Mandiant Account in X Hacked to Spread Cryptocurrency Scams
The Twitter account of Google's Mandiant cybersecurity service has been hacked to…
Qualcomm RCE Vulnerabilities Expose Millions of Users
Vulnerability in several Qualcomm chipsets allows for remote code execution during the…
Black Basta Ransomware Free Decryptor Available
SRLabs researchers published a free decryptor for BlackBasta ransomware. They discovered the…
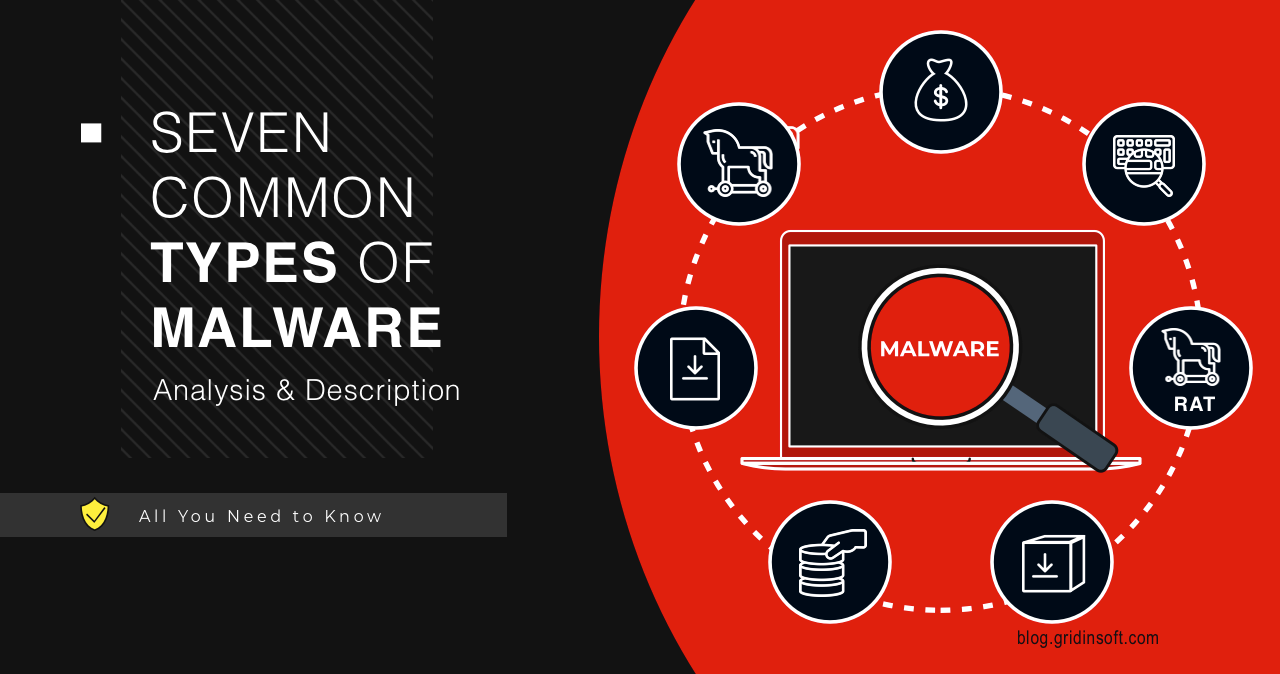
Seven Common Types of Malware – Analysis & Description
In the intricate landscape of cybersecurity, comprehending the various forms of malware…
DLL Search Order Hijacking Technique Bypasses Protection
A new DLL (Dynamic Link Library) Search Order Hijacking variant emerged. This…
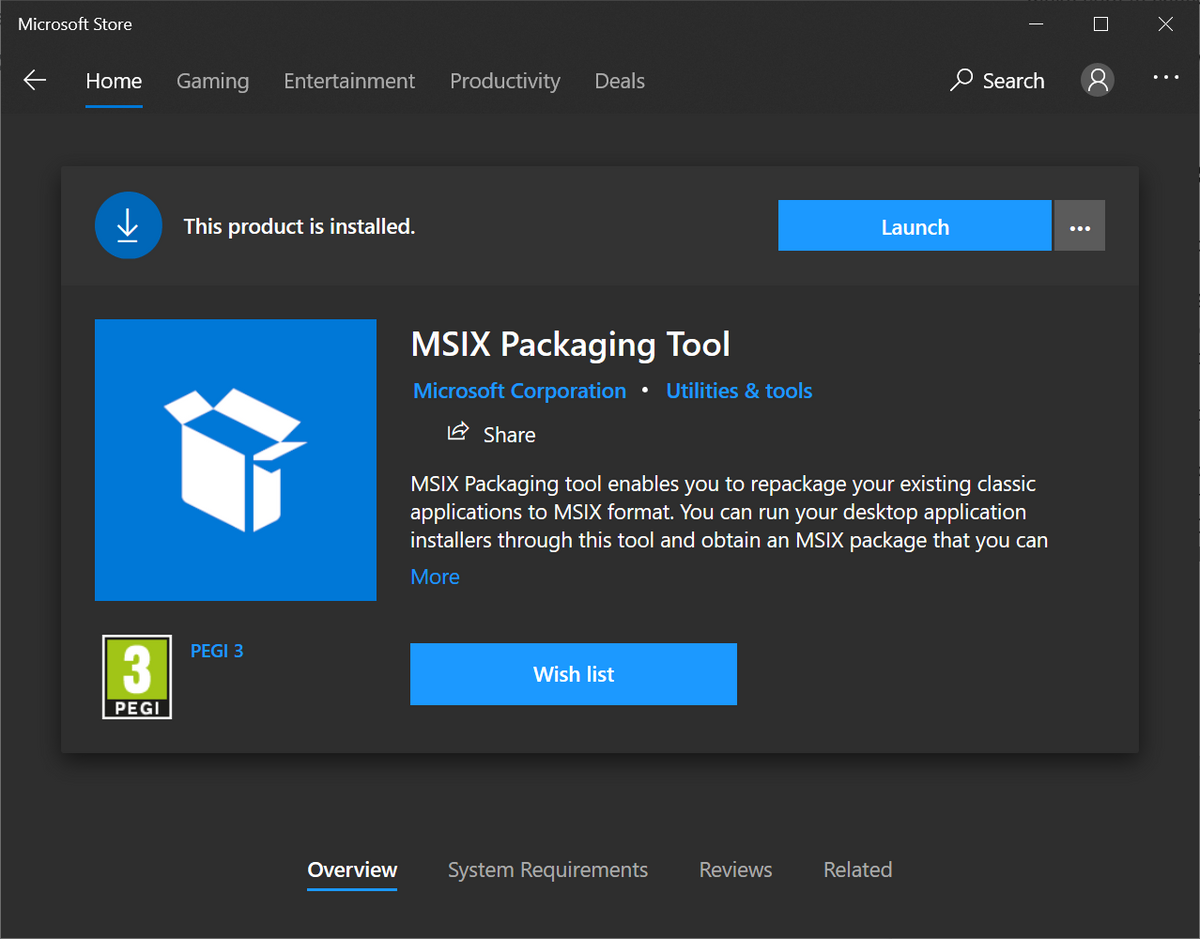
Microsoft Disables MSIX App Installer Protocol
Microsoft reportedly disabled MSIX installer protocol in Windows, due to its exploitation…
PUABundler:Win32/PiriformBundler
PUABundler:Win32/PiriformBundler is the detection of an unwanted program, developed and issued by…
Novice Rugmi Loader Delivers Various Spyware
The threat landscape meets a new player - Rugmi Loader. This threat…
Xamalicious Trojan Hits Over 327K Android Devices
A new Android backdoor, dubbed Xamalicious, was discovered by the researchers at…
Integris Health Hacked, Patients Receive Ransom Emails
Integris Health, Oklahoma's most extensive not-for-profit health network, fell victim to a…
Carbanak is Back with a New Spreading Tactic
The Carbanak cybercrime group, infamous for its banking malware, has resurfaced with…
What Should You Do When You Get Scammed?
As online scams become not only more widespread, but also more sophisticated,…