A research with Darknet monitoring utilities uncovered an active exploitation of a flaw present in Adobe Commerce (previously known as Magento). Quite a few versions of the software suite contain RCE vulnerability that potentially allow exfiltrating user data and manipulate page data. As there is no need for user/admin interaction for successful exploitation, it was expected to see the CVSS 9.8 rating.
Adobe Commerce/Magento Software Vulnerability Exploitation Uncovered
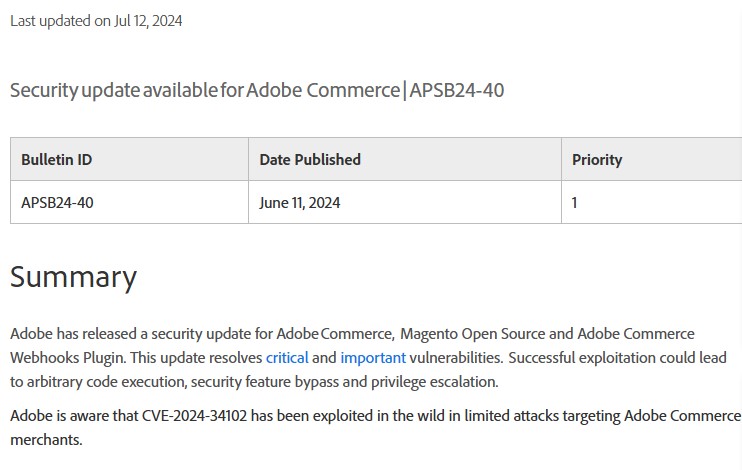
The original vulnerability, coded CVE-2024-34102, was discovered back in late June 2024, with all the corresponding reports and patches from Adobe. The description of the vulnerability clearly shows it is not too hard to exploit, which was reflected in the critical severity rating of 9.8. As all the required patches were released along with the vulnerability disclosure, the remediation steps were pretty straightforward.
But, as it usually happens, the disclosure of the vulnerability threw it into a spotlight of cybercriminals. As SOCRadar researchers discovered, 4275 online stores powered with Adobe Commerce were compromised, with the use of this exact flaw. That number is around 5% (!) of all online stores that use this software, and it keeps growing as hackers manage to retain the attack rate at 3-5 successful hacks per hour.
Among the most popular mischiefs that the researchers have noticed is setting up a skimmer at the checkout page. Once the visitor types the credit card data to pay for ordered items, the script that the hackers managed to embed with the use of this vulnerability will send all the data to the cybercriminals’ servers. It is also possible to facilitate stealing of other data types with the same exploit, as it allows modifying the final website’s interactive elements. The vast majority of these hacks appear automated, i.e. the exploit is simple enough and there are not many variable parameters that may require manual control.
The vulnerability itself falls under the CWE-611 designation – improper restriction of XML external entity reference. It is pretty self-explanatory: the program handles all URLs present in the XML documents as valid references, which eventually allows it to manipulate the output. As XMLs are essential for web development, the potential attack surface effectively extends to the entirety of Adobe Commerce user base.
Adobe Commerce CosmicSting Vulnerability Fix
As I’ve mentioned above, Adobe released the fix simultaneously with the disclosure of this vulnerability. That gives an obvious fix advice: just install the latest updates for Adobe Commerce, and you’re good to go. The following versions are known to contain the vulnerability, according to the original Adobe report:
2.4.4-p8
2.4.5-p7
2.4.6-p5
2.4.7 and earlier
Another advice that Adobe recommends all customers to apply is changing the secret encryption keys. This is needed to prevent the hackers from using potentially leaked ones, so it is also important to ensure that old encryption keys are invalidated.
Researchers from Sansec also offer a temporary fix, that should be enough to prevent exploitation until it is possible to install the proper update. To do this, they offer administrators to block all the requests to the CMS block API, a part that is getting manipulated during the attack. As it won’t take any new requests, adversaries won’t be able to create the aforementioned checkout skimmers and do other mischiefs.





