Confluence RCE Vulnerability Under Massive Exploitation
Researchers are seeing attempts to exploit a critical vulnerability in outdated Atlassian…
TikTok Shopping Scams On The Rise: Tips to Avoid
TikTok shopping scams is a new attack vector on online shoppers. Immense…
2 Citrix RCE Under Active Exploitation, CISA Notifies
CISA has given a timeframe of one to three weeks to fix…
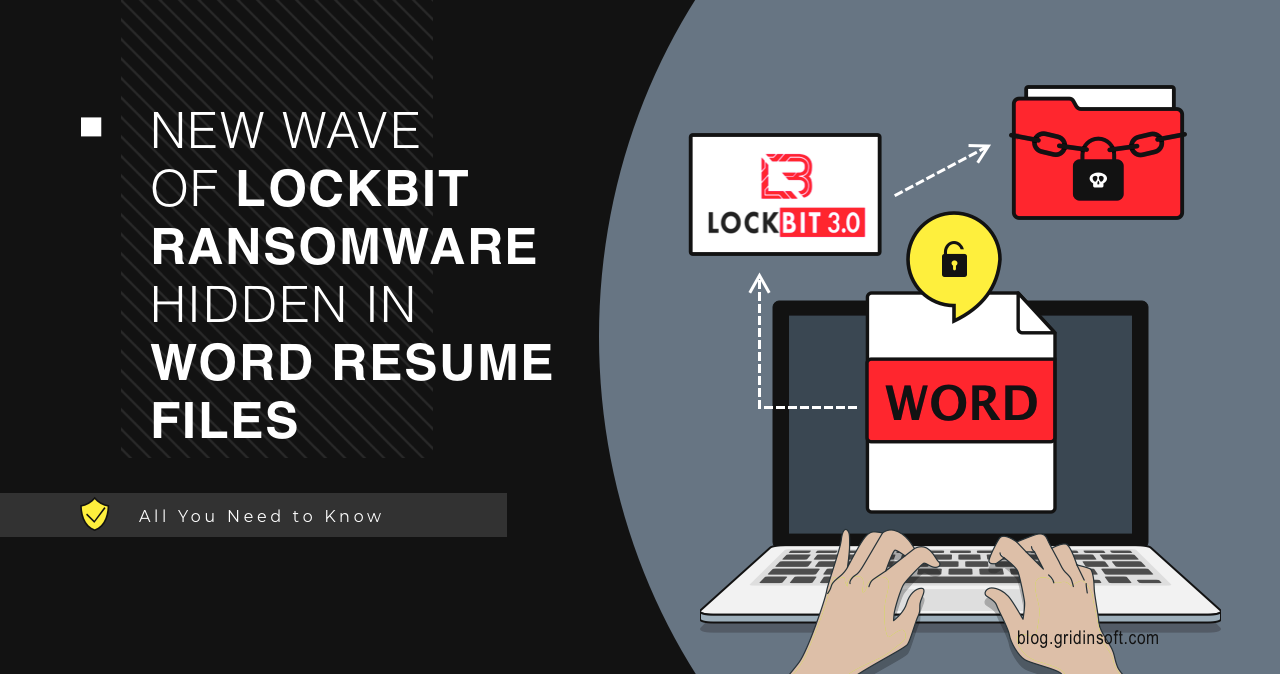
LockBit Ransomware Uses Resume Word Files to Spread
A recent investigation by ASEC reveals the new tactics of an infamous…
Over 178,000 SonicWall Firewalls are Vulnerable to DoS and RCE
Recent research uncovers a significant portion of SonicWall firewall instances being susceptible…
9 PixieFail Vulnerabilities Discovered in TianoCore’s EDK II
A chain of 9 vulnerabilities in UEFI’s Preboot Execution Environment (PXE), dubbed…
New Google Chrome 0-day Vulnerability Exploited, Update Now
In the most recent release notes, Google reports about a new 0-day…
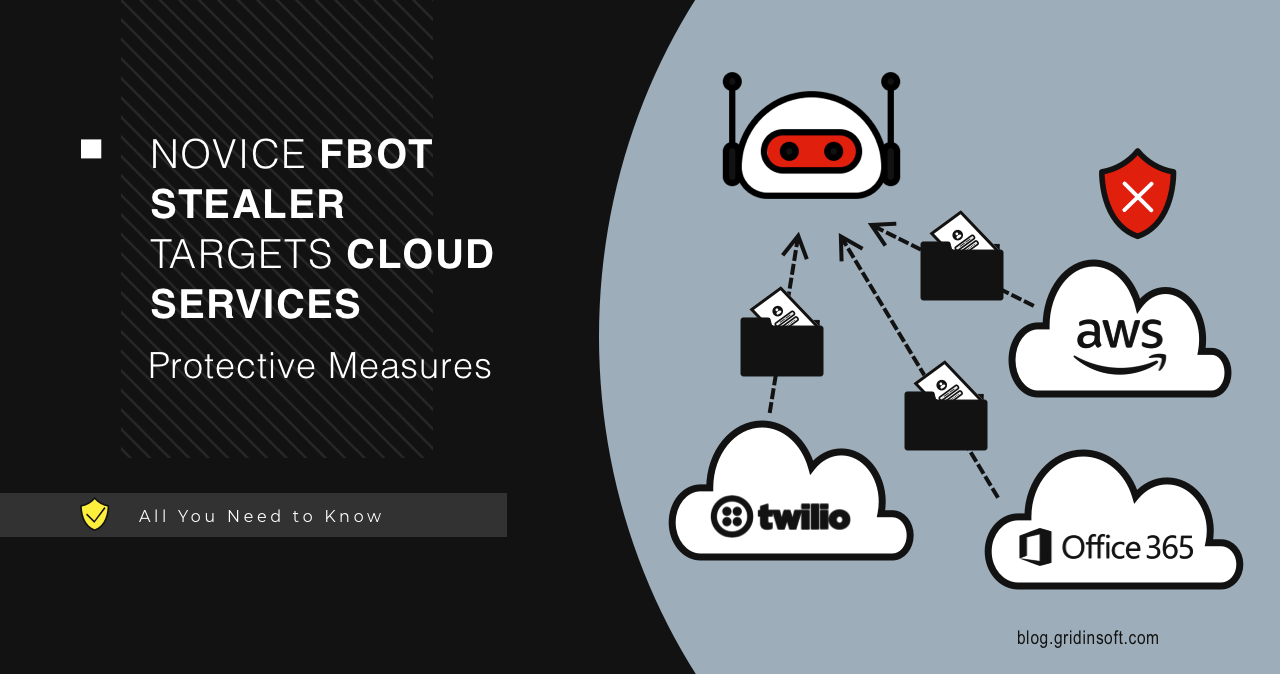
Novice FBot Stealer Targets Cloud Services
Researchers report about a new malware strain dubbed FBot. This Python-based malicious…
AzorUlt Stealer Is Back In Action, Uses Email Phishing
Cybersecurity experts have stumbled upon the eight-year-old Azorult malware. This malware steals…
Remcos RAT Targets South Korean Users Through Webhards
An infamous Remcos RAT reportedly started targeting South Korean users through the…
GitLab Zero-Click Account Hijack Vulnerability Revealed
On January 11, 2024, GitLab released an update with the official warning…
Windows SmartScreen Vulnerability Exploited to Spread Phemedrone Stealer
The malicious campaign exploits the CVE-2023-36025 vulnerability in Microsoft Windows Defender SmartScreen…