Acronis, a Swiss-based information technology company that provides file recovery services for hacked companies was breached earlier this month. The breach became public on March 9, 2023, when a hacker published a leak at one of the Darknet forums.
Acronis Breach Exposes Numerous Internal Data Packages
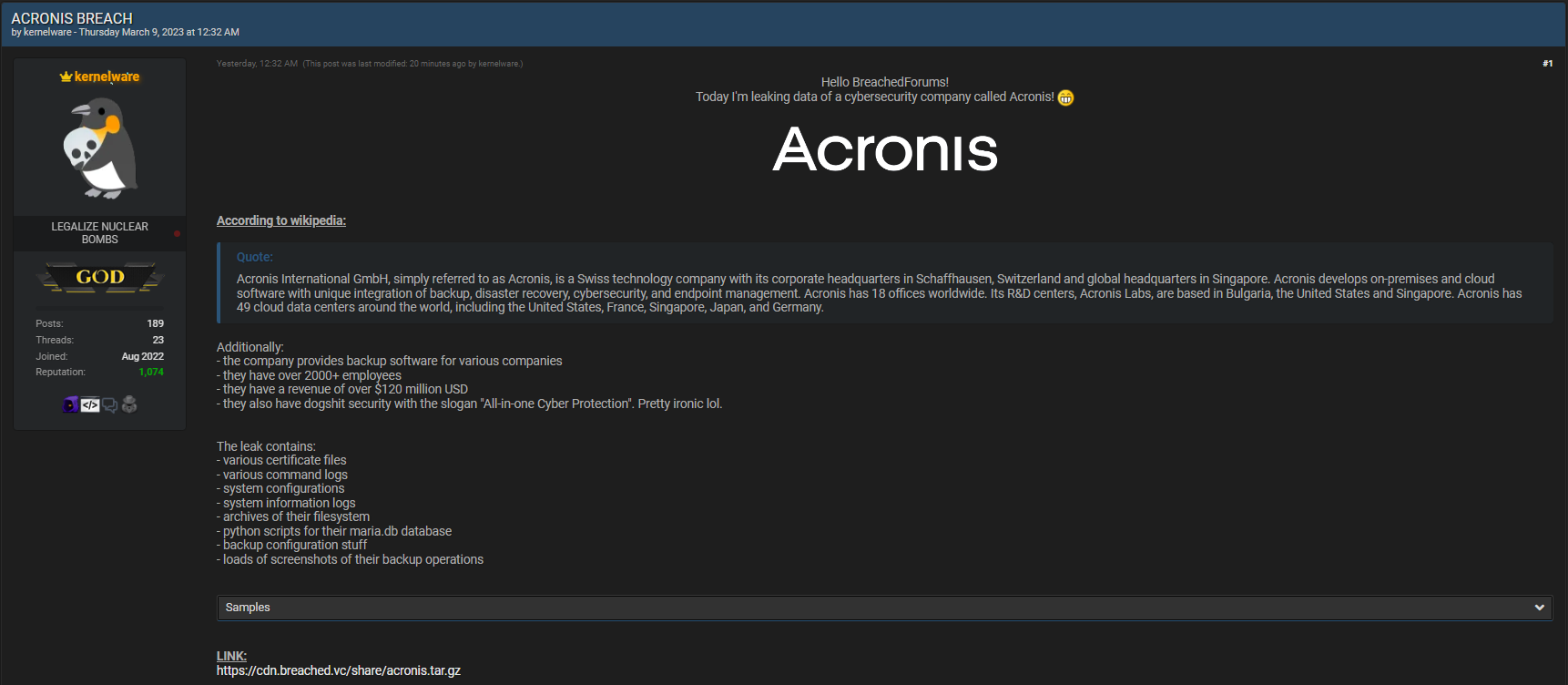
Actually, attacking the companies that help other ones to recover after cyber attacks in that or another manner is not a new thing. It has a slight touch of revenge – for making the victim pay less than hackers were estimating. However, this is most probably a different case, as no public ransom was claimed, as well as worldwide disclosure as it happened during attacks on Kaseya or FireEye. In its forum post, the crook shares that he succeeded at leaking “various certificate files, command and system info logs, system configs, python scripts for their maria.db database” and a row of other things.
Soon enough, at least compared to the recent Acer breach, Acronis claimed that no client data was exposed. The company also specified that none of their products were struck as well, meaning that only internal documents were leaked. This, however, does not show the real scale of a problem, both with overall security within the company and the amount of data the intruder may have access to. A bitter comment upon the security solution they use made by the forum post author just emphasises that unanswered question.
For transparency, the specific credentials used by only one customer to upload diagnostic data to an Acronis file server was compromised, no Acronis products have been affected. Our customer service team is currently working with this customer. Updates to follow as needed.
— Acronis (@Acronis) March 9, 2023
How dangerous is the breach?
At a glance, that breach may look pretty drub and non-informative. And it mostly is when we look only at the table of contents. The details that may be revealed by analysing the leaked information can give other hackers enough information to plan a new attack. Cybercriminals who spread malware that, actually, causes the companies to call for Acronis’ help, may adjust their payloads in this manner so it will not be possible to use the tools they have developed and used. Moreover, exposing the “loads of screenshots of their backup operations” may probably disclose their clients. That includes emergency ones and companies that are not happy to share the fact that they were hacked. Still, all the details are to come, as even the company is still investigating what exactly happened.