Researchers detected another IoT botnet based off of Mirai malware source code, that now leverages a newly-discovered vulnerability in Four-Faith routers. The botnet started back in early 2024, dubbing itself with a rather offensive name “Gayfemboy”, yet this did not hinder its rapid growth due to the successful exploitation of the flaw.
GayFemboy Mirai Botnet Exploits Four-Faith Flaw
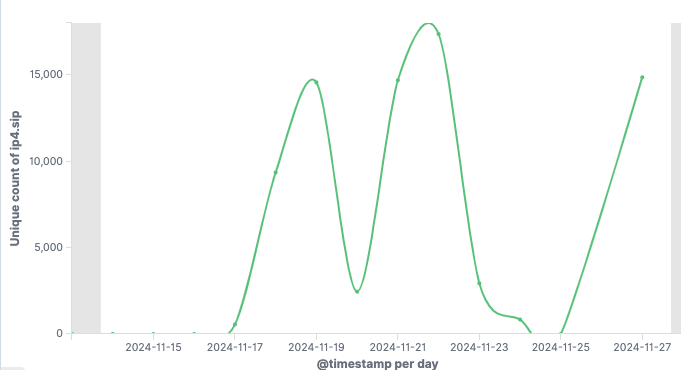
Over the course of its activity, the botnet of an unconventional naming has used plenty of vulnerabilities, which makes it stand out from the rest of Mirai-based backdoors. Researchers from X Lab hold a record of a grand total of 20 flaws used over its activity span. The flaw in Four-Faith routers has given a major boost in activity for that malware, as may be seen for the graphic below.
Mirai itself, and almost all the malware based on its source code, targets IoT devices to form botnets. Further, the network of infected devices is put for rent on the Darknet. Hackers may use it for all kinds of purposes – from mining cryptocurrencies to launching DDoS attacks or massive spam mailing.
The last wave of activity of the botnet started in November 2024, right when the vulnerability in the industrial routers was found. Malware spreading generally targets the US, China, Iran and Russia – a rather unusual geographics, considering that threats typically target only countries from one political camp. DDoS attacks that this botnet performs target almost exclusively the US of A and China.
To gain insight into its operations, the researchers have established several command servers and started calling out known botnet IP addresses. This was needed to observe the behavior of infected devices and get a rough estimate of the botnet’s scale. The observations revealed that Gayfemboy has more than 15,000 daily active nodes and operates through over 40 active groups.
One particularly notable finding was the botnet’s retaliatory behavior. Upon detecting that one of the command servers was under control of malware analysts, the network hailed a DDoS attack against them.
What is CVE-2024-12856 Vulnerability?
The flaw detected in Four-Faith industrial routers is one of a few 0-day vulnerabilities, discovered in 2024. It allows attackers to inject and execute the code into the firmware of the router. One of the most prominent use cases for such a security hole is to make the router connect the remote server, download the payload and execute it.
Sure enough, it cannot go any further than this: the router becomes infected, but it is not really possible to make it pass the malicious payload to the devices within the network. The only exception is other routers, as they may exchange packets and perform other communications, depending on network configurations. Nonetheless, there is a solid application for routers and overall IoT devices in botnets.
Protection Against New Mirai Botnet and Vulnerability Exploitation
The main problem is that there is no fix available for the Four-Faith routers’ flaw. The vendor of the network hardware is due analysing the vulnerability and releasing a firmware update. And, even with the update released, it should get installed to the devices – which is not trivial considering the area these routers are used in.
For now, security analysts only name indicators of compromise and suggest classic ways of removing the threat. As this malware is another Mirai offspring, the removal process is well-known and has been tested a lot over the years.
Unplug the router or another device from the network, in order to prevent any further infections. Then, reset it to factory settings, which should wipe out the malware. After that, set it up as usual but with adding a TCP port 23 closed. Analysts also recommend keeping the Telnet service disabled as well. Changing device management page passwords to stronger ones is another step that will prevent further attacks, and not only from Mirai malware.





