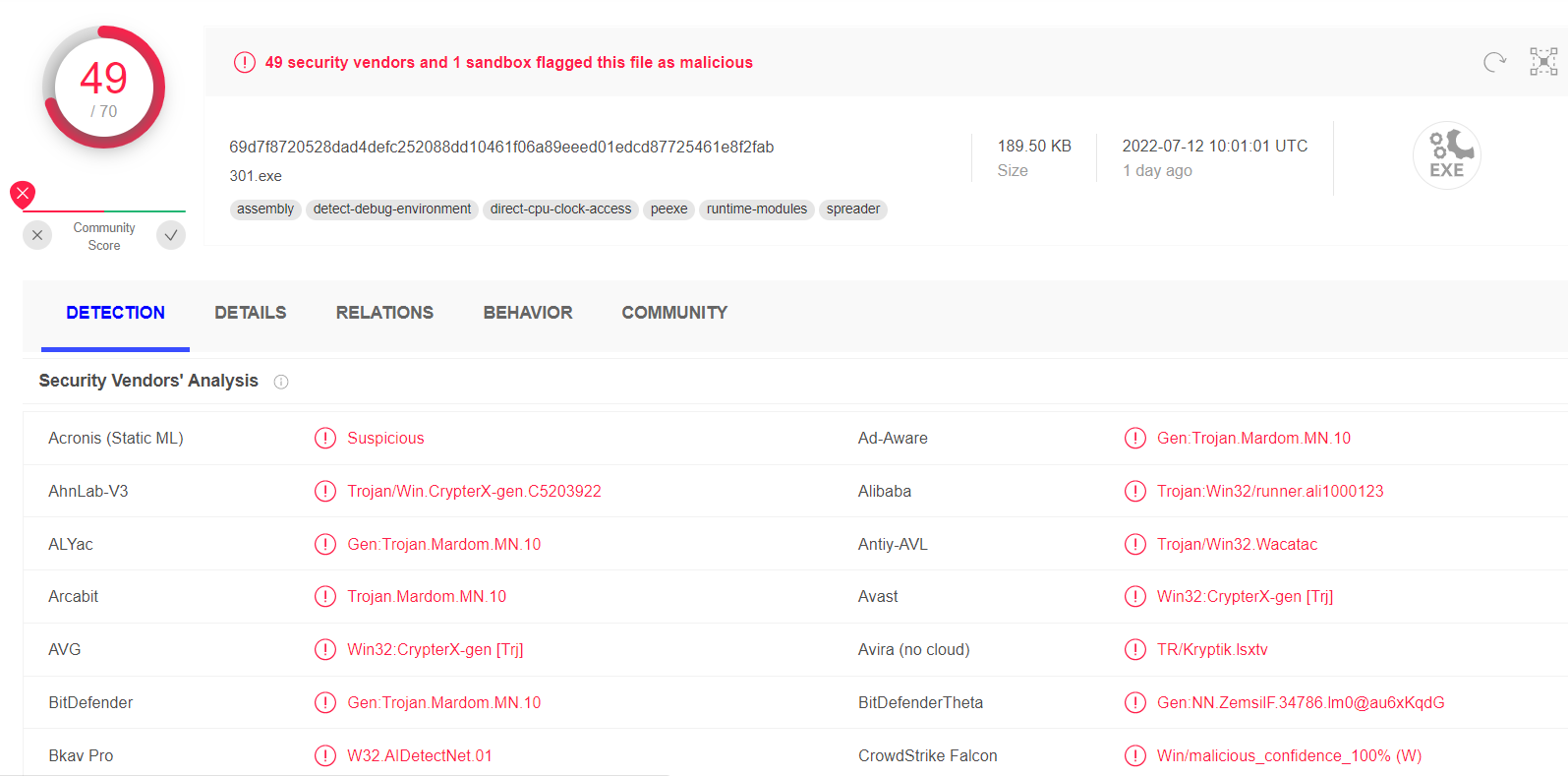
U2K Ransomware Strikes, Thousands Of Victims
U2K ransomware, probably the rising star on the ransomware arena, appeared on…
Types of Computer Virus
Computer viruses can steal and facilitate the dissemination of your confidential information,…
Bandai Namco Hacked, ALPHV Group Claims
On Monday, June 11, 2022, the information about the cyberattack on the…
Search Marquis: How to prevent it
What is Search Marquis? Search Marquis is a type of malware that…
Which Deadliest Virus in History? Types to Remember
What is the Deadliest Virus in History? On November 11, 1983, the…
Conti’s blockchain plans: an ominous prospect
Earlier this year, on February 22, Conti’s gang became popular because of…
Russian Organizations Under Attack By Chinese APTs
Unveiling a recent cyber saga, the experts at SentinelLabs have unearthed a…
Does My Phone Have a Virus? Phone Viruses Explained
Phone malware is obviously less widespread – and discussed – as a…
Securing Remote Desktop (RDP)
In 1998, Microsoft introduced the Windows Terminal Server as an add-on to…