OpenMetadata Vulnerabilities Exploited to Abuse Kubernetes
Microsoft security blog reports that the OpenMetadata platform has critical vulnerabilities that…
MITRE NERVE Hacked, Service Taken Offline
MITRE reports about hacker activity in their NERVE network, spotted in April…
LabHost Phishing Service Taken Down by Police
Authorities have seized the LabHost phishing service, accused of stealing personal information…
Cisco Talos Warns of a Massive Brute Force Wave
The Cisco Talos security team has released information about a new campaign…
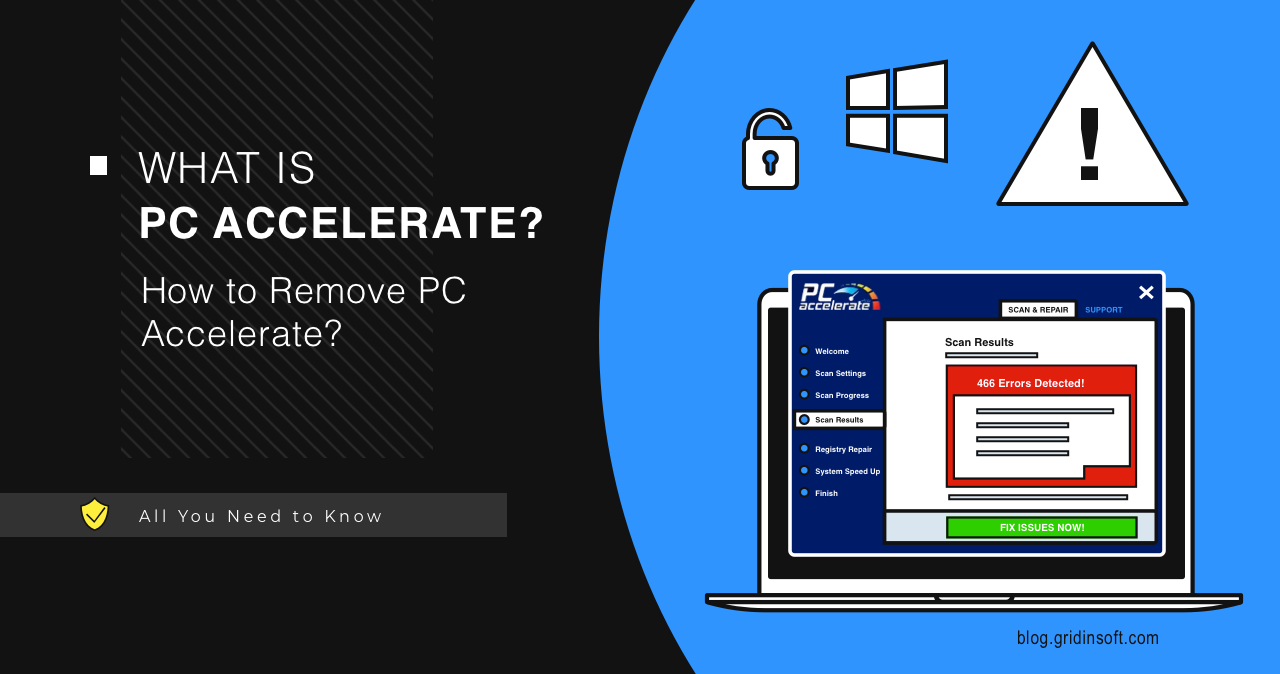
PC Accelerate
PC Accelerate is a questionable software that is presented as a useful…
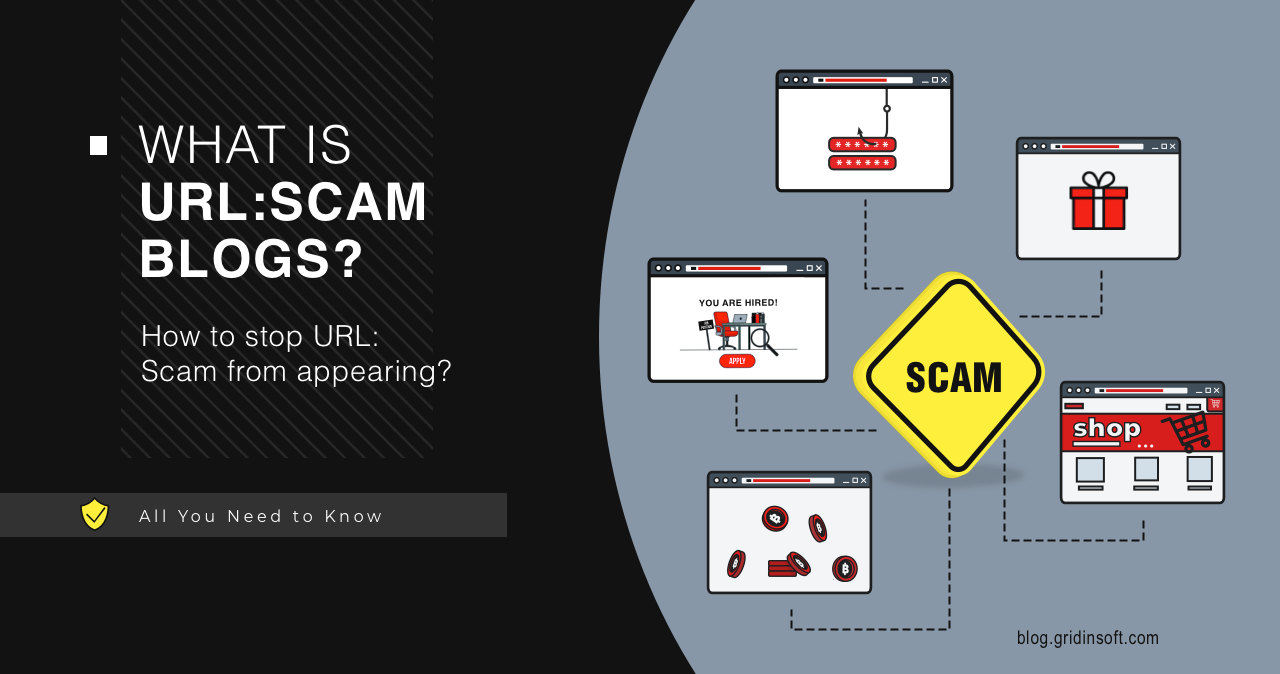
URL:Scam (Avast): Understanding This Detection and Securing Your System
The URL:Scam detection by Avast and AVG is a protective warning that…
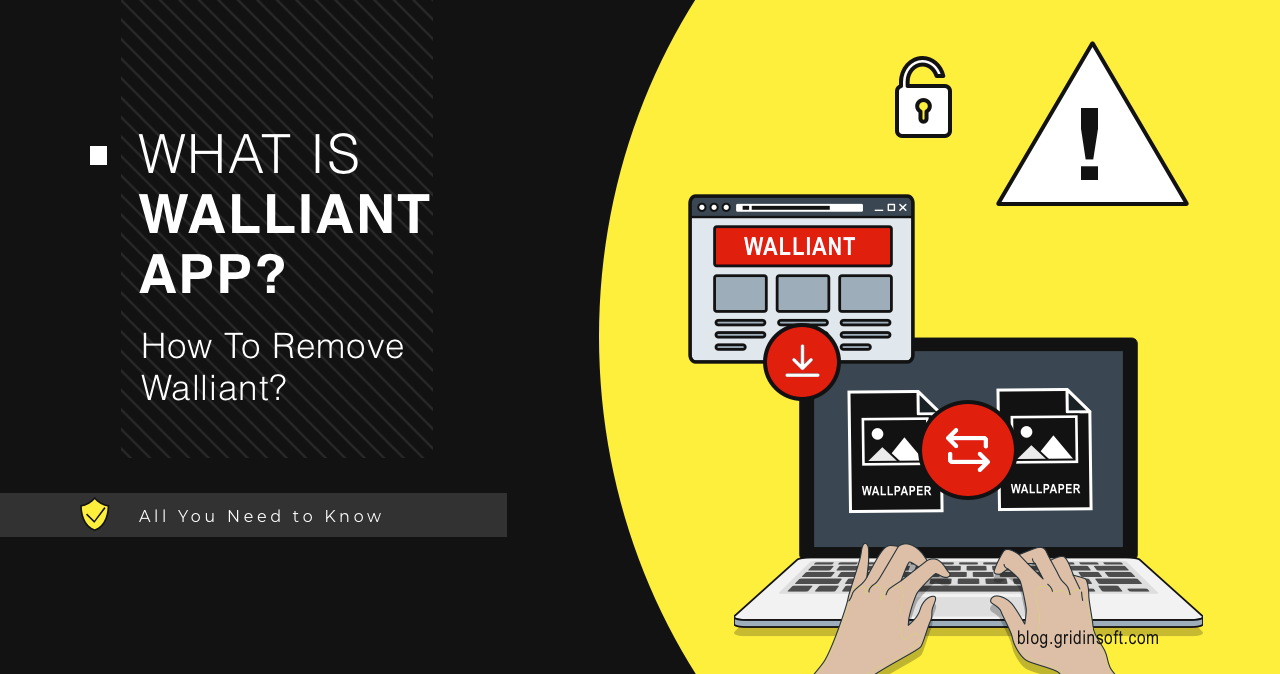
Walliant App
The Walliant application is a Potentially Unwanted Application (PUA). It is promoted…
Critical PAN-OS Command Injection Flaw Exploited
Palo Alto Networks warns its customers regarding a vulnerability in their PAN-OS,…
Fake Robux Generators Spread on Government Websites
Huge number of fake Robux generators recently appeared on a range of…
Critical LG TV Vulnerabilities Allow for Command Execution
LG reports fixing four critical vulnerabilities discovered in many of its TVs.…
Account restrictions are preventing this user from signing in
When working with Windows, users may sometimes encounter the "Account restrictions are…
SMApps Virus
SMApps is a malicious program that aims at spreading illegal promotions. It…