ThreatFabric analysts have discovered a new Android malware Alien. The malware primarily targets banking applications. Overall, Alien steals passwords and other credentials from 226 apps.
Alien is sold on hacker forums under the MaaS scheme (Malware-as-a-Service). At the same time, the malware was not developed from scratch, it is based on the source codes of the well-known banker Cerberus, which recently began to be distributed for free.
“Cerberus ceased to exist because the Google security team found a way to detect and clean up infected devices. Although Alien is based on the old version of Cerberus, it does not seem to have such problems and could become a full-fledged heir to the famous banker”, – said the Threat Fabric experts.
The researchers write that from a technical point of view, Alien can be called more advanced than Cerberus. Alien, for example, belongs to a new generation of banking Trojans that have integrated remote access functions into their code.
Thus, Alien can not only show the victim fake login screens and collect passwords from various applications and services, it can also provide hackers with remote access to infected devices so that they can use stolen credentials or perform other actions.
ThreatFabric experts report that most of the malware’s functions are used for fraudulent operations, because Alien operators, like most creators of modern Android Trojans, pursue financial gain. Alien is currently capable of:
- display content over other applications (used for phishing credentials);
- intercept data entered from the keyboard;
- provide remote access to the device (after installing TeamViewer);
- collect, send and forward SMS messages;
- to steal the list of contacts;
- collect device information and application lists;
- collect geolocation data;
- make USSD requests;
- redirect calls;
- install and run other applications;
- launch browsers, opening arbitrary pages in them;
- block the screen like a ransomware;
- follow up on notifications on your device;
- steal 2FA codes generated by authenticator applications.
The researchers’ analysis found that Alien could display fake login pages in 226 other apps in total. Most of the malware, of course, is interested in banking products, but besides them, Alien attacks email clients, social networks, instant messengers and cryptocurrencies (including Gmail, Facebook, Telegram, Twitter, Snapchat, WhatsApp, and so on). A complete list can be found in the company’s report.
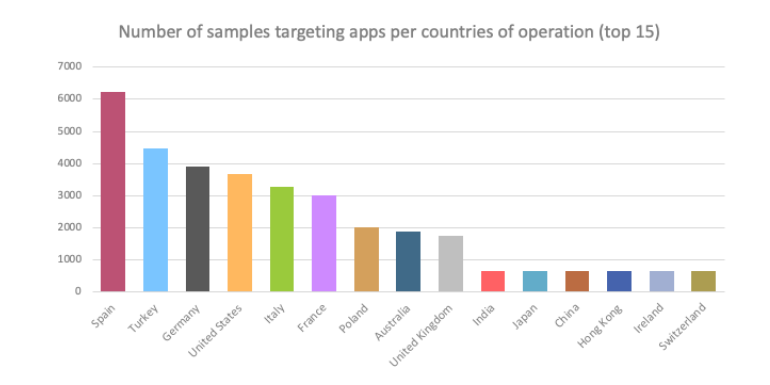
Most of the banking apps that Alien developers target are financial institutions from Spain, Turkey, Germany, USA, Italy, France, Poland, Australia, and the UK.
The ThreatFabric report is silent on how Alien gets to users’ devices, as delivery methods vary, depending on what Alien MaaS customers prefer. Sometimes such malicious applications even end up on Google Play, but in most cases they are distributed through other channels.
“Many of them seem to be spreading [Alien] through phishing sites, for example, a malicious page tricking victims into downloading fake software updates or fake coronavirus-related apps (a very common trick lately). Another method we have noticed is SMS messages: after infecting a device, hackers steal a contact list, which they then use to further spread their malicious campaign”, — ThreatFabric experts told ZDNet journalists.
In general, Alien-infected applications are easy to detect, as they usually require the user to grant them administrator rights or access to the Accessibility service.
Let me remind you that I also talked about the BlackRock Trojan that steals passwords and card data from 337 applications on Android OS.




